Zscaler Blog
Get the latest Zscaler blog updates in your inbox
DanaBleed: DanaBot C2 Server Memory Leak Bug
Introduction
DanaBot is a Malware-as-a-Service (MaaS) platform that has been active since 2018. DanaBot operates on an affiliate model, where the malware developer sells access to customers who then distribute and use the malware for activities like credential theft and banking fraud. The developer is responsible for creating the malware, maintaining the command-and-control (C2) infrastructure, and providing operational support. DanaBot has been involved in several high-profile campaigns, such as a supply chain attack on popular NPM packages and a Distributed-denial-of-Service (DDoS) attack against the Ukrainian Ministry of Defense during the 2022 Russian invasion. In May 2025, as part of a continued effort in Operation Endgame, law enforcement dismantled DanaBot's infrastructure and indicted 16 individuals affiliated with the group.
One aspect of DanaBot that has not been publicly known until recently is a bug in DanaBot’s C2 server that introduced a memory leak. In June 2022, a then new version of the DanaBot malware (version 2380) was identified in-the-wild by ThreatLabz. This update introduced changes to the C2 protocol, one of which inadvertently caused the C2 server to leak snippets of its process memory in responses to infected victims. The memory leak, comparable to the Heartbleed vulnerability of 2014, offered those who discovered the bug (including ThreatLabz) to gain unique visibility into the internal operations of DanaBot. We have named this vulnerability DanaBleed and in this blog, we will present some of the sensitive information that we were able to recover from the memory leaks over nearly three years.
Key Takeaways
- DanaBot is a Malware-as-a-Service platform that emerged in 2018 with numerous capabilities to facilitate banking fraud, information theft, and provide remote access.
- The platform has been used for a variety of purposes from banking fraud to espionage. From June 2022 to early 2025, a programming error in the DanaBot command and control (C2) server caused a memory leak.
- Leaked information included: threat actor usernames, threat actor IP addresses, backend C2 server IP addresses and domains, infection and exfiltration statistics, malware version updates, private cryptographic keys, victim IP addresses, victim credentials, and other exfiltrated victim data.
- In May 2025, Operation Endgame dismantled DanaBot infrastructure and indicted 16 members affiliated with the group.
Technical Analysis
The DanaBleed memory leak began with the release of DanaBot version 2380 in June 2022 and continued until early 2025.
Analysis of the DanaBleed vulnerability
DanaBot is written in the Delphi programming language and uses a custom binary C2 protocol. A general overview of C2 requests prior to the June 2022 version update was the following:
- Generate command data (e.g. key exchange, system information beacon, configuration file download, additional payload download, new C2 information, etc.)
- Encrypt data with a session key
- Encrypt session key
- Generate a basic header
- Send header and encrypted data
In June 2022, the malware developer introduced a new C2 protocol that modified the requests to perform the steps below:
- Generate command data (e.g. key exchange, system information beacon, configuration file download, additional payload download, new C2 information, etc.)
- Ostensibly append randomly generated bytes (although they were not random)
- Encrypt data with a session key
- Encrypt session key
- Send encrypted data length and data
Responses from the C2 server to the victim were generated using the same logic and likely the same underlying code as the malware itself. This overlap allowed us to reverse engineer the vulnerability and make inferences about how the C2 server memory leak worked.
The figure below illustrates the changes to the C2 protocol introduced in the June 2022 update:
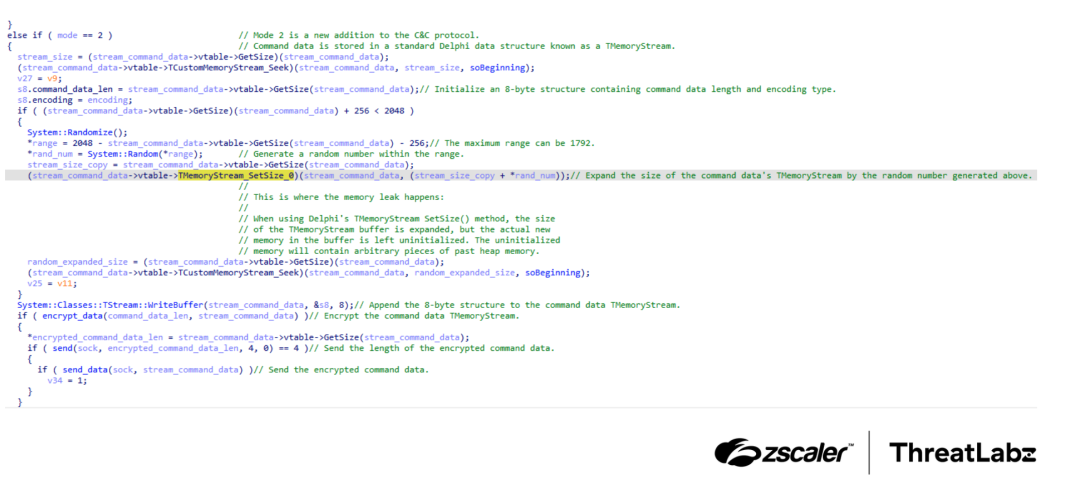
Figure 1: Overview of C2 protocol changes introduced in DanaBot in the June 2022 update.
