Proactively discover and remediate data and AI risks
Find and protect sensitive data across hybrid and multicloud environments with fully integrated, AI-powered data security posture management (DSPM).

Automatically discover, classify, and inventory sensitive data
Accurately identify and correlate risks such as misconfiguration, exposure, and more
Proactively remediate risks and apply least-privileged access control
Ensure data and AI regulatory compliance and streamline audits
The Problem
Data is the foundation of AI and modern business initiatives. However, its explosion across hybrid, multicloud environments has left organizations with blind spots. As a result, companies struggle to understand where their sensitive data is, and related context such as security posture, access entitlements, and compliance risks, opening them up to data risks.
#1
80%
66%
Solution Overview
Secure your data universe
Zscaler DSPM takes an AI-powered, unified approach to ensure strong data hygiene across all data stores, including IaaS, SaaS, on-premises, endpoint, and more. Natively integrated with the Zscaler Data Security platform, it enables you to fully understand and control all your data on a single platform.
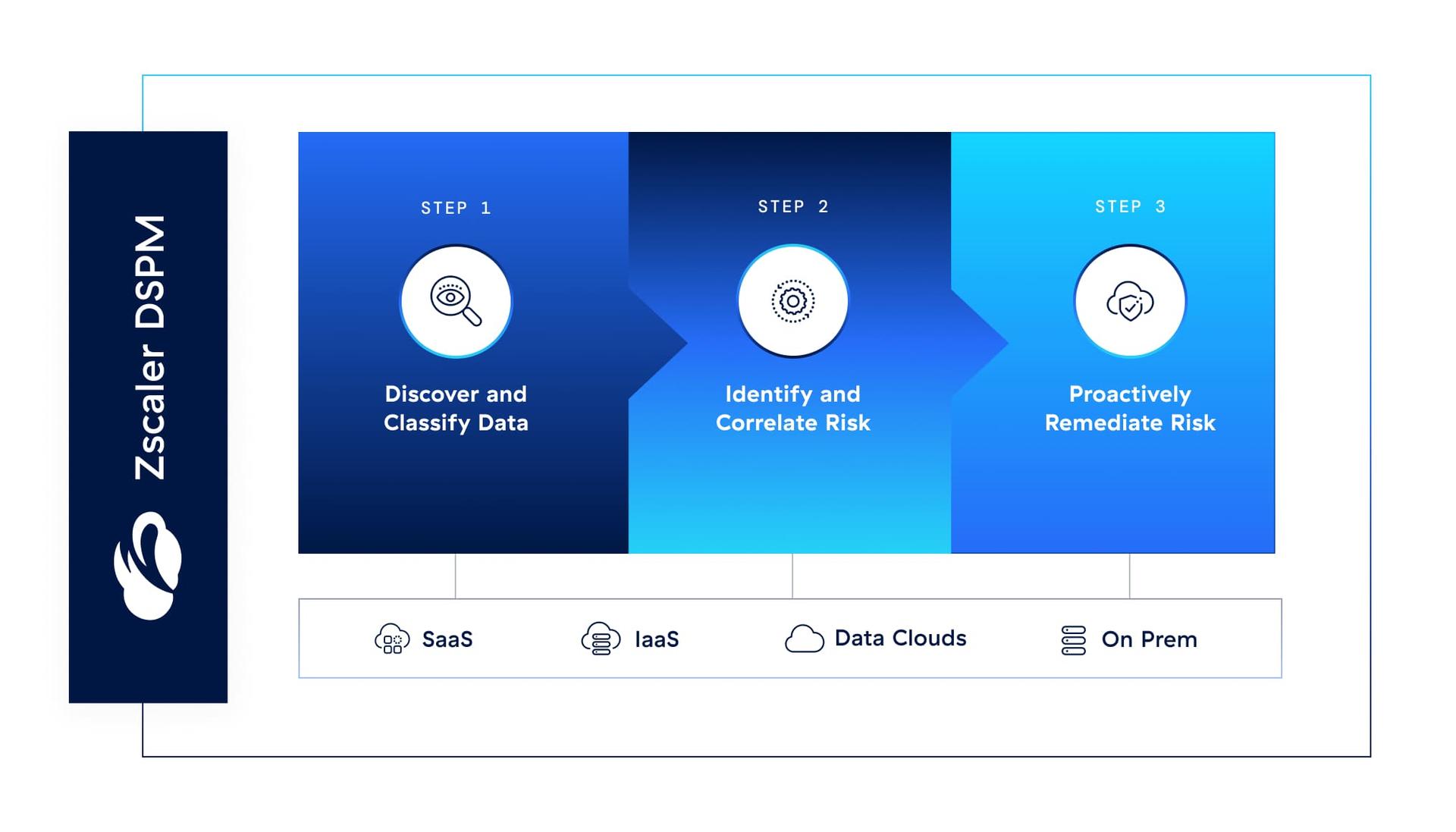
Use cases
Discover and classify data
Understand your entire data universe across structured and unstructured data within IaaS, SaaS, on-premises, endpoint, and more, all in one unified dashboard.

Capabilities
Find all sensitive data across all channels, including shadow AI, with AI-powered auto-discovery.
Accurately classify and categorize sensitive, regulated, or custom data using advanced LLM classification.
Automatically inventory your data to understand storage locations, access, usage, and more.
Efficiently manage your data's security posture
Give your security team deep visibility into the security posture of your data stores. With greater context, you can more accurately identify risks to minimize alert overload using AI-powered threat correlation that uncovers hidden risks and toxic combinations.

