Since the apparent deaths of the Angler and Nuclear exploit kits, we have seen elevated activity from other groups. While RIG and Neutrino have been the primary actors in the void left by Angler and Nuclear, Sundown has also been active and making strides to increase its share of the exploit kit marketplace. We previously analyzed Sundown in January, and while it remains a significantly less sophisticated kit than other EKs, its developers are quickly working to develop the kit's capabilities. Recently, we have seen a flurry of iterative improvements in the exploit kit, similar to the behavior seen during our observation in January.
In this analysis, we will not detail the components of the Sundown EK since we covered that in our previous post, but will highlight the most interesting observations over the past month. See here for additional insight on Sundown's structure through June 30th.
2016-06-15
In the Sundown PCAP released on 2016-06-15, the landing page was a mish-mash of styles, including a section that appears ripped directly from RIG landing pages seen around April-May. This section actually caused some confusion as we saw detections for this version of the landing page mistakenly labeled RIG.
Fig 1 - Stolen RIG Code
Besides the stolen RIG code, the Sundown landing page featured a base64-encoded block to exploit Flash (though the Flash version detection code and trigger are unencoded), a second and larger base64-encoded block to exploit Flash (without external trigger code), an interesting VBScript payload that attempts to launch an additional script via wscript.exe, and a very lightly encoded VBScript payload for the GodMode vulnerability, wrapped in a JavaScript block.

Fig 2 - VBScript wrapped in JavaScript
2016-06-27
While reviewing Sundown activity, we found that the campaign was still active but the landing page structure changed enough to evade our previous signatures. At this point, Sundown had abandoned the RIG-ripoff tactic, and stuffed nearly everything into base64-encoded blocks with an overabundance of
tags.

Fig 3 - New Sundown landing page on the left, old page on the right
For some reason, a completely unencoded Flash object remained on the landing page, which included a nice shellcode payload in a FlashVar named 'exec'! The shellcode is fairly basic, using urlmon.dll to fetch a malware payload.

Fig 4 - Shellcode downloads a malware payload from the highlighted URL
2016-06-30
Close monitoring continued and although there weren't any notable changes to the landing page, we did some testing with an old VM that produced an interesting result. We did further testing and found that user-agents claiming to be Internet Explorer 6 caused a basic PHP backend to be dumped to the browser. This uncovered backend shows the construction of some static objects to serve on the landing page and a switch statement based on the results of a simple, but flawed, IE version check. The IE check causes the backend to select between two different payloads.

Fig 5 - PHP backend code dumped in the landing page response
2016-07-01
Going into the long weekend for our US office, we wanted to keep a close eye on Sundown, and noticed a few new changes. First off, the landing page structure changed, with a major inflation in code size. The landing page makes multiple uses of the JavaScript string replace function to translate the inflated landing page data back to percent escaped values to be decoded with the unescape function.

Fig 7 - String replace calls replace strings with digits
Besides the landing page inflation, we also began seeing delivery of a RAT known as NetWire or NetWiredRC. Identification was easy thanks to the thorough analysis and documentation by CIRCL, MalwareMustDie, and others.

Fig 8 - Multiple strings related to data theft from various sources
However, this seems to be a slightly updated version of NetWire. It's previously been pointed out that the RAT uses a 76-way switch statement for parsing commands from the server, while the sample Sundown delivered provided for 82 cases.

Fig 9 - IDA graph of the command parsing switch logic
The RAT was configured to communicate with 86t7b9br9.ddns[.]net (resolving to 62.210.14[.]117) on port 8980, but the server was rejecting connections at the time of analysis.

Fig 10 - C&C hostname resolves but rejects connection attempts
2016-07-05
On checking Sundown again, we found some small changes compared to the landing page seen on July 1st. The same inflationary tactics are used on the landing page but the landing page comes in a few hundred kilobytes smaller, thanks in small part to stripping of many CRLFs from the HTML.

