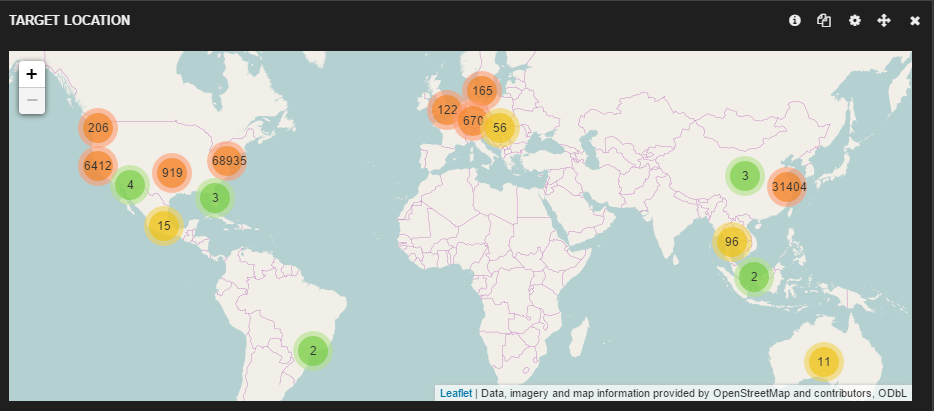
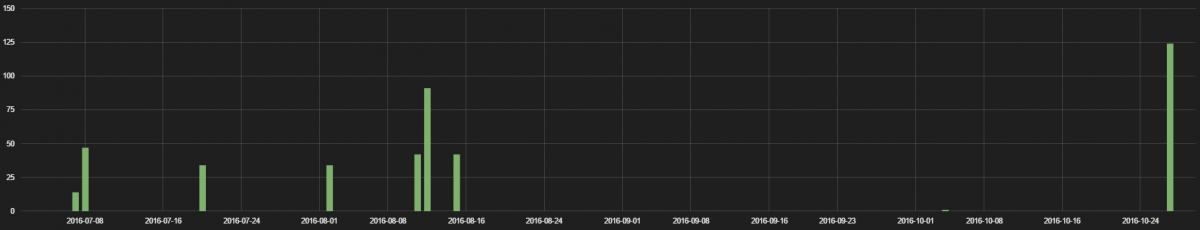
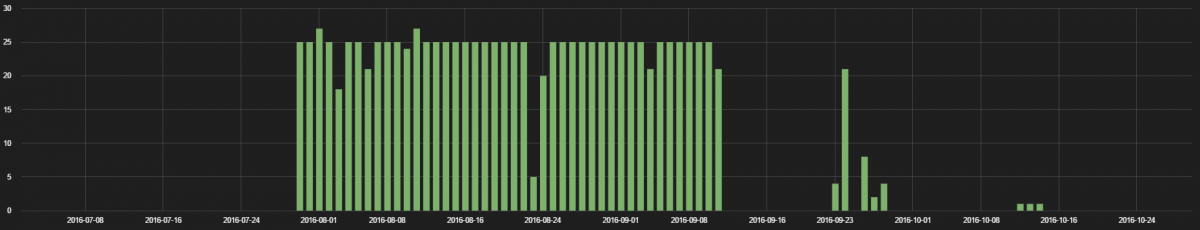
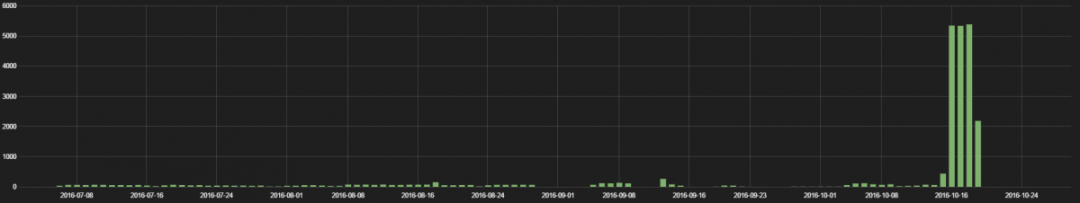
In the months prior to the recent attacks, which used Internet of things (IoT) devices to carry out massive distributed-denial-of-service (DDoS) attacks, the ThreatLabZ research team had begun studying the use of IoT devices on the networks of Zscaler customers.
