The Zscaler ThreatLabZ team has detected a rise in Java-based remote access Trojan variants — jRATs — which give attackers a backdoor into a victim's system and can be capable of remotely taking control of the system once it's infected. Malware authors are using numerous tactics to entice unsuspecting users to open infected attachments, which arrive as malicious JAR files. Most recently, we’ve seen filenames such as “IRS Updates.jar” and “Important_PDF.jar,” claiming to contain important tax deadline information from the IRS. We’ve also identified JAR files claiming to be purchase orders or other important documents. When a user opens the file thinking it is an actual communication from the IRS, or said party, the jRAT payload gets installed on the user’s machine.
We have seen numerous jRAT instances using the following filenames in the past two weeks:
- Important_PDF.jar
- IRS UPDATES.jar
- IRS UPDATE1.jar
- PO#(7 Digits).jar
- Invoice_TS4009653.jar
- DHL_MQ00546_INV_BL_PL_output913C0bb2F_PDF.jar.jar
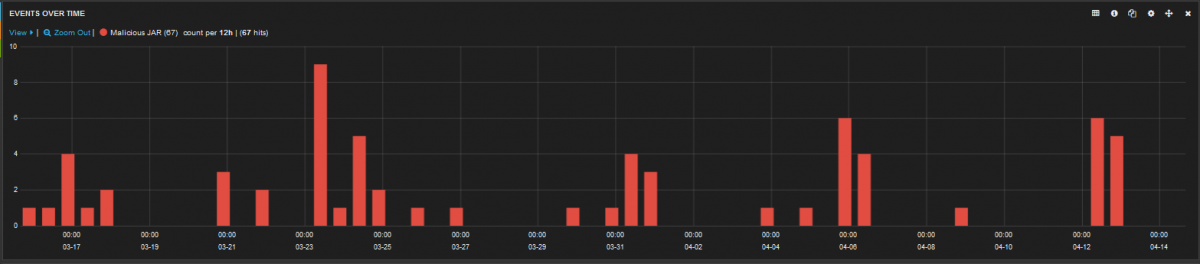
Figure 1: jRAT instances blocked in last two weeks
The jRAT sample that we analyzed for this report was obfuscated with three layers of packing. On execution, the malicious JAR file drops a VBS file in the %APPDATA% folder on the user's machine. The dropped VBS files are named “Retrive
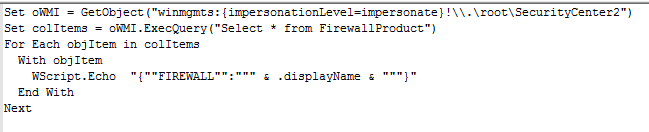
Figure 2: Script to check for firewall presence
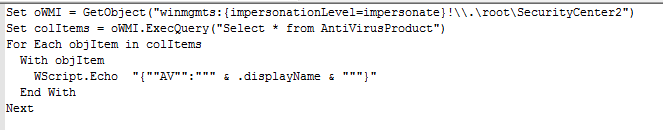
Figure 3: Script to check for AV presence
After passing these initial checks, it drops a JAR file in the Temp folder with a ".class" extension and executes it.
The JAR file dropped, as seen in the image below, is just a dropper and decrypter for the main jRAT file. It basically contains the jRAT sample in an encrypted form. The encryption of the file is done by an embedded AES key, which is again encrypted using an RSA key. The decrypter for this file has been written by hasherezade of MalwareBytes.
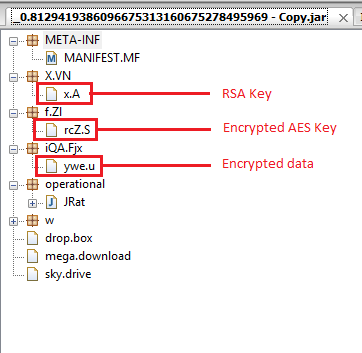
Figure 4: Encrypted data and keys in the JAR file
The jRAT code is written in a very modular way, segregating different functionalities in different packages. The image below demonstrates the level of obfuscation used by the author to make it difficult to decompile and understand the code.
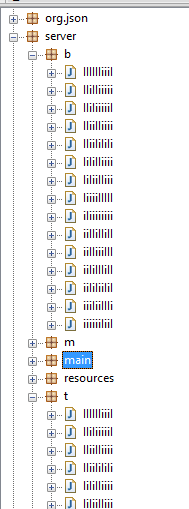
Figure 5: Obfuscated class files in jRAT source code
In our sample, there was an encrypted configuration file that contains details for the bot to communicate with the Command & Control (C&C) server.
