The following are known drop points for this threat:
- hxxp://69.64.70.25/301940a6b4673c67bd421220bb092fdc/justice-corresponding.php?zf=322d305457%26Be=2g55562e312f2j2j3155%26N=2d%26WT=L%26pP=i
- hxxp://corp-firewall.com/6.exe
- hxxp://66.11.227.108/0c3dcf60e6a7a6d2821831740af2cd59/optimum-bi.php?Jf=7172407038%26Ve=3b707139413a3e3e4170%26u=38%26sE=R%26q%29=w
- hxxp://main-firewalls.com/6.exe
- hxxp://main-firewalls.com/6.exe?
- hxxp://lessnvanor.info/calculator.exe
- hxxp://173.201.34.30/fabba93c6d389652ec249d95d79b9a43/connecticut-session.php?m7d%29-7-7g=8ew68aw68d%26-%21009GrVe=w88c8dw6wdw7wbwbwd8c%26h__%28D5V%2A_VI=ww%266U1P%2AJ0C9O%2A_V%21B=aGP%2Al%21FY%2A1_81%21C%26C8%21-N6%2AN=8y%2A%2AJk_%288XR_
- hxxp://216.224.186.70/setup.exe
- hxxp://61.152.158.37/da4fc29e32968439fd700e495d4e8903/instructors-spectrum.php?110b00aab11a001bba=-h-z76-b-e%260ba1a111a0b=-b7677-9-g-z-e-e-g76%26a0bab000ab01=-y%260bba0b01b1a00b1a=100a1a0100b110%26ba00aab0101ab1=11aab0b1bb10
- hxxp://193.106.172.140/index.php
- hxxp://174.70.149.96:35618/5239438/u491236/index.php
- hxxp://50.88.254.49:35618/ci5Xud?feVStUWVtcBMjoAOg=qLPueIKdPtnm&KNXWYseFaHCidA
- hxxp://80.15.218.122:35618/8DVQ6mm?xKKolchGvVMvI=SfipwkaWliPWrc
- hxxp://50.88.254.49:35618/OGbJfx1ro?yXvViVNepTrkRlNJ=AwqRMHHpLqJXAD&qagYnRxnYQYSpIEcB=lFAIbxdmjHO&eFTsEVSmSYpCtMbdm
- hxxp://68.102.186.119:35618/618342/d4921412/index.php
- hxxp://50.88.254.49:35618/UkMlaX?FpvxpKdwTaBxKVBD=kkEAvywTFQIBomL&BDKBeMIRwgNa
- hxxp://50.88.254.49:35618/KrU1qi1nu?SmjxtvpdphspkM=mxBoWXdFowVQLbm&PwkjWlqBMyBEf=qqePnpwIekn&YddGxrkSWPJgfe
- hxxp://68.102.186.119:35618/618342/d4921412/index.php
- hxxp://68.102.186.119:35618/jTORvR4mk?UkJmcNFNATO=NNpFbHCwxSRrRAHc&kIhIDgpeUOl=ILTtrQjWgYYOfAgJk
- hxxp://78.167.119.210:35618/3W7a8ph?AMhxEPvNUERWTHOK=oykAeQgptMTkJ&YxYLAodNKB
- hxxp://87.160.74.191:35618/suFTmE?FjRJTTyREjklwuELn=fSqlGVwMPjOin&bfGborcmWbla
- hxxp://96.58.105.16:35618/3Pkppd?osWurwLDMTivWmgac=xvxKVqTCeXfNBDuqe&YVkeMBlqIHTwg=rnTHuVwBKUMfjDVi&KOdCbidxJEVB
- hxxp://68.102.186.119:35618/cuw8y2?kwLQWFDmiQVKYmo=roVUdIwlxngKeJ&ilPweGjCVPFi
- hxxp://70.90.19.69:35618/618342/g1048234/index.php
- hxxp://109.29.222.118:35618/7x9pkn?KOwQrSdXnqXdAgJAA=FnHRwvBPgcIXuDA&rkWmaTRhJcWGAXtF=rnwXgTDkUrVXmfJdi
- hxxp://107.213.251.143:35618/618342/h491274/index.php
- hxxp://96.244.246.64:35618/493247/i423479/index.php
- hxxp://74.71.202.23:35618/493247/i423479/index.php
- hxxp://67.87.103.199:35618/493247/i423479/index.php
- hxxp://69.92.46.228:35618/tY0pcd?soRLbxjFdVCeo=YjcGWaFpmwdyG
- hxxp://68.118.249.206:35618/4Jdbqg5xi?UPrmDhcakwJtH=uHicfgSQWPsLJVa&uqHNsOpuWIEUKSQf=wqQOkoPieCTVsj&EuYAbtgNJHxoj=fYFukcVftXpEWOL
