The infected host does an HTTP POST every 5 minutes to the URL:
hxxp://216.108.234.168/scr1p7-r5.php
The IP is part of a US netblock, Las Vegas NV Datacenter PREMIANET, swipt out to a customer in the Ukraine (UA):
Vladimir Miloserdov SERVERPOINT-CUSTOMER-SYNEJY (NET-216-108-234-166-1) 216.108.234.166 - 216.108.234.197
Here is the customer information for this small netblock:
CustName: Vladimir Miloserdov
Address: So,136
City: Donetsk
StateProv: DN
PostalCode: 83054
Country: UA
RegDate: 2009-05-24
Updated: 2009-05-24
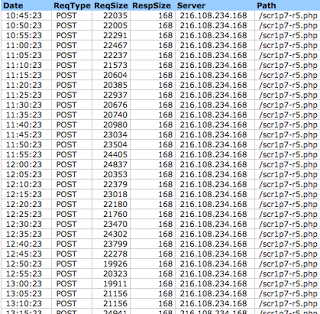
Below is a snippet of the transactions seen.
Notice that the size of the POST is larger than the response from the server - over 20000 bytes compared to a very short response of 168 bytes. This means that the client is regularly pushing a fair amount of data somewhere and not receiving anything other than a very simple acknowledgment back. In the case of a normal web application, pushing data to a server usually has a larger response such as a webmail or blog interface.
Visiting 216.108.234.168 responds with the default Apache response “It works!”
Open-source searches show that the IP is blocked in a few block lists due to spam, e.g., Project Honeypot.
At a minimum this netblock is suspicious and should be alerted/blocked within your organization.
Reaching out to some colleagues, helped to reveal that this beaconing is likely tied to the Swarft Banking Trojan due to the “scr1pt7-r#.php” phone home URL path. This is a relatively new Trojan family, the Microsoft threat entry states, that the Trojan steals data that may “include credit card numbers, tax returns, login credentials or any other informed deemed to be of interest to the attacker. The collected data is then surreptitiously sent to the remote attacker via a variety of electronic means.” Technical details of the Trojan do not appear to be readily available in the open-source- I am in the process of back tracking and reaching out to the impacted customer to get additional information on the Trojan and the incident. Any new details will be shared in a follow-up post.
Also, if anyone has details on the above-mentioned netblock or Swarft Trojan, feel free to post a comment.