Fig 11 - Sundown's landing page starts looking squashed without CRLFs
We noticed a very interesting change to the payload at this point: the exploit kit was actually delivering unmodified copies of PuTTY version 0.66. Visit infected website, receive PuTTY! We considered this could actually be useful if it wasn't likely to be a simple test payload.
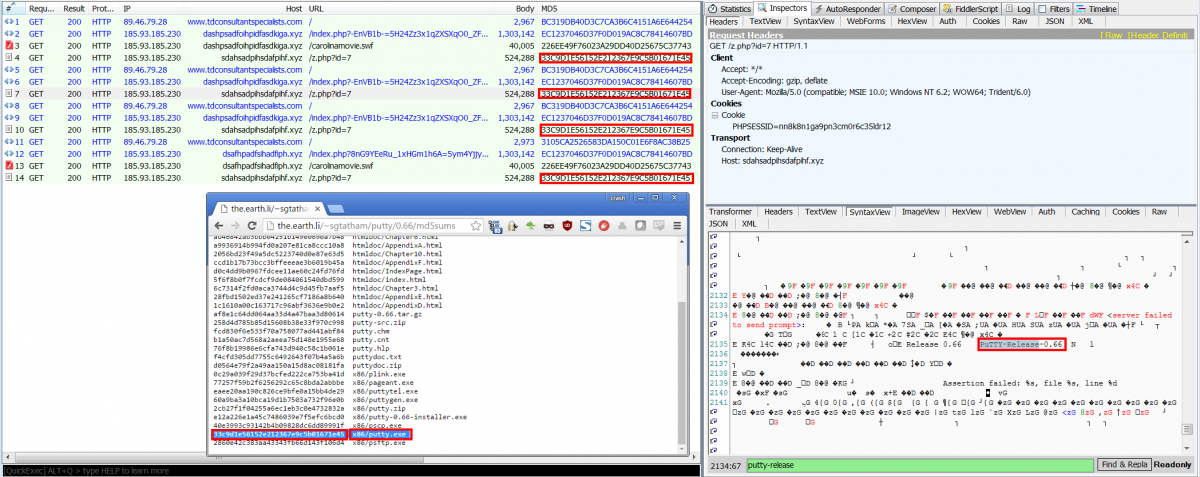
Fig 12 - PuTTY is the new calc?
With no interesting payload to investigate, we decided to do some poking at the infrastructure. We went looking for the backend admin panel, but instead we found a nice splash page. When browsing the landing page URL with no parameter, a simple HTML page with a meta tag meant to load another HTML page from a base64 encoded data tag.

Fig 13 - The meta tag of the matryoshka splash page
It turned out that the HTML didn't actually load properly (it appears the meta refresh directive doesn't work in this case), but since the actual splash page was contained in the previously mentioned data parameter, we decoded the base64 blob. This turned out to be another HTML page, this time with data:image objects for background and foreground images, with the foreground image showing a logo for a "Yugoslavian Business Network".