In light of their notoriously poor security, we knew that IoT devices were relatively easy to compromise, so there’s been concern over the potential to use them for spreading malware, stealing credentials, leaking data, sniffing traffic, or even moving laterally on a network to scan for sensitive data. The devices themselves can also be exploited for malicious purposes, such as spying in the case of cameras. Or, as we saw last month, creating large, destructive botnets.
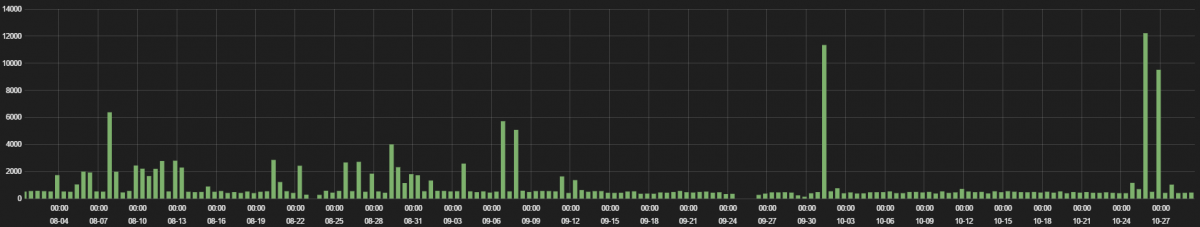
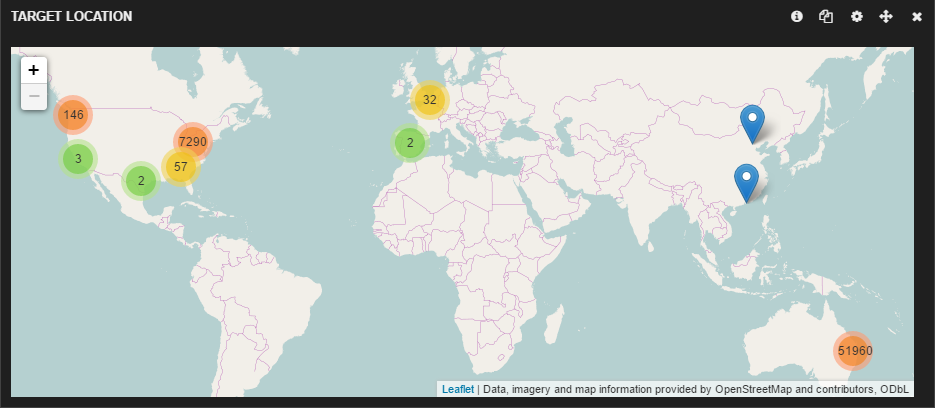
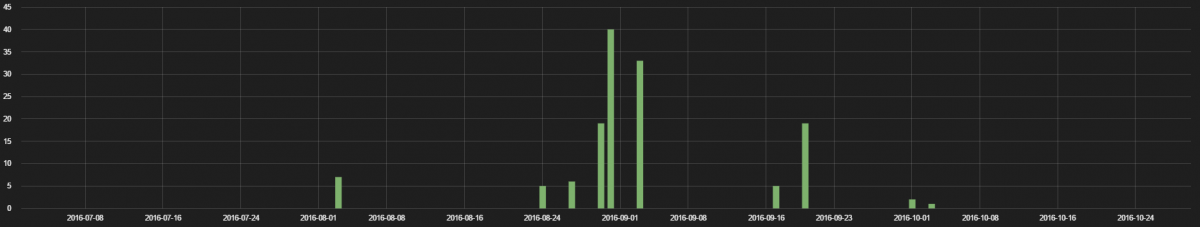
We analyzed data going back to July for recent IoT device footprints based on the traffic we are seeing in the Zscaler cloud. We looked at the types of devices in use, the protocols they used, the locations of the servers with which they communicated, and the frequency of their inbound and outbound communications over a two-month period (26 August 2016 to 26 October 2016). Our primary purpose was to determine if any of the devices posed a threat to customer security, and eventually we also looked at whether the devices that were used in the Dyn and KrebsOnSecurity attacks were also in use by our customers.