DanaBot’s command data was stored in a Delphi TMemoryStream. A random number, capped at a maximum value of 1,792, was generated to determine the number of padding bytes to add to the command data buffer. While the size of the buffer was increased, the newly allocated memory within the buffer was not initialized. At first glance, this uninitialized memory appeared to be random, but closer inspection revealed that it contained arbitrary fragments of the C2 server’s process memory. This oversight in memory handling created the DanaBot vulnerability that exposed the group’s sensitive internal data.
Data exposed by the memory leak
The memory leak allowed up to 1,792 bytes per C2 server response to be exposed. The content of the leaked data was arbitrary and depended on the code being executed and the data being manipulated in the C2 server process at a given time. Despite this, our examination of the leaked data allowed us to extract meaningful insight into DanaBot for nearly three years.
Some of the most intriguing leaks revealed HTML snippets associated with the C2 server's web interface. The figure below, with highlights added, provides a sample of these leaked elements.

Figure 2: Example of leaked HTML code from DanaBot’s C2 server.
These HTML snippets can be compared to the figure below (highlights added) which includes a screenshot from a video advertising DanaBot.
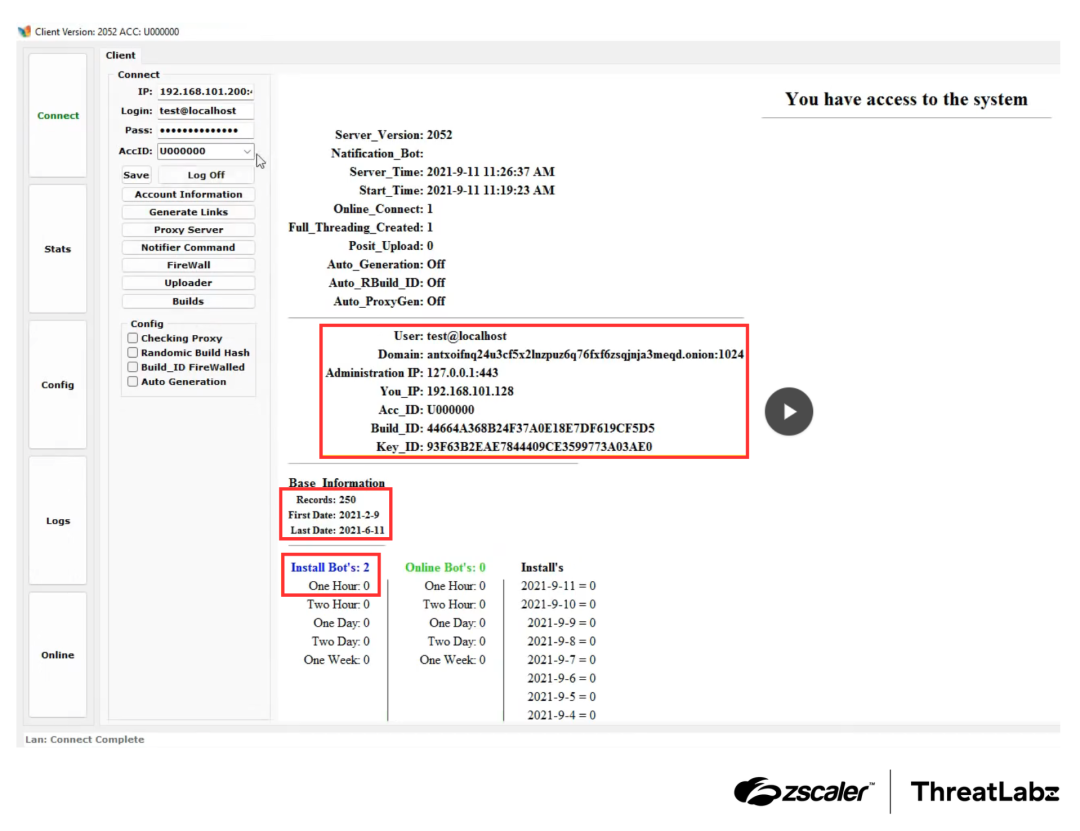
Figure 3: Screenshot from a DanaBot advertisement video with content similar to the data observed in C2 server memory leaks.