- hxxp://69.92.46.228:35618/O2Wgky1ex?sKhnFBxHVOsAg=ArsWCCCVkgevlo
- hxxp://64.251.129.122:35618/IFmZnn?LhnRHjJjcBP=YhfseyodnwkJi&NkAEOSEPXxUvwFan=orpPSnPiuFDuk&NeIxkIOJpWkH
- hxxp://24.237.39.65:35618/5923/u82364286/index.php
- hxxp://69.92.46.228:35618/SHPdiz?EApYkqAbAlYxWkG=jvBlaYDMbla
- hxxp://24.151.47.183:35618/i2dBru5br?WOvpdgXBvbjRAI=lghnceNceN&vIBagHuAExoRd=eCYwmudMPJoyXsaj&RouLOdQJEXYJEJ
- hxxp://69.92.46.228:35618/OKlHrt?wpOcUyyXtpGXCdFj=RJOWxyDOepMWDG&cDAbmAKpjg
- hxxp://78.112.119.85:35618/5923/j41824612/index.php
- hxxp://76.100.9.18:35618/PUU06dl?mUlCxcKquOICm=rMOvgjltEicp
- hxxp://72.218.201.207:35618/nfCdkN?tOKAOFdkuIre=slKVYfIUkDpnM&OqnMeKxfwdyCQJ=wUGxeQRcvtDMwIoj&NpyeBDYjrurEkfc=sWJWvGdFTOkRAD
- hxxp://173.30.185.44:35618/s6fjdU?UgFIrOJJWsjmQo=HmgyBypGXbTwHKL&UHqwbRQgtNcnCfsO=amBRUJFjWSdqagRyj
- hxxp://68.82.210.42:35618/Igchv87fj?uNytyqkbJTVXEaBLH=aGnHwxpDNVcUReQf&uxLwEfRGPLBm=CmNinWfybrpgRj&EoOhaxhdbID=dSdbmpJOAj
- hxxp://68.82.210.42:35618/FJEE7rn?qiXtdIHxpFmGE=KsmiFMHufteqwVd&dVOoTpCMVBDQm
- hxxp://72.82.61.239:35618/36414/g977123/index.php
- hxxp://173.30.185.44:35618/AHA24?VwweLQojXjqRbIi=KQIGDkFqLvGD&MVhIYJPKADM=fCeuCMPJGsmH&KBFYwYDElgmTTtHxe
- hxxp://81.139.129.74:35618/36414/j481261/index.php
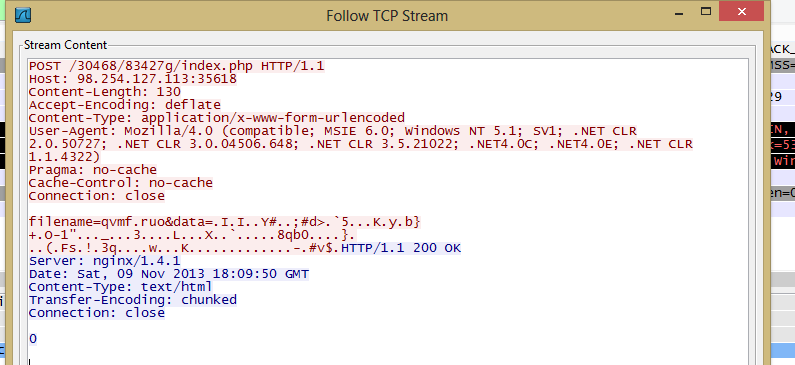
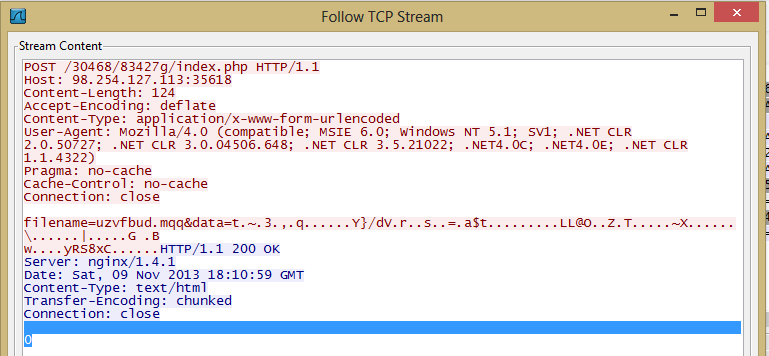
- hxxp://98.254.127.113:35618/30468/83427g/index.php
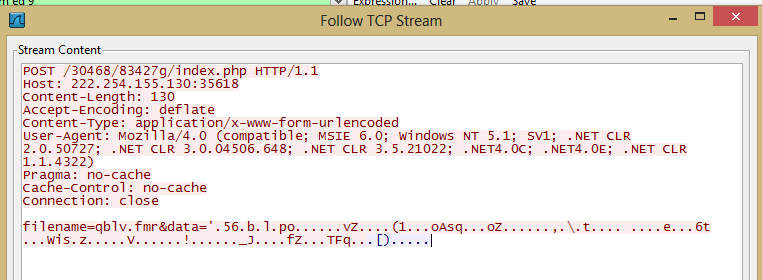
- hxxp://222.254.155.130:35618/30468/83427g/index.php
The main function of Sharik is to leave the victim open to further infection. To do this, the infection will set up a backdoor and communicate with it's CnC. The attacker can choose to attack the victim further later on. The standard communication between the victim and attacker appears to take place on a non-standard port 35618. Given the high volume of variants of this threat, it is advised to close this port or at least monitor it for suspicious activity.
It should also be noted that many of the above mentioned download locations are involved in other threats. For example, main-firewalls[.]com is very closely related to Nymaim ransomware. Another example is the md5, 771cc060cf15fc29290a0109c1cf7669, which is a Fareit variant. So what is a ransomware application and a FTP stealing trojan doing displaying the same phone home activity as a resilient backdoor Trojan? This activity hasn't been tied to on specific group at the time of research, but administrators and users should be on notice. Where there is smoke there will inevitably be fire. So if you suspect you or the users you are responsible for are seeing HTTP traffic like the above mentioned, then it definitely merits further investigation. Mind your clicks.