Fig 14 - Is Sundown really the work of the YBN?
This Russian Business Network inspired group may or may not be responsible for Sundown, but there does appear to be a German language group offering coding services on forums under the YBN moniker, with many commenters voicing their pleasure with the services.
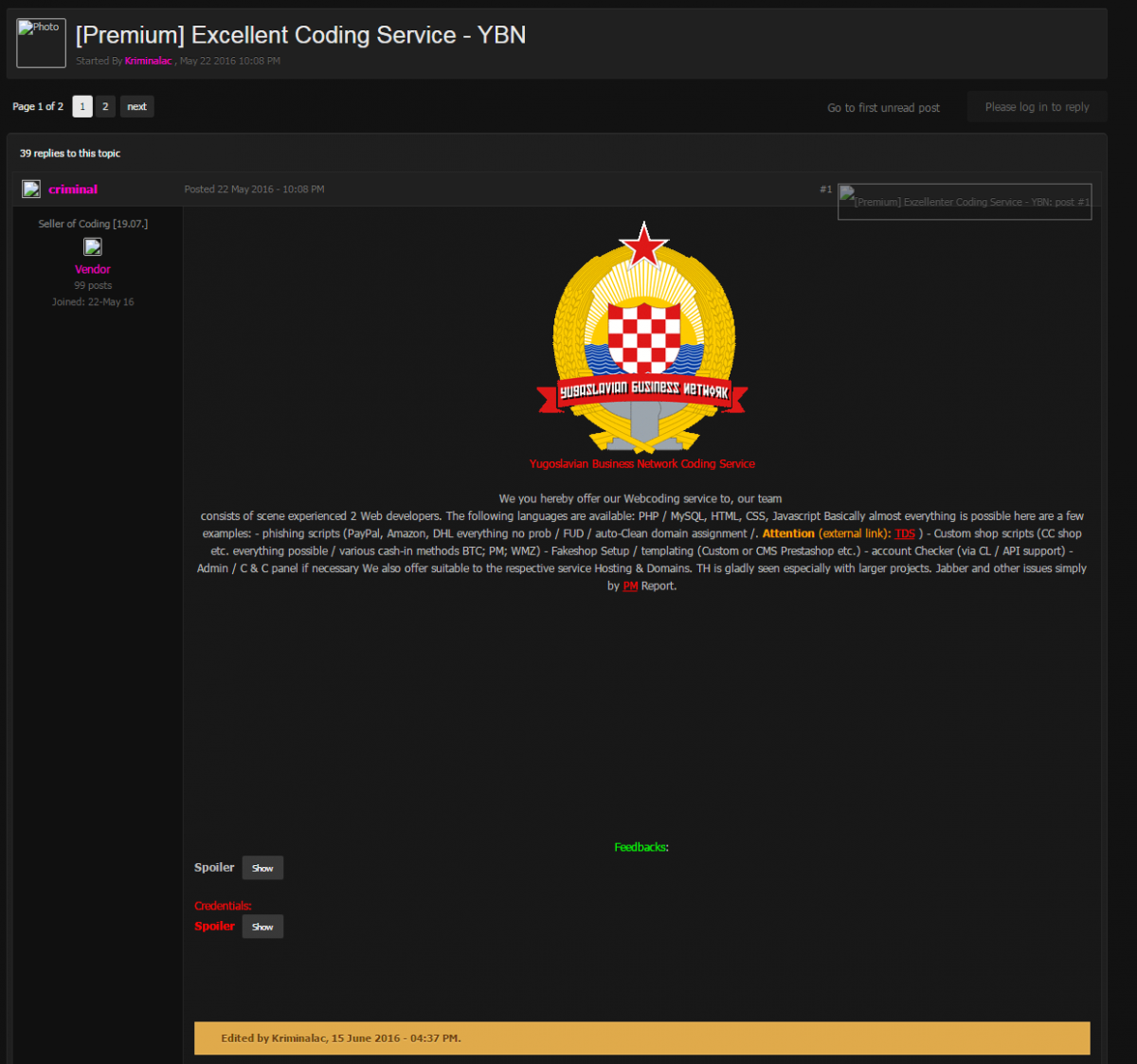
Fig 15 - Everyone loves a good logo, whether its the white-hat infosec industry or an underground black-hat forum
2016-07-06
Checking on Sundown again, we found yet more changes to the landing page. This time, the changes to the landing page itself mostly comprised small structural changes, but the functionality of the encoded blocks was altered in an interesting way. Rather than being a self-contained landing page, additional javascript payloads would be fetched from the server. Both the landing page and the secondary payloads used the same encoding/inflation technique mentioned above. Where the previous single-file landing pages were initially between 20k and 100k, then multiple megabytes, we began seeing primary landing pages of 12k supported by javascript payloads in several different sizes: approximately 300kB, 1.5mB, and 4mB.
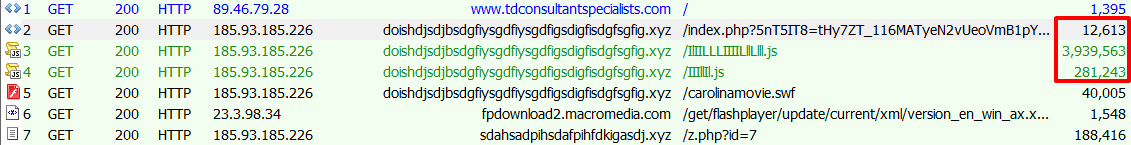
Fig 16 - The landing page itself has shrunk, but now there are huge secondary JavaScript payloads
In addition to the newly modularized landing page, we also discovered that Sundown's PuTTY service was shutdown to make way for actual malware delivery once again, with NetWire returning to the party.
2016-07-07
We found a new malware payload: a version of Kasidet that adds a base64-encoding layer to its HTTP callbacks. This is new behavior compared with our previous analysis, where we reported it being dropped by malicious spam. Callbacks were attempted to hhggffppgttt[.]ru (resolving to 185.127.25.173 at the time of analysis), including the submission of a screenshot. Cleverly, the C&C server response with 404 status codes, but the 404 pages contained base64-encoded responses inside HTML comments.