Capabilities
Get deep visibility into the security posture of your data stores containing sensitive data, including encryption, exposure, logging, backup, certificates, and more.
Accurately pinpoint and correlate risks such as data exposure and misconfigurations to reveal hidden attack paths using our AI correlation engine.
Leverage in-depth, precise risk scoring to filter out the noise and prioritize top risks, saving valuable time and resources.
Manage and remediate data access risk
Identify users, roles, and resources with access to data stores, and track privilege levels. Detect excessive or inappropriate access, prioritize risk remediation efforts, and enforce least-privileged access to reduce your risk of a breach.

Capabilities
Get a granular, risk-based, user-centric view over all access paths to mission-critical data assets and their configurations.
Minimize the attack surface by remediating overprivileged users and risky access paths to sensitive data.
Keep up with rapid changes to data access and its environment, and respond to potential threats.
Manage regulatory compliance
Seamlessly comply with complex regulations and standards like GDPR, HIPAA, PCI DSS, NIST AI RMF, and more. Flag violations and create real-time reports to attest compliance and avoid penalties, regardless of data residency.

Capabilities
Get complete visibility into your data compliance posture with a dynamic view of compliance status, configuration drift, and policy violations.
Automatically map your data security posture to compliance benchmarks and best practices to assess gaps, understand their impact, and reduce manual effort and errors.
Leverage comprehensive compliance data, analytics, and automated reporting for technical compliance audits. Get a drill-down view of compliance issues to help prioritize risks and remediation.
Accelerate secure AI adoption
Leverage complete visibility, accurate classification, and granular control over sensitive data used in AI cloud services. Prevent accidental exposure, overly permissive or unauthorized access, and potential AI compliance violations.

Capabilities
Discover all AI models, services, and agents in the cloud and eliminate shadow AI risks. Understand which sensitive data is associated with which AI service to prevent oversharing of training data sets and data poisoning.
Evaluate AI systems against operational, regulatory, and reputational risks to ensure compliance with current and upcoming regulations.
Deep-scan AI models for vulnerabilities across the OWASP Top 10 for LLMs. Pinpoint vulnerabilities, misconfigurations, and permissions, and remediate with step-by-step guidance.
Help build trust among stakeholders and customers with AI-SPM by ensuring secure and compliant AI systems, demonstrating a commitment to ethical AI.
Mitigate your data risk with Workflow Automation
Rapidly address critical data risks such as exposures, vulnerabilities, misconfigurations, and more with guided remediation and automated workflows.
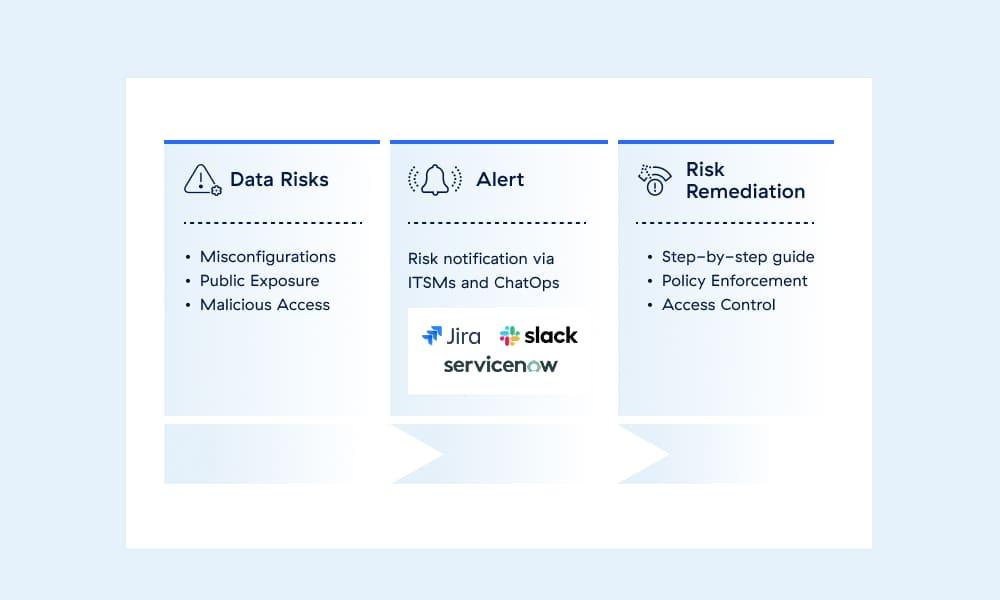
Capabilities
Ensure best-in-class data security everywhere, from endpoint to email, SaaS, public cloud, on-premises, and your AI ecosystem.
Empower your users with frictionless experiences across teams. Automate time-consuming and repetitive security tasks to become more productive and efficient.
Easily integrate with the most effective ITSM, operations, and developer tools.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
FAQs
DSPM works to protect data—both local and in the cloud—against unauthorized access, misuse, or theft by continuously monitoring, updating, and refining security measures. DSPM solutions use intelligent automation to identify vulnerabilities, enact safeguards, and perform regular system tests and audits. Learn more.
Cloud DLP monitors and inspects data on a network to prevent data exfiltration stemming from cyberattacks like phishing, ransomware, and insider threats. Deployed from the cloud, cloud DLP can protect sensitive data such as PII, credit card numbers, intellectual property, and more, wherever it lives or flows. Learn more.
AI-SPM secures AI systems through visibility into resources, evaluation of security controls, and detection of threats like model stealing and data poisoning. It supports regulatory compliance and helps organizations reduce risks, strengthen security, and address vulnerabilities quickly, ensuring their AI deployments are reliable and trustworthy.
Request a demo
Proactively secure your mission-critical data with agentless, AI-powered DSPM.


