Remember Stuxnet? Chances are you do- a few months back there was a worm that spread over USB using the 0-day .LNK vulnerability (CVE-2010-2568) and targeted Siemens SCADA systems. Additionally the rootkit package that it installed was digitally signed using real certificates from real hardware manufacturers: Realtek Semiconductor Corp. (realtek.com.tw) was one of the companies (JMicron was the other - both are Taiwanese companies).
In recent days, I have seen malware with Realtek Semiconductor Corp. signature information. Specifically, it has been of the Trojan Lethic / Ddox malware family. About a year ago, Jose Nazario detailed his analysis on the Lethic bot being used to spew pharma, replica, etc. spam. About a month after he posted his analysis, M86 reported on the Lethic botnet takedown. Well it appears that there is a new variant / botnet of this malware family:
Here are two recent samples:
MD5: 0460d89f0091d951184a8d77c6641340
First seen: 2010-10-31 17:42:29
VirusTotal Report
MD5: ddb7aee9b335f479e0e2ac7aaf223856
First seen: 2010-11-07 09:58:39
VirusTotal Report
Both have Realtek information reported from Microsoft's Sigcheck tool:
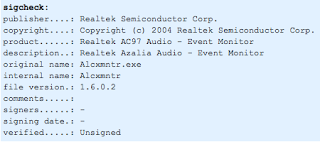 However, the tool shows no signer / certificate authority verified the signature. Here is a snapshot of the Stuxnet signcheck output for comparison:
However, the tool shows no signer / certificate authority verified the signature. Here is a snapshot of the Stuxnet signcheck output for comparison:
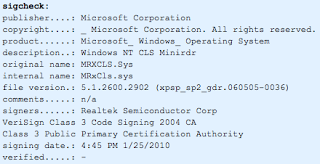 Stuxnet and Lethic are completely different, and I am in no way presuming that one or more authors behind either malware campaign intersect - I did think it was interesting that this one company is being "picked" in malware campaigns though.
Stuxnet and Lethic are completely different, and I am in no way presuming that one or more authors behind either malware campaign intersect - I did think it was interesting that this one company is being "picked" in malware campaigns though.
There may be some correlation with the exact Realtek information in the Lethic binary. The information within the Lethic binary does appear to mimic valid Realtek information for their AC97 Audio product. Doing some searches, I've found other malware families have used this exact Realtek information within their malware binaries. Here is a VirusTotal report from an SDBot sample first seen in January 2010, that has the exact same Realtek information used by Lethic. Separate malware authors could have simply selected a legitimate software package and included the exact information - however this does seem pretty coincidental. Or perhaps it could be the "signature" of a common author or group behind these artifacts - perhaps they seek to tarnish the reputation of this Taiwanese company for personal or political motivation - who knows?
There are about 91 Lethic samples with the "Realtek" signature information that Google shows from VirusTotal. These date from early September to present.
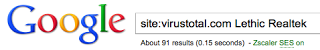
In the past few days, locations that I've seen the Lethic bot spread from include:
77.79.9.174 over port 17678
85.17.58.165 over port 36182
91.121.175.219 over port 16512
The port location changes over time, and rotates through funky sounding executable names that appear to be auto-generated from various letter permutations. For example:
bknx.exe
fewfdewwe.exe
fefewwew.exe
rfvmimikwe.exe
vgewfwqwq.exe
vgrwvew.exe
Following infection, connection attempts have been seen to:
izuhjsn.com (173.236.56.218) on port 8706
xkihjhx.com (67.159.45.104) on port 2904
The domains were both registered August 1, 2010 through the Registrars:
BEIJING INNOVATIVE LINKAGE TECHNOLOGY LTD. DBA DNS.COM.CN,
XIN NET TECHNOLOGY CORPORATION
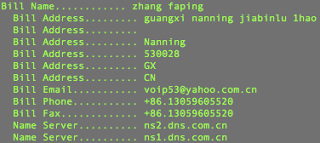 |  |
DomainTools shows 12 other registered domains with the "voip53" Yahoo email address and 62 other registered domains with the "dfghddf" Hotmail email address within the whois information - presumably other malicious / C&C domains.
In mid-October, an Anubis report shows a "Realtek" Lethic sample looping through a number of SMTP proxies/open-relays and sending spam similar to the pharma, replicas, etc. that Jose had reported in the previous 2009 iteration of the botnet. Here is a pcap snapshot of a replica spam message sent from the recent, Fall 2010 iteration of the Lethic bot:
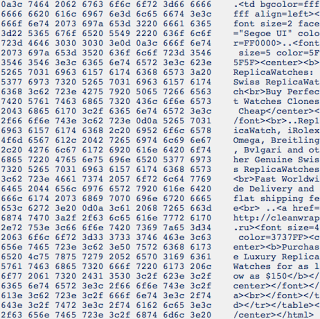
El Reg recently reported on how prolific the Lethic botnet was and the success of the takedown... could it be ramping up to make a come back? Also, can this "Realtek" signature info be used to tie the author/group to the malware they have released?
Update:
The Sigcheck tool apparently parses the PE File Version Info data structure and includes this in the output. The above "Realtek" information is actually extracted from the PE File Version Info data structure (e.g., here). While this is not a digital signature- it is still identifying info that may be able to tie certain malware samples to the same author / group / or binary builder.




