| Lethic Bot URLs |
| 155[.]133.18.45/nut40a361.exe |
| 155[.]133.18.45/dq40a361.exe |
| 155[.]133.18.45/dqfjr73.exe |
| 155[.]133.18.45/85fjr73.exe |
| 155[].133.18.45/112fjr73.exe |
Installation
 |
| Creating Path For Dropping File |
- “HKEYCURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”
- “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce”
 |
| RunOnce Key Created |
- For a 32-bit CPU architecture, it attempts to get the handle to the existing explorer.exe process and injects a malware module into it. It executes the injected code by calling “CreateRemoteThread” and terminates itself.
- For a 64-bit CPU architecture, it creates a new explorer.exe process in suspended mode and then injects the malicious code into it. It follows this method if the processor architecture is x64 (AMD or Intel) or Intel Itanium-based.
 |
| Function to get the path of explorer.exe |
 |
| Command from C&C server |
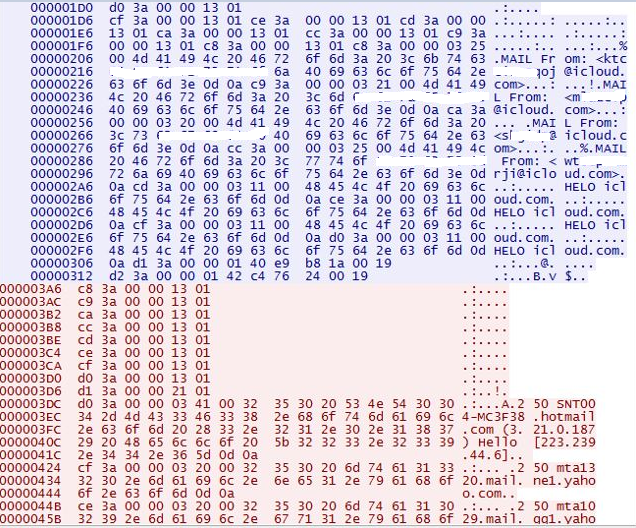 |
| SMTP proxy traffic |