Finally, we analyzed IoT traffic patterns on the days of the DDoS attacks to see if there had been any unusual behavior on those days, such as spikes in bandwidth use or variations in the destination of IoT traffic.
What we found
The most common devices we saw were cameras, home entertainment systems, printers, and IP phones. Many of the devices we observed were still using plain-text HTTP protocol for authentication as well as firmware updates, which makes their communication vulnerable to sniffing and Man-in-The-Middle (MiTM) attacks.
What we didn’t find
An analysis of the IoT traffic on the attack days did not show traffic spikes that would indicate that any of the devices had been compromised. Therefore, we do not believe that any of our customers’ devices were involved in either botnet. Mirai, the malware responsible for the recent attacks, uses the Telnet and SSH protocols to infect devices. But most enterprises will not allow inbound open external access over these protocols, whereas access over HTTP and HTTPS are more common. While there are many devices on our customers’ networks that are similar to those used in the attacks, none of them appeared to be compromised or involved in the recent attacks based on our research.
What follows is a presentation of our findings. At the end of the report, we will present some questions and answers about IoT devices, protecting your organization from potential threats, and what to do if you believe a device has been compromised.
Zscaler Cloud – Enterprise IoT traffic research
For this report, we have grouped the IoT devices based on their functionality.
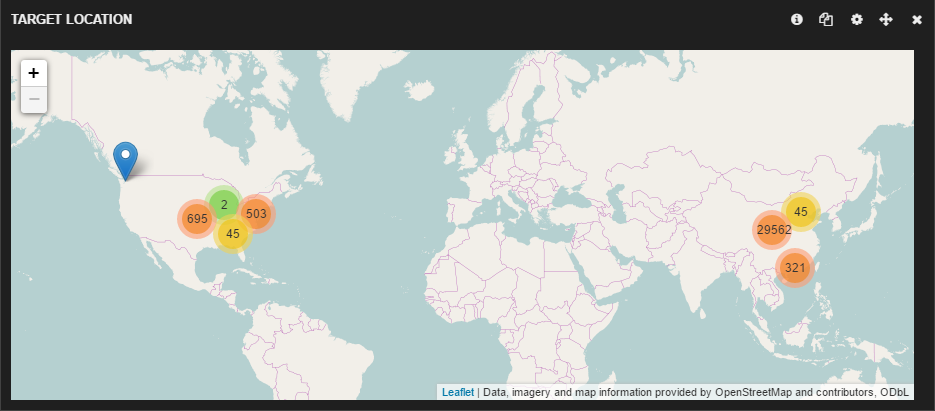
Video Monitoring & Surveillance Cameras
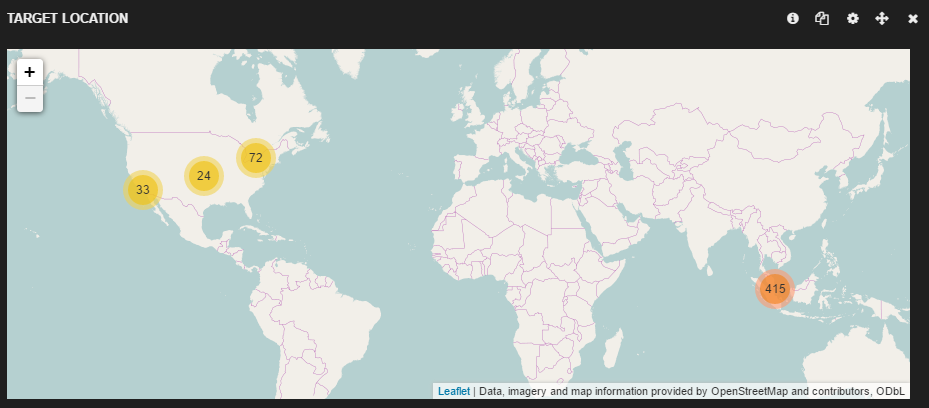
Geographic distribution of servers with which these devices are communicating:
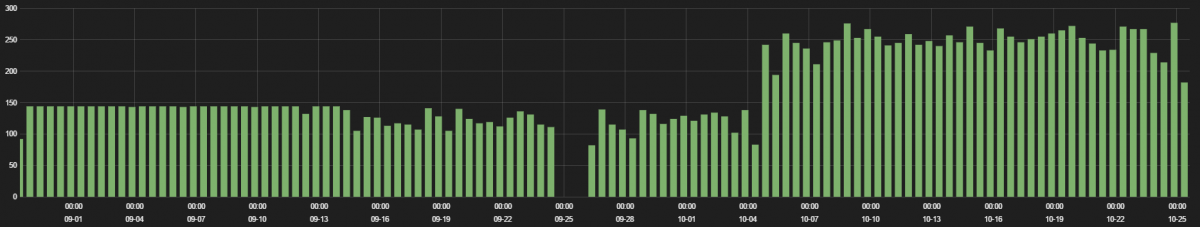
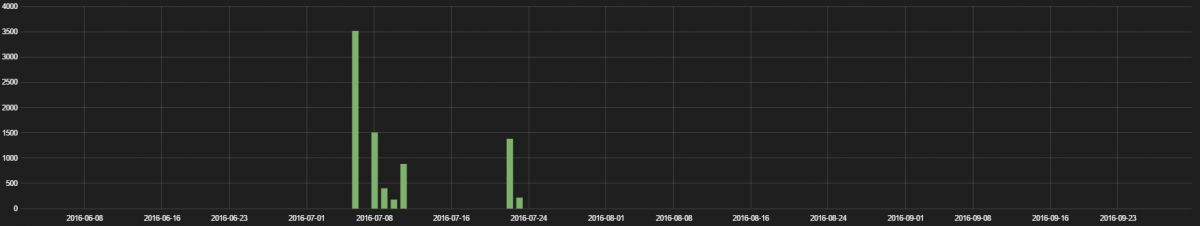
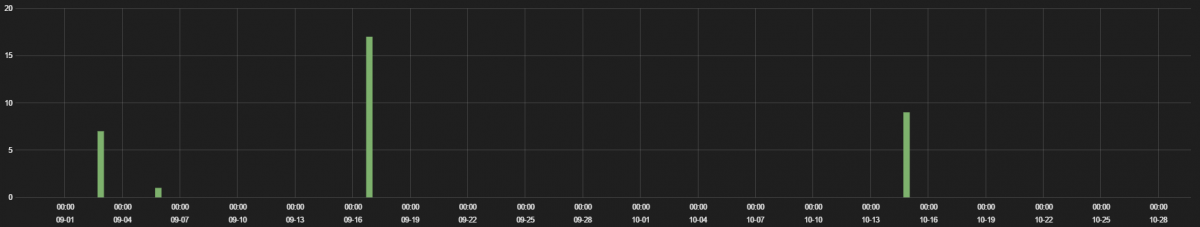
1. Flir FX wireless HD monitoring camera

The FLIR FX™ is a wireless HD camera that allows you to see the day in a minute and keep an eye on the things you care about. We observed multiple Flir FX devices connecting to FLIR services servers on a regular basis.
