Recently, the Russian government ordered the immediate blocking of the messaging app Telegram and requested its removal from the Apple App Store and Google Play Store. In reviewing activities around this matter, Zscaler ThreatLabZ researchers noticed a fake Telegram app making the rounds in the Google Play Store. Zscaler informed Google about the fake app and it was promptly removed from the store.
Because Telegram is partially open-source, we initially thought this fake Telegram app was a regular app implementing Telegram APIs. However, upon further analysis, we found that the fake app had been repackaged, in which case it is possible that a developer simply decompiled the original Telegram app and added advertisement libraries. We also noticed that the name and icon of the fake app changes after installation. Our analysis is detailed below.
App Details
Name: Telegraph Chat (which changes to Teleg'e'ram after installation)
Package Name: com.telegeram.anydev
Hash: 1f188831ec559566f8746e5e57bb1fcbb0f30ead
VT count: 2/62 (at time of analysis)
The screenshot below shows the fake Telegram app (left) and the original Telegram app (right). The fake app portrayed itself as Telegraph Chat and the Play Store description of the app was precisely the same as the original Telegram app. The only differences were that the term Telegram was changed to Telegraph Chat and the app icon was slightly altered after installation.
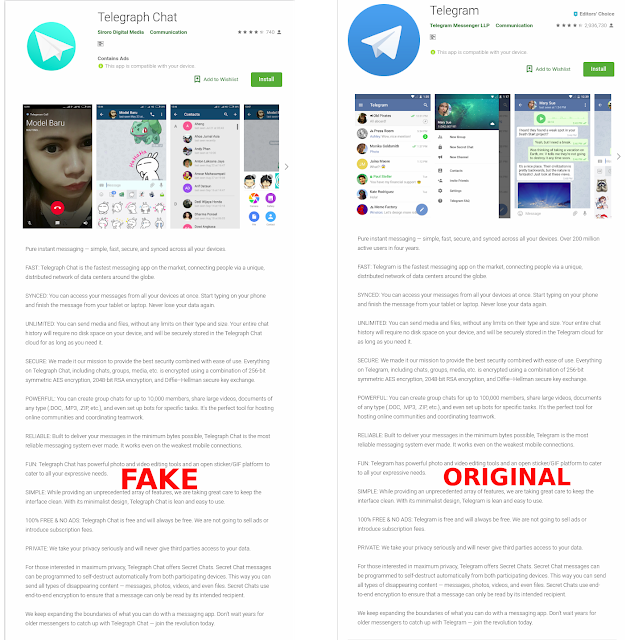 |
| Fig 1: Fake app vs original app (Google Play Store) |
The screenshot below on the left shows the app as it appears in Google Play, displayed as Telegraph Chat. The screenshot on the right shows how the app changes after installation, displaying a different icon and name, Telegeram (notice the extra “e”).
 |
| Fig 2: Fake app name/icon change |
As soon users try to open the app, they are bombarded with different types of ads. Below is a screenshot of banner ads inside the app (left) and an interstitial ad (right).
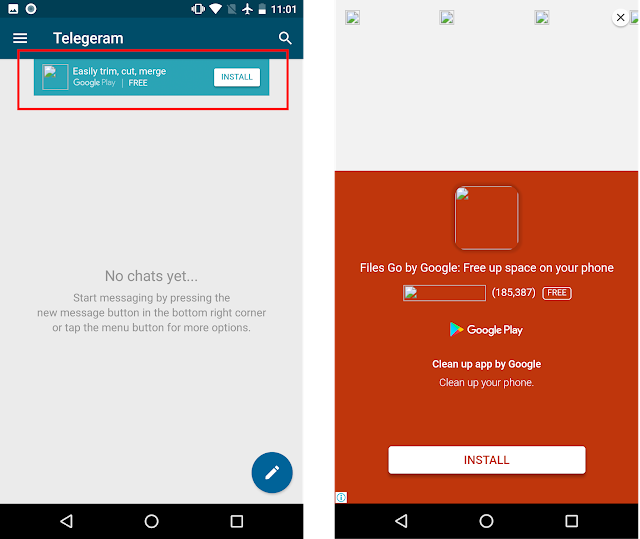 |
| Fig 3: Ads displayed by fake app |
In one instance, we also noticed an obfuscated piece of code sent by the server that contained a Play Store link to browser named Silver Mob US Browser. We could not analyze this app because it had been removed from Google Play Store before our investigation began. The screenshot below shows the response and further functionality.
