While examining our cloud sandbox data recently, we uncovered a large MultiPlug network that caught our attention due to its use pattern of code signing certificates and the breadth of its hosting infrastructure.
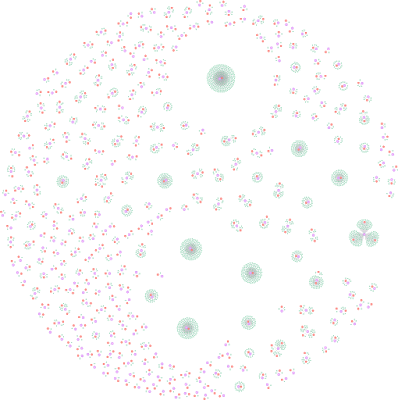 |
| Overview of the Scamware Hosting Network (Node Legend -- Red: Host, Pink: Domain, Green: File-MD5) |
As we discussed in June, MultiPlug is a common scamware family that tricks users into downloading/installing an initial binary, which then delivers a variety of additional spyware packages. Search poisoning is used to bait users into installing the scamware, with the lures including cracked and legitimate software, pirated music and movies, as well as other documents and files that a user might be seeking.
 |
| This installer pretends to help speed up your downloads |
After taking the bait and executing the file, the user is presented with one of several typical-looking installer dialogs that promise to deliver what the user was originally searching for. Whether the user realizes the mistake or not, the “installer” will proceed to fetch multiple encrypted payloads from a remote webserver. The installation of the payloads continues even if the user clicks the various “Decline,” “Cancel,” or “Exit” buttons. Throughout the process, the scamware also gathers system information and sends it to remote web servers.
 |
| Data sent to remote servers via HTTP POST |
Several typical components of the scamware include a payload called "compfix" that is installed as a system service to be run at boot time, as well as a payload called "SystemStrengthener."
 |
| "compfix" installed as a service |
Besides the benevolent-sounding payloads mentioned above, the scamware makes a few changes to the user’s browser configuration. If Chrome is installed, two DLLs are dropped into the Chrome installation directory that appear to be modified and slightly outdated versions of chrome.dll. Chrome and Internet Explorer also receive browser extensions that spy on user behavior and serve ads. As a bonus, the IE add-ons are marked as uninstallable without administrator approval.
 |
| Modified Chrome DLLs with invalid certs |
 |
| User is prevented from disabling scamware addons |
 |
| User is prevented from disabling scamware addons |
 |
| New Chrome addons installed without notice |
Apart from some additional obfuscation layers compared to previous versions, the technical aspects of this malware are fairly standard. However, the breadth of the hosting network and the pattern of code-signing certificates used made this an interesting campaign. We uncovered 33 unique certificates, all issued from the same Certificate Authority: Certum / Unizeto Technologies. (Note: we also identified other adware campaigns utilizing Certum certificates, though they appeared to be unrelated.)
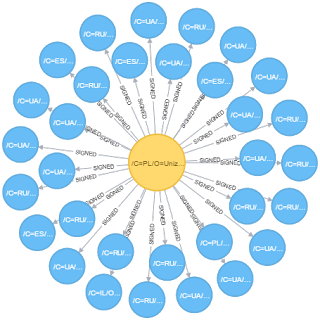 |
| Unizeto Technologies / CERTUM issued certificates (Node Legend -- Yellow: Issuer, Blue: Signer) |
These 33 certificates were used to sign 2,783 pieces of scamware that were hosted on 447 unique hosts (323 unique domains). While it's normal for adware campaigns that utilize code signing to rotate through their certificates as they are blocked by AV and security companies, the volume of unique signing certificates in use signals that something is different here. Additionally, the data in the signatures indicates that all of the certificates are owned by individual persons with free email accounts. This hinders naive denylist updates as well as attribution, since there is no clear way to link the campaign to a specific organization.
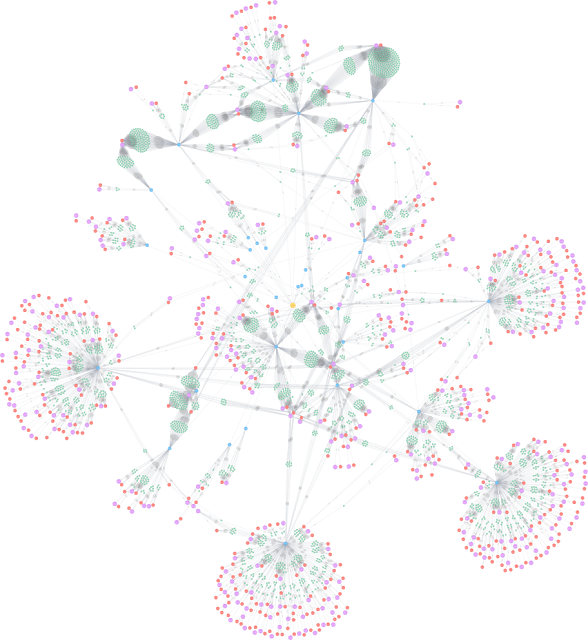 |
| Overview of the Scamware Network (Node Legend -- Yellow: Issuer, Blue: Signer, Red: Host, Pink: Domain, Green: File-MD5) |
Given the nature of this MultiPlug campaign, it is easy to hypothesize that the organization behind it has more malicious intent than the usual adware/scamware operators. That said, it could just be a matter of the organization trying to maximize ROI for this large infrastructure it operates. Regardless of their intentions, enterprises should be wary of even the most innocuous-looking adware due to the ability to perform system and network reconnaissance, achieve persistence on infected hosts, deliver arbitrary payloads, and take control of the system, its applications, and its data.