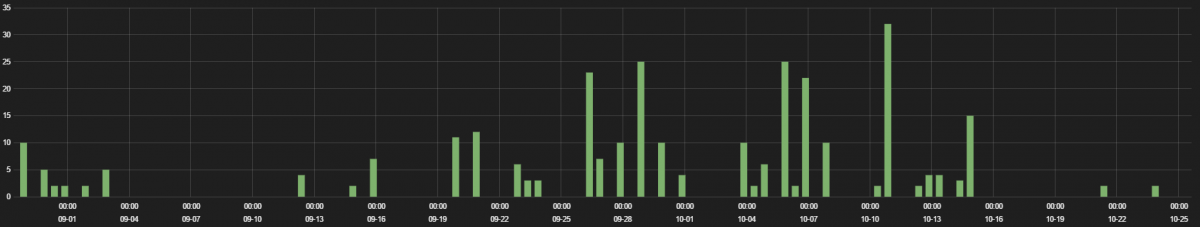
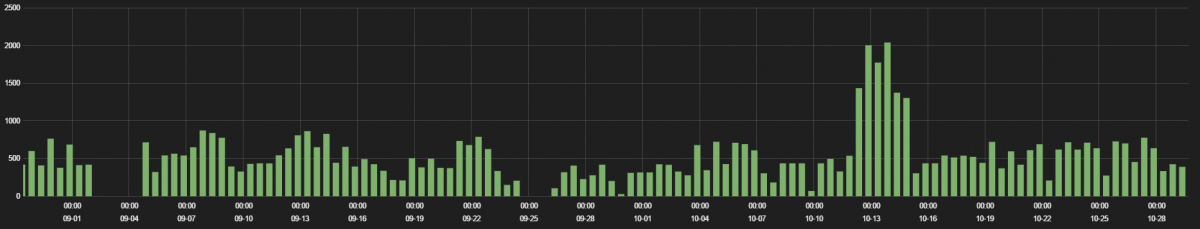
The traffic hits are displayed in the following graph.
Security concerns:
This device was found to be communicating over plain-text HTTP with the FLIR services server for firmware updates without any authentication tokens.
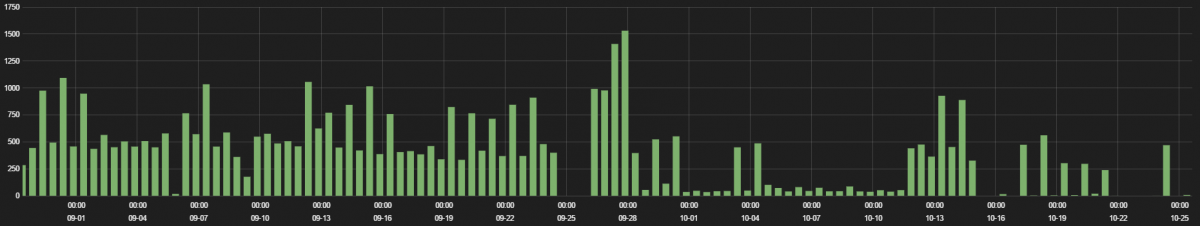
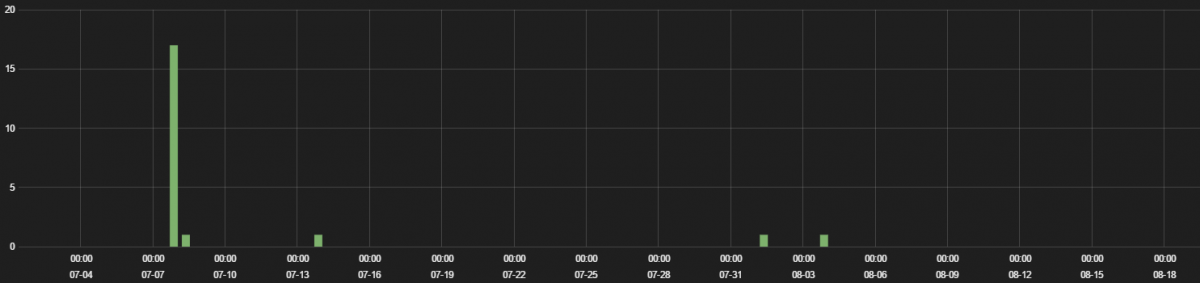
2. Canary Home Security System

Canary Home security system is an all-in-one security system which can stream real-time video of your home and has features like, built-in siren, motion-activated recording, HomeHealth Technology and Intelligent notifications.