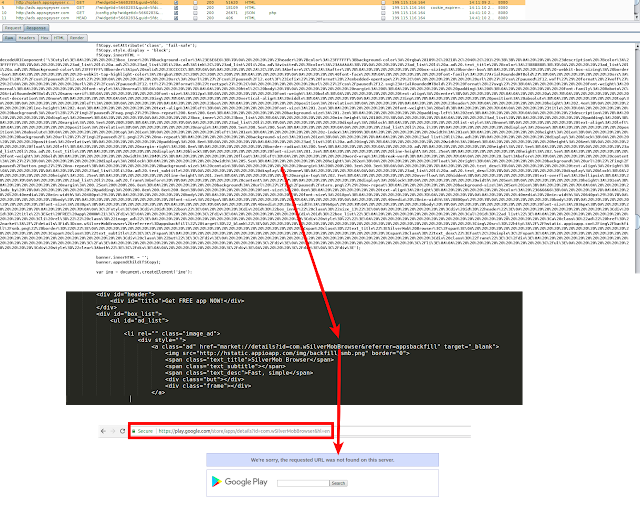 |
| Fig 4: Download link leading to 'removed' Play Store app |
Adware, such as this example, presents a threat, because it is capable of providing links that can lead users to download highly malicious Android apps.
In our analysis, we noticed that the fake app performed original Telegram app's messaging functions, but other functions were missing. We tried calling to other numbers, which is a functionality in the original Telegram, but the fake app stopped working, as shown in the message below:
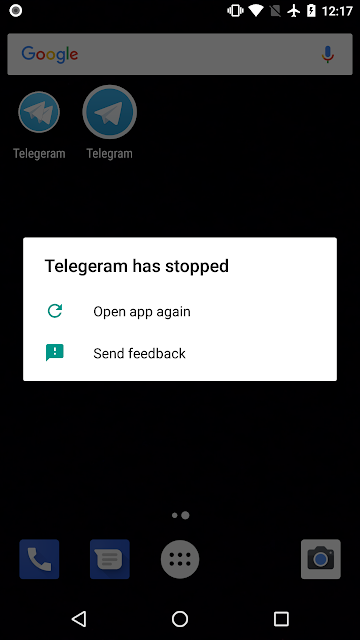 |
| Fig 5: Fake app fail. |
Conclusion
Telegram is a popular app with 200 million users, according to its own reports. But with the confusion brought about the actions of the Russian government, bad actors have seized an opportunity to present an app that may trick users searching for Telegram into downloading a malcious app. This technique is often used when an app is popular (see Pokemon GO) or, in this case, in the news.
Fake versions of popular apps are an ongoing problem, and once such an app has been downloaded on a mobile device, it is easy for the developer to open a gateway for more downloads and installation of malware.
Users should always take appropriate precautions before installing any app, even in trusted stores like Google Play or Apple App Store. One effective precaution is to read other users’ reviews before installation.
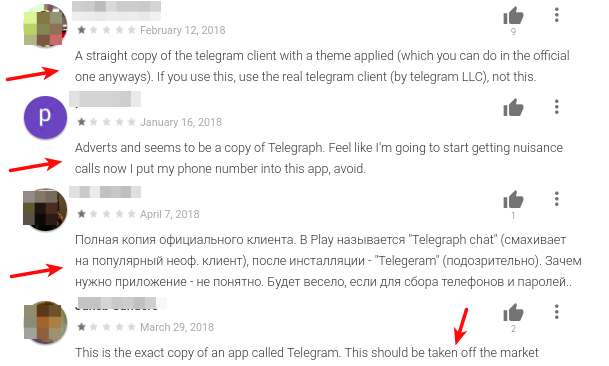 |
| Fig 6: Google Play reviews for fake Telegram app |
ThreatLabZ will continue to track and ensure coverage for fake Android apps to protect Zscaler customers.





