Background
Upatre is a Trojan Downloader family that once installed, is responsible for stealing information and downloading additional malware onto the victim machine. It typically arrives via spammed e-mail messages from the Cutwail Botnet, either as an attachment or via a URL pointing to a remote hosting site. We are also seeing Exploit Kits being used as a vector for Upatre infections in the wild.
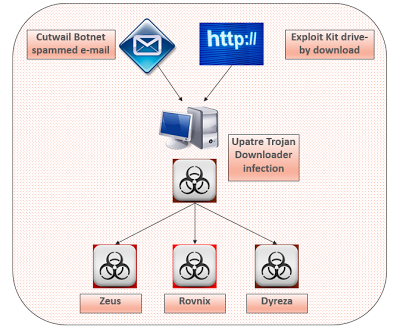 |
| Upatre Downloader cybercrime network |
Upon successful infection, Upatre has been responsible for downloading malicious payloads from known malware families such as:
- Zeus (Zbot) banking Trojan
- Rovnix Volume Boot Record (VBR) bootkit
- Dyreza (DYRE) banking Trojan
The Upatre malware family was first discovered in August 2013 and exponentially increased its infection rates by October, 2013. With the demise of the popular Blackhole Exploit Kit in October 2013, many malware authors resorted to traditional spam with the Upatre Trojan downloader as a medium for delivery of the ultimate payload, which also contributed to the increase in infections.
The Upatre malware authors have deployed multiple new techniques over the past year, which is the reason why it is one of the most prevalent malware families today. Some of the features that we have tracked include:
- Password protected attachments - This makes the e-mail look more legitimate and confidential
- Spammed as an attachment inside an attachment - The spammed e-mail messages contained another e-mail message (*.msg, *.eml) as an attachment which contains the actual Upatre archive attachment
- Email messages containing a URL pointing to the actual payload
- Randomized header bytes and encrypted malware downloads to evade detection
- Usage of SSL encryption for Command & Control (C2) communication and subsequent malware downloads
Recent Attacks
We have seen an increase in the number of Upatre Downloader infections occurring through spammed messages containing fake invoices or voice-mail messages in the past month. The final payload being downloaded from these recent Upatre infections tends to be the Dyreza Banking Trojan. Below is a sample e-mail message from this campaign:
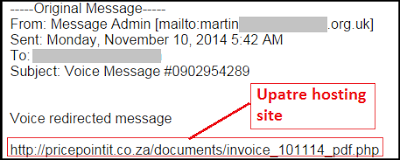 |
| Cutwail spam e-mail leading to Upatre |
If the user clicks on the link in the e-mail, they will be redirected to the same site with additional information identifying the operating system in the URI before serving the payload as seen here:
GET /documents/invoice_101114_pdf.php?h=[3 digit integer]&w=[4 digit integer]&ua=[User-Agent String]&e=1 HTTP/1.1
The user will then be prompted to download a zipped archive file, which contains a new variant of the Upatre Trojan downloader as seen below:
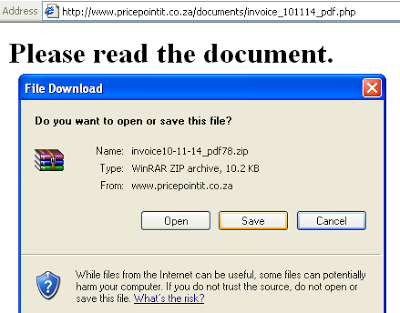 |
| Upatre download in an archive |
The user is redirected to a legitimate site (i.e "www.hsbc.com"), if the operating system is not supported or is redirected at the end of the download cycle.
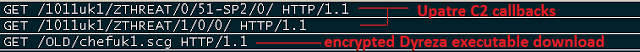 |
| Upatre network communication |
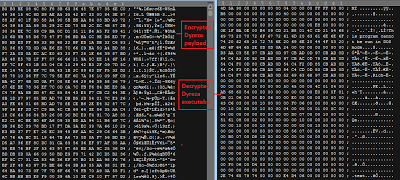 |
| Dyreza banking Trojan encrypted and decrypted payload |
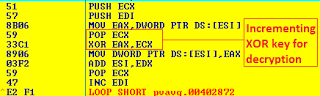 |
| Part of Upatre decryption routine for downloaded payload |
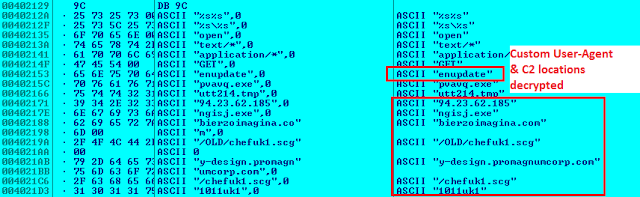 |
| unpacked Upatre binary |
Indicators of Compromise
Here is a sample list of HTTP requests that will provide a good indication of an Upatre and Dyreza compromise on your network:
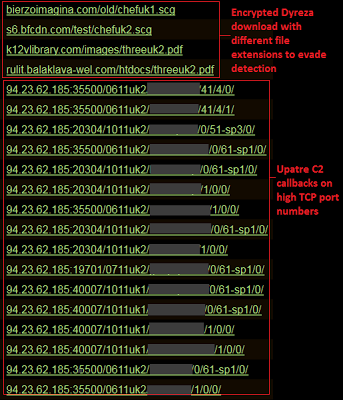 |
| Upatre indicators of compromise |
- ENUPDATE
- ONLYUPDATE
- UPDATE
The Upatre Trojan downloader family continues to evolve and is one of the most prevalent malware families at present. It continues to add new malware to its cyber crime pay-per-install nexus, serving as a vector for downloading and installing additional malware family payloads.
Zscaler ThreatLabZ is actively monitoring this threat and ensuring full security coverage for our customers.





