Background
Earlier today Microsoft released several security updates as part of its regular monthly updates known as Patch Tuesday. Some of the issues that were patched in today's update are critical and has prompted an emergency directive from Cybersecurity and Infrastructure Security Agency (CISA) for certain U.S. government agencies. It is important for everyone running the vulnerable operating system to apply this security update. Large organizations following 15/30/60-day patch cycles should consider making an exception and apply the patches as soon as possible, especially if running one of the vulnerable operating systems.
What are the issues?
1. CVE-2020-0601 - CryptoAPI spoofing vulnerability
A spoofing vulnerability exists in the way Windows CryptoAPI validates the Elliptic Curve Cryptography (ECC) certificates. This vulnerability allows an attacker to use spoofed ECC certificates for signing malicious files to evade detection or target specific hostnames to evade browser security alerts.
Systems impacted: Several versions of Windows 10 and Windows Server 2016, 2019 [Check the reference for specific details]
2. CVE-2020-0609, CVE-2020-0610 - Windows Remote Desktop Gateway remote code execution vulnerability
An unauthenticated attacker could exploit a remote code execution vulnerability in Windows Remote Desktop Gateway by connecting over RDP and sending specially crafted requests. No user interaction is required for exploiting this vulnerability.
Systems impacted: Windows Server 2012, 2016, 2019 [Check the reference for specific details]
3. CVE-2020-0611 - Windows Remote Desktop Client remote code execution vulnerability
An attacker could exploit a remote code execution vulnerability in Windows Remote Desktop Client by tricking the user into connecting to a malicious server hosting this exploit.
Systems impacted: Several versions of Windows 7, 8, 10 and Windows Server 2008, 2012, 2016, 2019 [Check the reference for specific details]
What can you do to protect yourself?
Apply the security updates released by Microsoft immediately from the following location:
https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Jan
Zscaler coverage
Zscaler Cloud Sandbox provides proactive coverage against worm payloads and advanced threats, such as ransomware, and the Zscaler ThreatLabZ team is actively monitoring for in-the-wild exploit attempts to ensure coverage.
We have also deployed several in-line signatures for detecting exploitation attempts of CryptoAPI spoofing vulnerability.
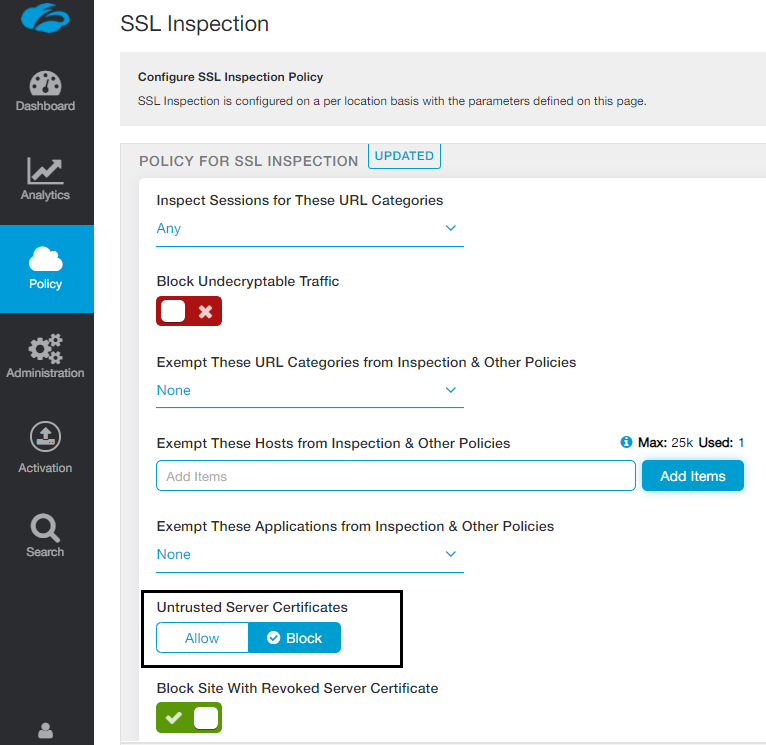
Additionally, Zscaler customers can leverage SSL inspection feature and block such spoofed certificates under 'Untrusted Server Certificates'. This will block any connection to destinations serving such spoofed certificates.
Reference:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0601
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0609
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0610
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0611





