The talent over at MalwareBytes wrote this week about a Zbot dropper which comes from a PDF exploit through a spear-phishing e-mail. In their blog, they discuss how a spear-phishing attempts to exploit either CVE-2013-0640 or CVE-2013-2729. User's must be extra cautious dealing with any attachment in an e-mail, but this threat merits extreme concern. It installs a very persistent rootkit and logs the victim into a botnet which receives new commands/tasks every 10 minutes. Removal is near impossible and also will use your Windows Mail to spear-phish your contact list.
As noted by MalwareBytes, attackers often use false extensions in order to infect victims (such as totally_legit.doc.exe). In the case of this attack, victim's download and click a malicious PDF. This PDF, as Malwarebytes mentions, exploits Adobe Reader 11 and downloads an executable file. At the time of research, 18/51 AV companies saw through this ruse and blocked the content before it had a chance to further exploit the victim.
We obtained a copy of the same malware in the Zscaler cloud and noted the following observations. A dropped file immediately connects to a Russian IP address to set up its beaconing activity as well as download more malicious PE files to the victim's machine.
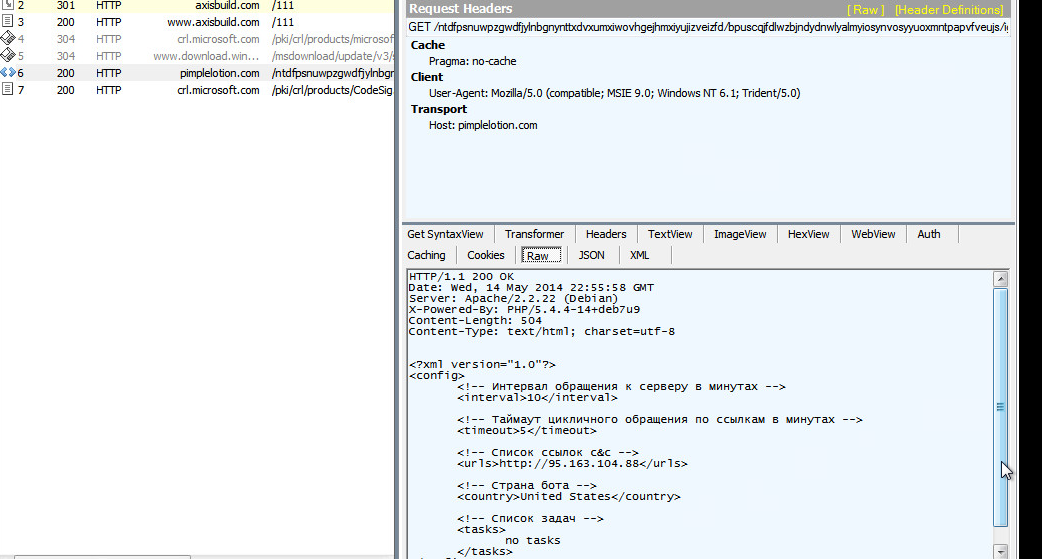 |
| axisbuild[.]com is showing some suspicious activity besides beaconing. |
The translation of the C&C configuration file seen above in English is:
In addition to awaiting for further commands from a remote server, the threat will also make many edits to the vicitm's system in order to remain despite removal processes.
There are several locations where this threat might download additional malicious PE files. I've added a brief list below to illustrate. I will provide more upon request to interested security professionals.
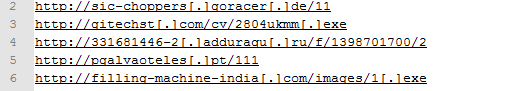 |
| There are other locations used to download malicious files. |
We took all different versions of these files and combined the phone home traffic to give a full list of IPs contacted. The dropped files immediately begin to contact various IP addresses using nonstandard ports. The following is a list of IPs and their hosted country.
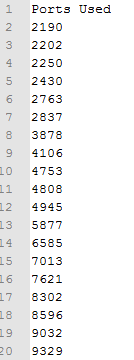 |
| List of nonstandard ports used by all variants. |
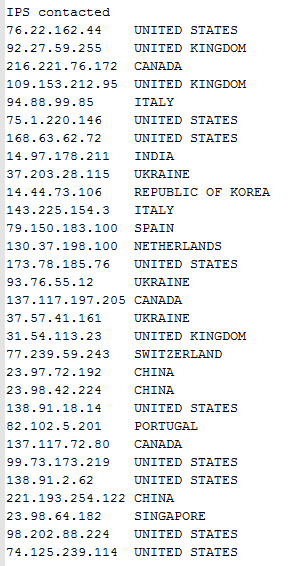 |
| List of IP addresses which were contacted across all variants. |
Administrators should monitor their networks for any activity which might match the outgoing transactions above. Administrators will have a really tough time removing the threat due to the creation of a rootkit and altering the system's boot sequence. The Zbot variant maintains a high level of persistence by doing the following:
 |
| This allows for untested drivers to be executed as part of the boot process |
- Uses bcdedit to modify the Windows boot settings.
 |
| Dropped files create a system driver which executes during boot sequence. |
- Spawns drivers in the Windows Directory
 |
| The Autostarter value is randomly generated |
- Creates an autostart registry key
 |
| Used to inject malicious process into kernel. |
- Registers kernel notifiers (kernel callbacks)
 |
| The victim is used as a node in further spear-phishing campaigns. |
- Manipulates Windows Mail files
Users and Administrators must take extra caution against suspicious attachments. Common methods for APT infection include tricking users to go to a compromised website or downloading something malicious through an attachment. The fact that this threat compromises Windows Mail files means that the victim can be used to attack your contact list. This allows for the attack to circumvent spam lists and base protections employed by regular users. The best solution is to employ a sandboxing solution against all files which come through e-mail.





