Firesheep highlighted once more, the problem of session sniffing. Users on open wireless networks are especially at risk when they login to websites without SSL encryption. But not all wireless networks are the same when it comes to sniffing traffic...and wired LAN networks are not 100% safe either.
 |
| Firesheep found user sessions |
Wireless networks
Firesheep was released to demonstrate the inherent weakness that session hijacking can present on wireless networks. They are several types of wireless networks, some are safe, but most are susceptible to session theft.
Open networks
Open wireless networks are becoming more and more popular. They can be found in public libraries, coffee shops, book stores, etc. Anybody can connect to these networks and no password is required. An attacker simply needs to be physically close enough to the wireless signal to steal unencrypted sessions.
WEP
WEP networks are protected by a password. These networks are often used in hotels to restrict Internet access to paying customers, but the password is the same for everybody. If the attacker knows the password, the network is as unsafe as an open wireless network.
It's generally very easy for an attacker to get the password without being a real customer (just ask another user for the password and you will likely get it). However, knowledge of the password is not necessarily required, as WEP encryption has been broken. There are tools freely available to crack the password.
WPA-PSK/WPA2-PSK
Unlike WEP, WPA negotiates a different key with each client to encrypt the traffic, but like WEP, WPA/WPA2 PreShared Key (PSK) encryption has been cracked as well. Somebody with enough security knowledge can determine the shared key, and sniff the HTTP sessions.
WPA-Enterprise/WPA2-Enterprise
These extensions built on the WPA/WPA2 protocols have not been cracked. Unfortunately, those are not often found or personal wireless equipments.
Wired networks
Wired networks are not necessarily safe. As with a wireless network, the type of technology used has an impact on the likelihood that traffic can be intercepted.
Hubs
If hubs rather than switch are used to connect computers, session sniffing is easy. Hubs send network traffic received on one interface to all other interfaces. This means that anybody connected to the same hub receives everyone else's traffic. Hubs are not used in many enterprises because of the security issues they represent, as well as their performance issues. However, they are cheaper that switches, and thus, can still be found in home or SMB networks.
 |
| Hub: traffic is replicated to all ports |
Switch
Switches are more efficient than hubs: the network traffic is forwarded to one interface only. In theory, session sniffing is not possible on these devices. However, it is quite trivial flood a switch in order to make it behave like a hub. This flooding would probably be noticed in a company with a good IT department monitoring the internal network, but not necessarily in smaller companies.
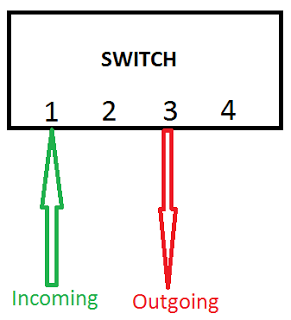 |
| Switch: traffic is forwarded to one interface |
Monitor port
Most enterprise-grade network equipment (switches, routers, firewalls) has a monitor or mirror port: all traffic seen by the switch is mirrored to this interface. Anybody with physical access to this port can sniff traffic from the entire network. Unlike the case of flooding a switch to make it behave as a hub, this would not create any unusual network activity, and could not be detected.
Don't trust your network! Wired LANs are safer than wireless networks in general because they require physical access, but they are not 100% safe. To be sure that you're the only one accessing your accounts on the web, make sure you use SSL: use HTTPS only, or use an SSL VPN.
-- Julien





