Once seen as the ultimate protection for data being transmitted over the internet, encryption has become a vast playground for cybercriminals.
Zscaler ThreatLabZ, the research organization at Zscaler, analyzed the encrypted traffic traversing the Zscaler cloud in the second half of 2018 and prepared a report of our findings. The Zscaler cloud processes more than 60 billion transactions a day and, at that volume, it provides valuable insight into traffic patterns and the types of threats organizations are facing globally.
We already knew that the use of encryption had been rising each year and our research showed this trend continuing. By December 2018, the amount of encrypted traffic on the Zscaler cloud increased by 10 percent to nearly 80 percent of all traffic. This growth rate is consistent with that of the Google Transparency Report and Mozilla’s findings for the Firefox browser.
Zscaler has always made its cloud statistics available to anyone who wants to see them. We have recently created a dashboard that shows the volume of encrypted traffic crossing our cloud as a percentage of total traffic. You can view that interactive dashboard here.
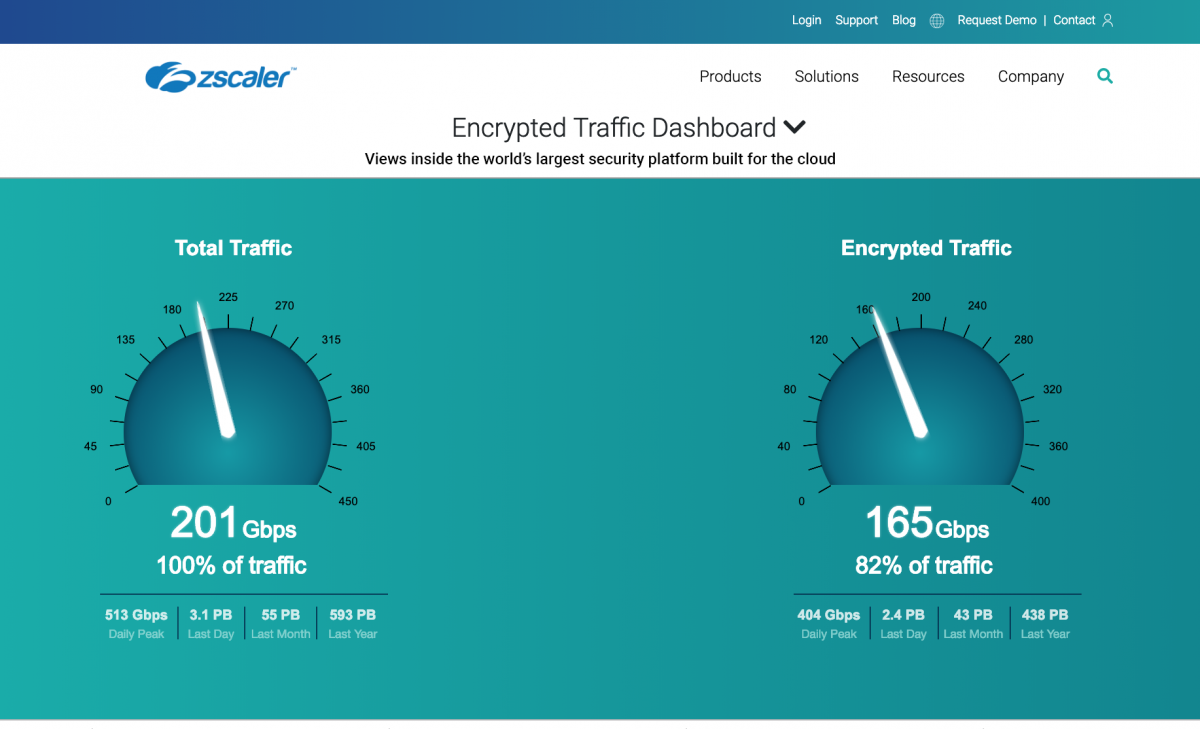 Real-Time Zscaler Cloud Activity: Encrypted Traffic Dashboard
Real-Time Zscaler Cloud Activity: Encrypted Traffic Dashboard
As the use of SSL* grows, cybercriminals are increasingly using encryption to conceal and launch attacks. In the second half of 2018, the Zscaler cloud blocked 1.7 billion threats hidden in SSL traffic, which translates to an average of 283 million advanced threats blocked per month. The top blocked threat categories in our study period included phishing attempts—which increased more than 400 percent over 2017—as well as malicious content, botnets, and browser exploits.
One of the reasons that SSL-based threats have increased so dramatically is because SSL/TLS certificates, which were once expensive and difficult to obtain, are now easy to get—at no charge. The vast majority of the certificates involved in security blocks in the Zscaler cloud were issued by Let’s Encrypt, a free service. Furthermore, nearly 32 percent of newly registered domains that were blocked by our cloud were using SSL encryption to deliver the content. We recommend inspecting and/or restricting access to newly registered domains, including those using SSL, to scan for malicious content being delivered from an otherwise unknown location with no history or reputation.
While the percentage of growth in SSL traffic is slowing as it reaches near totality, the threat trends are increasing in both frequency and sophistication. Cybercriminals know that most organizations are unable to inspect SSL traffic at scale. So, with malicious websites that can be set up in no time with free SSL certificates, they’re launching attacks that have a good chance of going undetected.
Organizations should be inspecting all encrypted traffic, even from CDNs and trusted sites, because many of the threats we continue to block are from legitimate sites that have been compromised. Organizations that don’t inspect all traffic are at risk of infiltration that can be difficult to remediate, lead to costly breaches, or damage their reputation.
Read the full ThreatLabZ analysis of SSL/TLS-based threats: SSL Report
*The encryption protocol is known by several terms—Secure Sockets Layer (SSL), Transport Layer Security (TLS), and HTTPS—and they are often used interchangeably. For the sake of simplicity, I am using “SSL” in this blog.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Deepen Desai is Zscaler VP of Security Research and Operations