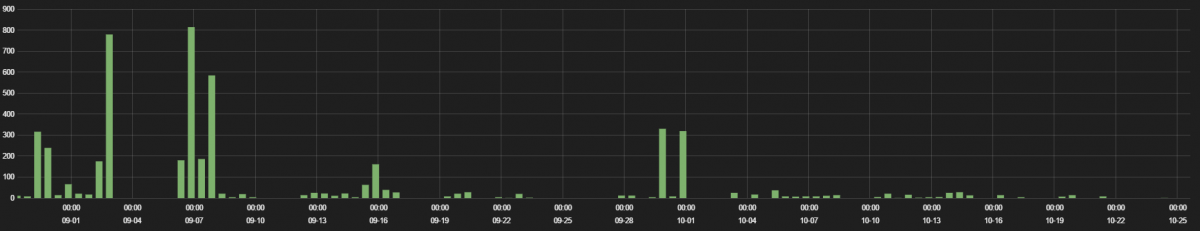
The traffic hits are displayed in the following graph.
Security concerns:
None
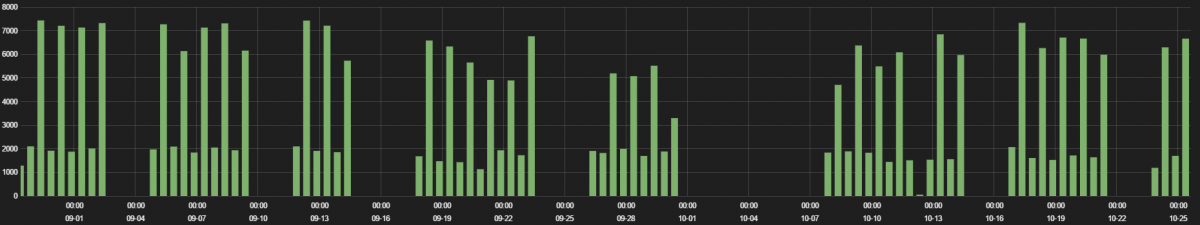
3. Foscam

Foscam is a IP surveillance camera with ability to remote pan/tilt. It connects to a web server to stream video to desktop or smartphone from anywhere on local network or over the Internet.
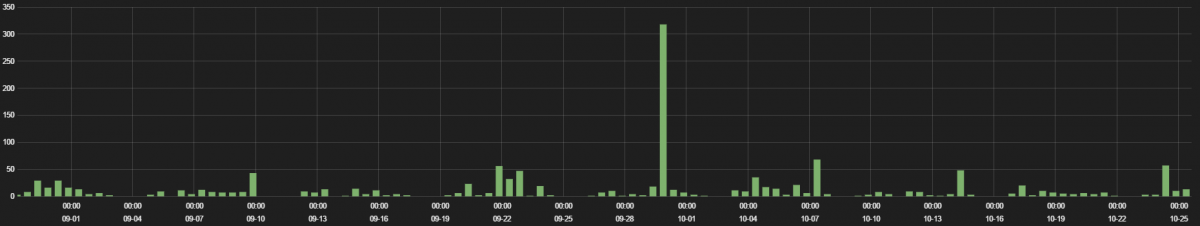
The traffic hits are displayed in the following graph.
Security concerns:
This device was leaking user credential information over HTTP in the URI. For example,
xxx.xxx.xxx.xxx:yyy/snapshot.cgi?cmd=snapPicture&user=admin&pwd=password
4. Dahua DH Security Camera

Dahua DH Security Cameras are networked IP cameras that allow video surveillance over the internet. Dahua Technology is one of the leading product and solution provider in the global video surveillance industry.
The traffic hits are displayed in the following graph.