The memory leak exposed sensitive data including:
- Threat actor usernames and IP addresses
- Backend C2 server IP addresses and domains
- Infection and exfiltration statistics
- Malware version update information
- Private cryptographic keys
- Victim-related data, such as IP addresses, credentials, and exfiltrated information
The DanaBot developer maintained a changelog of updates and some of those changes were also leaked, as shown in the figure below (highlights added).
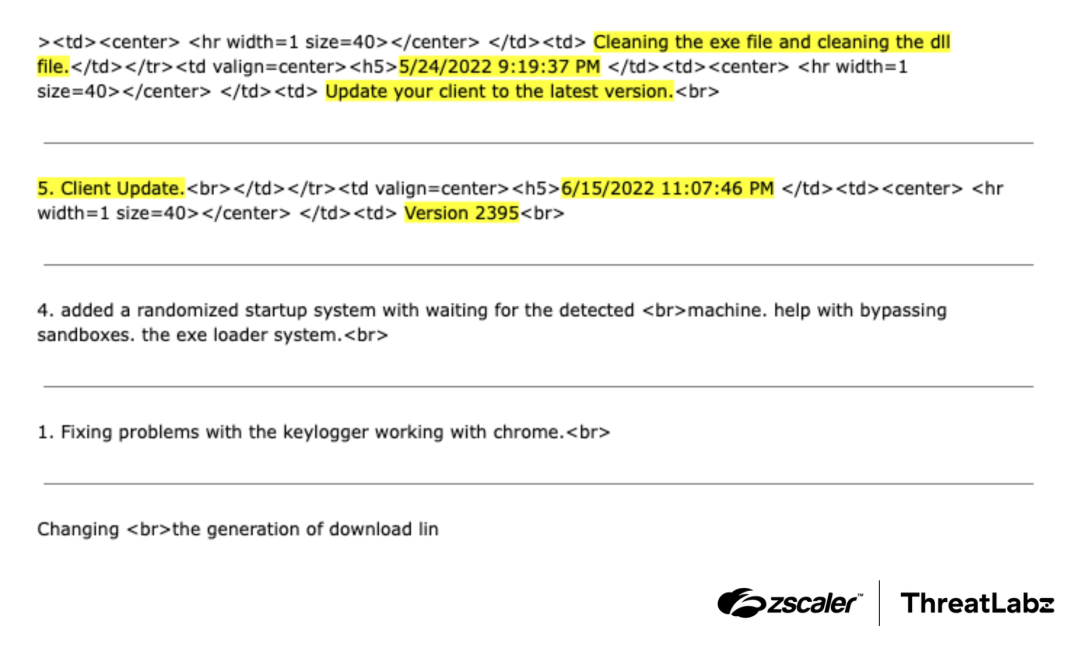
Figure 4: Sample change log discovered in DanaBot C2 server memory leaks.
In addition to HTML snippets, the memory leak also exposed debug information, including pathnames and logging messages. These are demonstrated in the figure below.
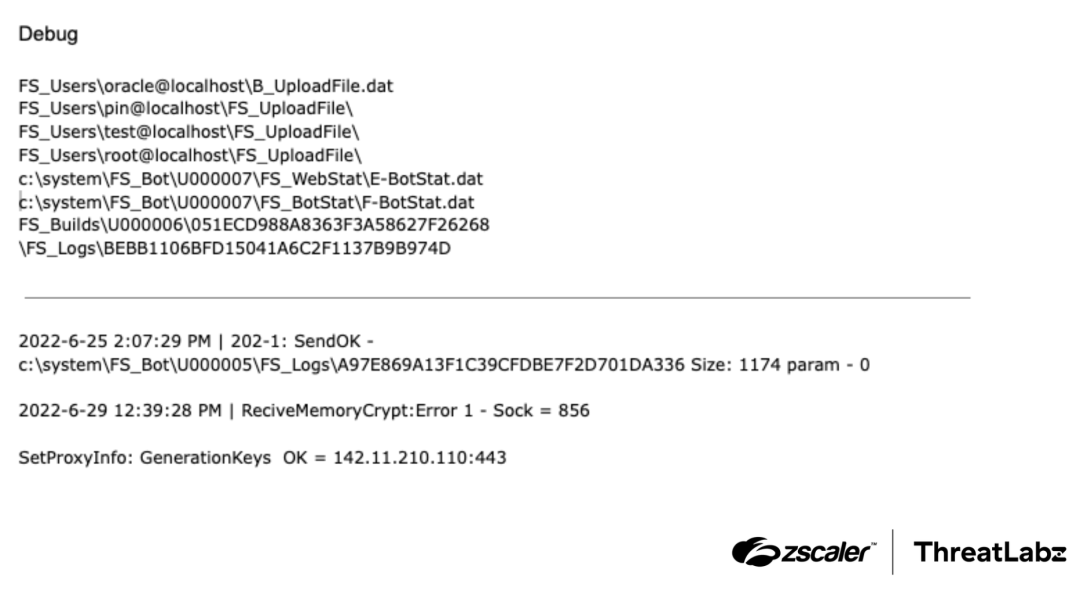
Figure 5: Sample debug information identified in DanaBot C2 server memory leaks.