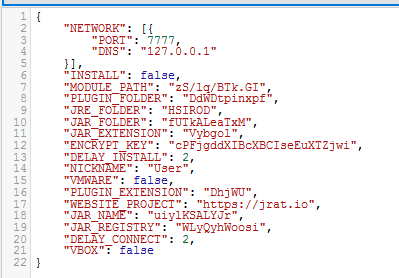
Figure: 6: Decrypted bot configuration file
The jRAT payload is capable of receiving commands from a C&C server, downloading and executing arbitrary payloads on the victim's machine. It also has the ability to spy on the victim by silently activating the camera and taking pictures.
For persistence, the sample creates an autostart registry entry to launch itself upon system reboot.
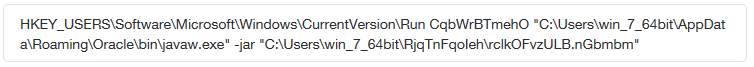
Figure 7: Autostart registry entry
The malware connects to a hardcoded URL to download malicious executable files. In case of the sample analyzed in this blog, the following URL was contacted:
- workfromhomeplc[.]ru/dmp/PO%233555460.exe
At the time of analysis, the URL was not active, but the site has a known history of hosting the Loki information-stealing bot.
Malware continues to draw in unsuspecting victims by using current issues and relevant events of the day to capture people's attention and interest. With one click, users can become victims, making themselves and their corporate networks vulnerable to attack by malicious payloads. The image below shows the full detonation of this malicious jRAT payload in the Zscaler Cloud Sandbox environment, capturing all its activity.
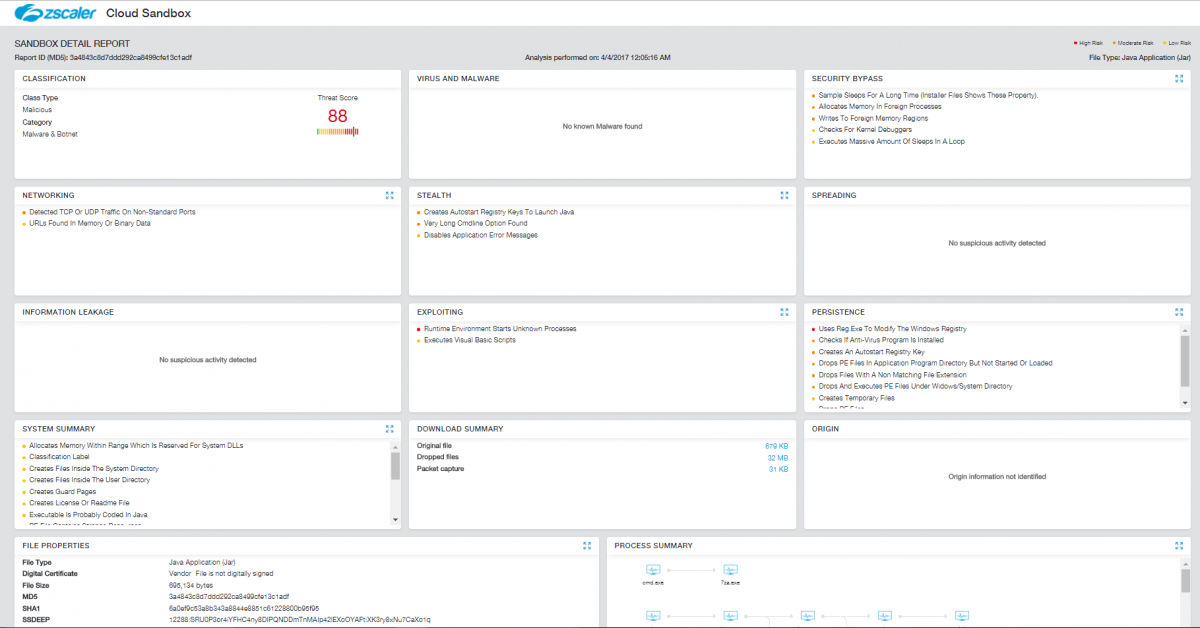
Figure 8: Zscaler Cloud Sandbox report showing all suspicious activities
Research by - Sameer Patil and Jithin Nair.