Security concerns:
Weak default credentials and communication over HTTP makes the communication susceptible to sniffing and MiTM attacks.
5. Axis Camera

Axis designs cameras to cover a variety of application needs, from robust outdoor cameras for harsh climates, to discrete products for sensitive environments. We observed communication from networked Axis IP cameras.
The traffic hits are displayed in the following graph.
Security concerns:
We found the remote management console of the camera to be using basic HTTP based authentication, which makes the communication susceptible to sniffing and MiTM attacks.
Smart TVs and Entertainment devices
Geographic distribution of servers with which these devices are communicating:
1. Haier Android TV
 .
.
Haier Android TV is smart TV which integrates Internet and interactive “Web 2.0” features. It connects to the internet to provide host of features like streaming video content to web connected apps to provide a technological convergence between computers, flat screen television sets and set-top boxes.
The traffic hits are displayed in the following graph.
Security Concerns:
The security concern with respect to smart TVs in general is the use of outdated libraries which could be exploited to gain control over the system.
2. Chromecast media player

Chromecast media player is a streaming device by google that plugs into HDMI port of TV. It allows streaming content from mobile devices like iPhone, iPad, Android phones, and various laptops.
The traffic hits are displayed in the following graph.
Security concerns:
None
3. Roku streaming TV and media player

Roku is a streaming device which allows streaming movies, TV shows, live sports, news and music to TV. It allows users to connect to paid content providers and stream contents from them.
The traffic hits are displayed in the following graph.
Security concerns:
None
Smart Network Printers & Scanners
Geographic distribution of servers with which these devices are communicating:
1. Epson Printer

The Epson printer is a wireless/wired connectivity printer designed for home office environment. It allows to print sharp, professional-quality documents from desktop, iPad, iPhone, Android tablets or smartphones.
The traffic hits are displayed in the following graph.
Security concerns:
None
2. HP Designjet Printers

HP Designjet printers are easy to use large-format printers which are web-connected to allow prints from anywhere over the internet.
The traffic hits are displayed in the following graph.
Security Concerns:
None
3. Fuji Xerox Printer

Fuji Xerox printers are networked printers which are designed for high print performance and have a host of powerful productivity tools designed to make daily office tasks more efficient.
The traffic hits are displayed in the following graph.
Security concerns:
We observed print monitors connecting to maintenance logging modules without any authentication.
UPDATE:
We were informed by Fuji Xerox authorized dealer at Fuji Xerox Business Center Toowoomba that the communication that we were seeing was unencrypted traffic being sent to a non SSL based management platform, and they have initiated change request to move the service to a SSL platform so that the communication is secure. It is important to note that the maintenance/logging module is NOT a Fuji Xerox product and is not authorized by Fuji Xerox.
Network printers are usually installed and setup in a way to make them reachable by most users on the internal networks. It is important to ensure that these printers are running the latest security patches by keeping the firmware up to date.
Digital & Network Video Recording systems (DVR/NVR)
Geographic distribution of the servers with which these devices are communicating:
1. VideoEdge NVR

VideoEdge NVR is a powerful NVR system which can be used to manage surveillance in active environments, onsite and remotely. Using a victor client with VideoEdge allows high-performance video streaming, audio, motion metadata.
The traffic hits are displayed in the following graph.
Security concerns:
Weak default credentials and communication over HTTP makes the communication susceptible to sniffing and MiTM attacks.
2. D-Link DNR-202L

D-Link DNR is a Camera Recorder to simultaneously stream, record and playback upto 4 D-Link Wi-Fi camera to provide home or small business security.
The traffic hits are displayed in the following graph.
Security concerns:
Weak default credentials and communication over HTTP makes the communication susceptible to sniffing and MiTM attacks.