Fig 17 - Kasidet commands and responses are easily decoded
Conclusion
Since the disappearance of the two top exploit kits, Angler and Nuclear, other kits will be fighting for market share. Sundown remains technically less sophisticated than others, but as we outlined in this analysis, Sundown's authors will surely keep making rapid updates to their code. Zscaler ThreatLabZ will continue monitoring the situation to ensure protection of Zscaler customers and provide relevant updates.
IOCs
Exploit Payloads
- E785F04EA98CBF3E42C46417E7DD7925
- 226EE49F76023A29DD40D25675C37743
- 9A9FFCE2F4462C2751FA5D76E180979C
EXE Payloads
- 3bb6eba8ea26a293a238ba98a6731238
- 78df54a2465fcd2c01fa14ab72d8cdfb
- bcb80b5925ead246729ca423b7dfb635
- af8b13866833c76b93a0d7b114c2671d
- 33C9D1E56152E212367E9C5B01671E45
- AF8B13866833C76B93A0D7B114C2671D
Domains seen during analysis
- ewfihwfehiiwfhowfowfwfwfihfwhwffjwfjbfwjbkfw[.]xyz
- fdijgdlkfjgkldfjkldfjklgfjkldfjkldfjkldfgjkl[.]xyz
- djfnuihueifbnjosnfeurgbjorbjhucibyuc3dmxicnu[.]xyz
- dashpsadfoihpidfasdkiga[.]xyz
- dsafhpadfsihadfiph[.]xyz
- afihpiahfpiaefhpiadkiga[.]xyz
- afihaspifhpiasdhpidkiga[.]xyz
- doishdjsdjbsdgfiysgdfiysgdfigsdigfisdgfsgfig[.]xyz
- djfnuihueifbnjosnfeurgbjorbjhucibyuc3dmxicnu[.]xyz
- efiugfhifuwgyfjdhgyjgyfcfxhfghchgjgugkhdijos[.]xyz
- sdahsadpihsdafpihfdkigasdj[.]xyz
- sgerpijhsger0pihgsdkigasdj[.]xyz
- afsidhipafshfapsihdkiga[.]xyz
- fdshdiufsbuibnjosdnvjobsdbiyhvsbibdnjvosfnos[.]xyz
- ouaefgoiafehoafeughoaufeoiuafseghgouaesf[.]faith
- sdahsadpihsdafpihf[.]xyz
IP addresses hosting Sundown domains
- 185.93.185[.]226 (Check VirusTotal for more Sundown domains seen on this IP)
- 185.93.185[.]230 (Check VirusTotal for more Sundown domains seen on this IP)






