I'm working on generating our Q2 2010 Stats and Trends report, and I noticed a large number of blocked exploit kit activity from domains registered with the .IN TLD. These were not hacked sites but domains registered for the explicit purpose of supporting a criminal enterprise. This activity is on-going. As the post will show, the campaign involves leveraging exploit kits to exploit known vulnerabilities on client applications and installing various payloads including installing various wares to monetize pay-per-installs.
A large number of the the malicious domains have been hosted on:
91.188.60.225 - 91.188.60.227
These IPs belong to the 91.188.60.0/24 owned by ATECH-SAGADE:

Which other ATECH-SAGADE netblocks have been described as "evil" in blog posts from earlier this month:
"Evil network: Sagade Ltd / ATECH-SAGADE" -- Dynamoo
"Basically, 91.188.59.0 – 91.188.59.255 is completely evil and has no legitimate use as far as I can see." -- ComputerSecurityArticles
"Exploits, Malware, and Scareware Courtesy of AS6851, BKCNET, Sagade Ltd." -- ComputerSecurityArticles
There have also been a number of recent malicious sites related to this .IN campaign seen on the 85.234.190.0/24 ATECH-SAGADE netblock as well, for example:
nvild.in
volnv.in
uinge.in
brusd.in
woonv.in
brayx.in
edois.in
which currently resolve to 85.234.190.4, .15, and .16.
Here is a snippet of what we've seen and blocked related to this ongoing .IN campaign:

Other open-source research show several of these sites still live on this /24, for example:
http://support.clean-mx.de/clean-mx/viruses.php?ip=91.188.60.225&sort=id%20desc
http://support.clean-mx.de/clean-mx/viruses.php?ip=91.188.60.226&sort=id%20desc
http://support.clean-mx.de/clean-mx/viruses.php?ip=91.188.60.227&sort=id%20desc
Here is an example of the WHOIS for one of the malicious .IN domains:
 Russian based information and self-resolving domain. The name servers currently resolve to 91.188.60.225 and 91.188.60.229 respectively on the same ATECH-SAGADE netblock.
Russian based information and self-resolving domain. The name servers currently resolve to 91.188.60.225 and 91.188.60.229 respectively on the same ATECH-SAGADE netblock.
Here is a small snippet from the exploit kit hosted on the .IN domains:
 I believe this is from the SUTRA exploit pack. In any case, here is an example of an earlier Wepawet report from analyzing one of these .IN sites:
I believe this is from the SUTRA exploit pack. In any case, here is an example of an earlier Wepawet report from analyzing one of these .IN sites:
http://wepawet.iseclab.org/view.php?hash=753106a87a6e72e407c7e7b80164a538&t=1277905162&type=js
The exploits detected from the report are CVE-2009-0927 and CVE-2007-5659
And the ActiveX controls:
CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA
CA8A9780-280D-11CF-A24D-444553540000
While many of the payloads include Trojan Downloaders and FakeAV, there have been some other wares installed via this campaign. VirusTotal has shown that some of the payloads dropped by the kit are undetectable via anti-virus:
http://www.virustotal.com/analisis/bb16ee91e726a4d99e79e1815f539bbac6fc5195a0ef2b9f2d25d5df8ab11148-1277895209
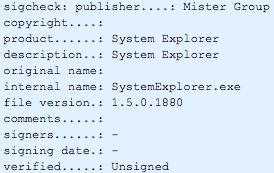
The sigcheck on the artifact shows it as System Explorer by the Mister Group:
 Secunia has a brief advisory posted on the Mister Group and their System Explorer here.
Secunia has a brief advisory posted on the Mister Group and their System Explorer here.
The Mister Group has a few pages setup for their System Explorer:
http://www.mistergroup.org/
http://www.systemexplorer.net/


From the above, it seems that this campaign is largely driven by pay-per-install profit.
Zscaler Blog
Get the latest Zscaler blog updates in your inbox
ATECH-SAGADE Badness - Malicious .IN Campaign
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