IP Phones
Geographic distribution of the servers with which these devices are communicating:
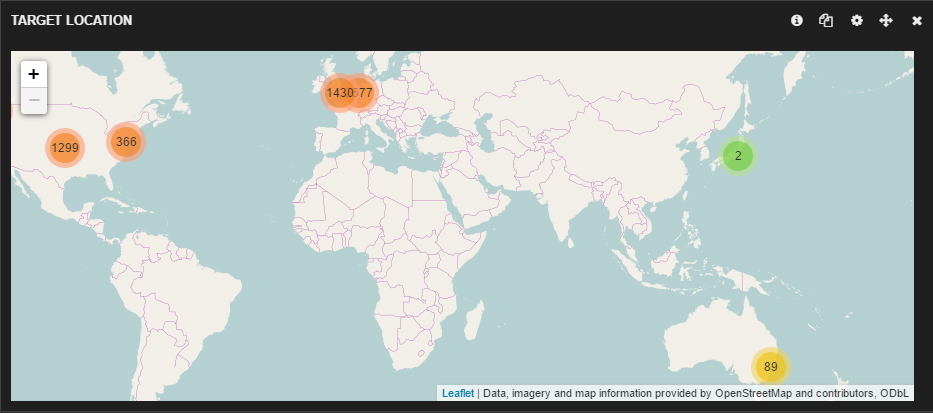
1. Panasonic KX-TGP500B04

The Panasonic KX-TGP500B04 is a DECT solution which includes base unit and a DECT cordless handset. It enables the users to use range of services provided by the carrier such as Call Forward, Voice Mail etc. This system can also be used as a wireless terminal.
The traffic hits are displayed in the following graph.
Security concerns:
These devices were found to be downloading a root certificate as well as performing authentication over plain-text HTTP protocol making them vulnerable to sniffing and MiTM attacks.
2. Yealink SIP phones-T46G

The Yealink SIP-T46G IP phones are designed for executive users and professionals. They make use of Yealink Optimal HD technology to deliver clear, life-like voice communications with features like Gigabit Ethernet, variety of device connections and programmable keys.
The traffic hits are displayed in the following graph.
Security concerns:
These devices were found to be using basic HTTP authentication.
IoT in the enterprise
IoT devices present a unique threat, because of their minimal security and their sheer numbers.The Mirai malware has shown us how these devices can wreak widespread havoc through targeted DDoS attacks. But what else do we need to know about these devices? Are there some that should be banned from the enterprise? What do we tell employees who are bringing them from home?
What follows is a brief Q&A to help you form your policies around the use of IoT devices in your organization.
1. How would you know if your device was used in an attack, like the one on Dyn?
You probably wouldn’t. If a device is used in an attack while in the enterprise, you would likely see a spike in traffic and abnormality in the traffic destination, as the device bombards the victim. If there are many devices involved, their high bandwidth use would slow your overall traffic.
2. What can people do if they think their devices were used in an attack?
Our recommendation is to reset the device in question to factory default settings. Following the reset, change the default management credentials to something more secure (see below) before plugging the device back on the network.
IMPORTANT NOTE: Many IoT devices support multiple management protocols (SSH/Telnet/HTTP/HTTPS) over the same network interface. This means that changing the user credentials for the web administrator panel is not enough because your device may be reachable over other supported protocols from external networks. We strongly recommend restricting the inbound management access from external networks to HTTPS only.
3. Is there anything we can do to make sure IoT security is acceptable?
Recommendations for the user/enterprise:
A) Restrict access to the IoT device as much as possible from external networks. Block unnecessary ports from external access.
B) Change the default credentials to something more secure
C) If possible, enterprises should install IoT devices on isolated networks (to prevent lateral movement), with restrictions on both inbound and outbound network traffic.
D) Enterprises should invest in setting up a process to apply regular security and firmware updates to IoT devices, in addition to securing the network traffic.
Recommendations (wishlist?) for IoT manufacturers:
A) IoT device manufacturers need to start enforcing default password change as part of device installation. They should also ensure that the password changes are reflected for all supported management protocols.
B) Security and firmware updates should be automated.
Credit to Rohit Hegde for helping with the IoT traffic analysis