Another frequent type of leak involved SQL statements. These leaks offered valuable insights into the C2 server's database structure, including information such as malware MD5 hashes, version updates, and victim IP addresses. The figure below (with highlights added) provides an example of these leaks.

Figure 6: Sample SQL statement leak by DanaBot’s C2 server.
The memory leaks also exposed private cryptographic key material, as shown in the figure below (highlight added):

Figure 7: Sample private key material leaks.
Finally, as DanaBot primarily functioned as an information stealer, the memory leak also exposed a significant amount of victim credentials and other exfiltrated data.
Conclusion
The memory leak discovered in the June 2022 update of DanaBot's C2 server protocol gave ThreatLabz and other researchers a glimpse into the inner workings of DanaBot. By analyzing the leaks from uninitialized C2 server memory over time, we gained valuable insights into the infrastructure, processes, and threat actors behind DanaBot. The leaked information revealed everything from backend server data, debugging logs, SQL statements, and cryptographic key material to sensitive victim data and elements of the C2 server's web interface. It is too soon to determine the impacts that Operation Endgame will have on DanaBot in the long term, but ThreatLabz will continue to track the activities of the group and their affiliates if they reemerge.
Zscaler Coverage
Zscaler’s multilayered cloud security platform detects indicators related to DanaBot at various levels. The figure below depicts the Zscaler Cloud Sandbox, showing detection details for DanaBot.
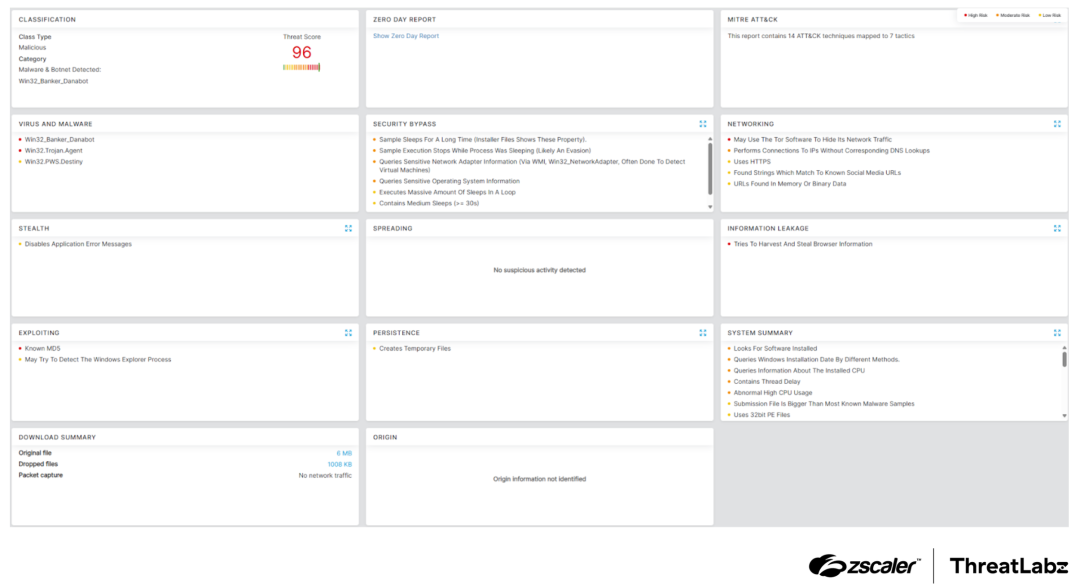
Figure 8: Zscaler Cloud Sandbox report for DanaBot.
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to DanaBot at various levels with the following threat names:
Indicators Of Compromise (IOCs)
IOC | Notes |
|---|---|
3ce09a0cc03dcf3016c21979b10bc3bfc61a7ba3f582e2838a78f0ccd3556555 | SHA256 hash of DanaBot version 2380 main component |
ae5eaeb93764bf4ac7abafeb7082a14682c10a15d825d3b76128f63e0aa6ceb9 | SHA256 hash of DanaBot version 4006 |
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.