Exploit kits available in the wild tend to follow a trend by exploiting vulnerabilities reported in various browser components which are commonly deployed. Recently, we have seen an increase in exploitation of a year old vulnerability reported in the JRE component of JAVA (
CVE-2012-1723). Exploitation of this vulnerability in JRE allows a attacker to download malware onto a victim's machine and execute it. Let's looks at an analysis of such an exploit kit recently found in the wild.
Exploit Kit URL:
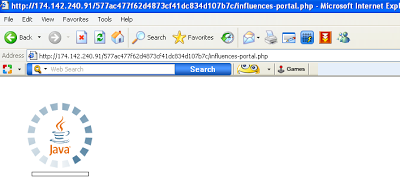
hxxp://174.142.240.91/577ac477f62d4873cf41dc834d107b7c/influences-portal.php
When accessed, the above exploit URL executes obfuscated JavaScript and loads an applet into the browser as shown below:
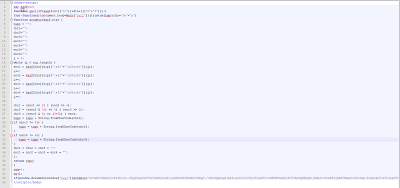
Obfuscated source code:
Let's analyze the above obfuscated JavaScript code by de-obfuscating it. While de-obfuscating the JavaScript code, we noticed that the code has multiple layers of obfuscation. For the scope of this article, lets skip ahead to the end of the de-obfuscation process.
As usual, the exploit kit request loads content based on the version of the browser and versions of different plugins installed in a browser by running browser/plugin detection logic embedded in obfuscated JavaScript. The exploit kit targets vulnerabilities in JRE (Java) and Adobe components of the browsers.
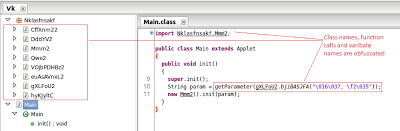
Let's take a look at following de-obfuscated code which loads malicious applet into browser:
The following code calls the relevant functions above, depending upon the JRE version found on the victim's machine:
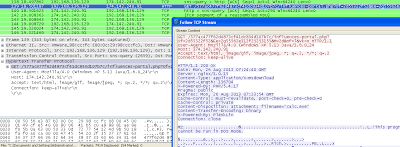
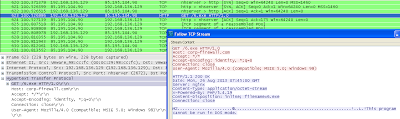
The applet is executed by the browser, which then downloads a malicious .jar file from following URL,
hxxp://174.142.240.91/577ac477f62d4873cf41dc834d107b7c/influences-portal.php?gKoRO=UfhqAFb&gCTEVgSTdQbZjI=wUkSXV
The de-complied code of the downloaded .jar file is also heavily obfuscated.
MD5: 361b0e1eab5e647315e6873ea16ca720
This .jar files exploits the vulnerability in the JRE, which allows the attacker to download additional malware and execute it the browser context.
MD5: a151fdce265ba4fcab1b36bd624d330f
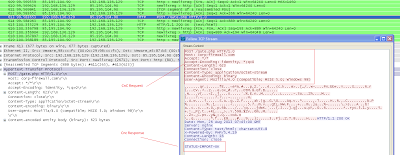
A Trojan then connects to the CnC server by sending POST data and in response, the CnC server replies with 'STATUS-IMPORT-OK'.
After receiving command 'STATUS-IMPORT-OK' from the CnC server, The Trojan then downloads another malware file (6.exe) from the same domain which looks to be a variant of ZerooAccess rootkit. The detection rate for the '6.exe' is also fairly low on VT.
MD5: b152b3d170dc089b057fbbe3d6393764
Exploitation of browser components such as Java and Adobe plugins by exploit kits are now a very common reason for enterprise PCs to become compromised. My colleague Krishanan Subramanian recently blogged about a rise in
Red Kit Exploit Kit Activity, which also addressed the same vulnerability in Java. It is vital that enterprises ensure that browser plugins are always patched and up to date, something enterprises regularly fail to do. In the case Java, given the now regular stream of 0days that it has inspired, you may want to seriously consider disabling Java altogether, at least at the browser level, something that you can read about in a previous blog post entitled:
Are you vulnerable to yet another Java 0Day exploit?
Pradeep