Transform your workload security from firewalls to zero trust
Achieve consistent threat and data security
Eliminate lateral movement of threats
Reduce costs and complexity vs. legacy architectures
The Problem
Navigating security in a multi-cloud environment is complex
Securing modern workloads isn’t easy.
- Applications run across multiple clouds, regions, and availability zones.
- Diverse traffic paths connect workloads to the internet, and private and public apps.
- Mission-critical applications must be microsegmented and safe from attackers.

Every internet-facing firewall is an attack surface
Private networks enable lateral movement
Managing security across multiple cloud providers is complex
Solution Overview
Enable superior cloud workload security with Zero Trust Cloud
Secure all workload traffic in one place with our cloud native zero trust platform. Protect everything from ingress/egress and east-west connections to granular micro-flows across any cloud, all with a consistent security model.
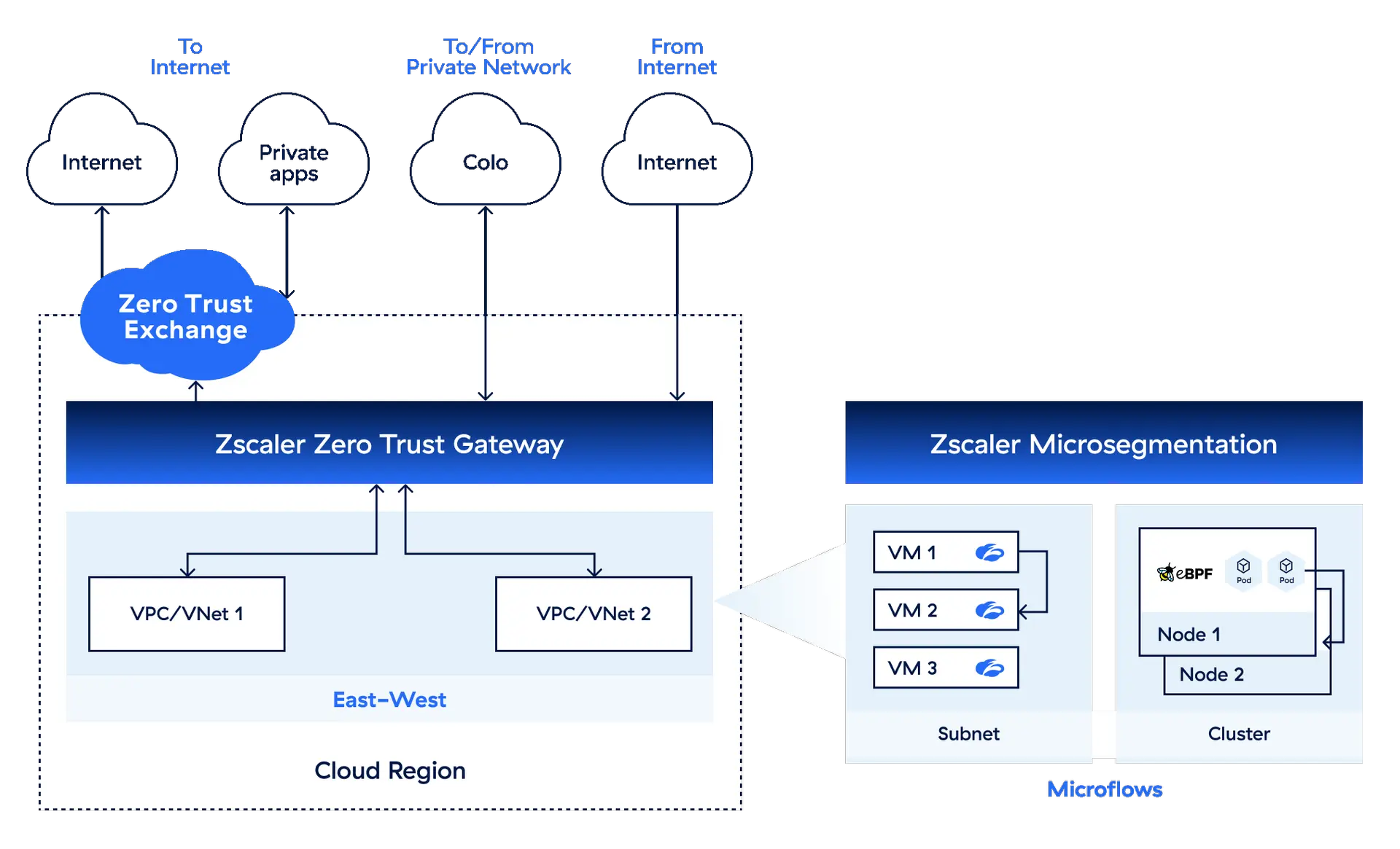
Benefits
Unify security for multi-cloud environments
Enforce consistent, comprehensive threat and data protection
with standardized security control across multi-cloud environments.
Eliminate lateral movement and the attack surface
with segmentation between and within clouds, VPCs, and VMs.
Isolate and protect high-risk applications
with granular microsegmentation.
Use Cases
Achieve comprehensive hybrid cloud workload security
Secure ingress and egress traffic from workloads
Enable secure connectivity between workloads and internet or SaaS destinations with a scalable, reliable security solution that inspects all traffic.

Secure workload-to-workload traffic
Enable workloads to securely communicate with other workloads in other cloud regions, public clouds, or on-premises data centers.

Microsegment workloads
Protect mission-critical applications with AI-powered recommendations and local enforcement.

Deployment Options
Leverage flexible deployment options
Deploy Zero Trust Cloud the way that best suits your operations: take full control of your cloud infrastructure or consume the capabilities as a gateway service.

Want to test out Zero Trust Cloud in an AWS tenant?

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
Technical videos
Dashboard and Navigation
Explore the Cloud Connector Portal, where you can access and manage your Cloud Connectors and policies.
Securing East-West Traffic
Learn to secure traffic between VPCs that are connected to security VPC in centralized model.
Securing Ingress Traffic
Learn to secure ingress traffic.
Enforcing Minimum TLS Versions
Learn how to set up policies to enforce minimum TLS versions to secure cloud workloads.
Protecting Against Malicious Payloads, Phishing, and Botnets
See the comprehensive protection Zscaler Zero Trust Cloud offers right out of the box.
Establishing a Data Loss Prevention Policy
Discover the power of Zscaler Data Loss Prevention to protect against data exfiltration.
FAQ
A zero trust architecture operates on the principle that no entities, including firewalls and VPNs, are inherently trustworthy. It continually validates and secures every workload and all traffic regardless of origin. In doing so, the architecture minimizes the attack surface, prevents lateral movement of threats within the environment, and streamlines workload security for greater efficiency and protection.
Securing workloads with Zscaler Zero Trust Cloud overcomes the limitations of traditional firewalls. Zero Trust Cloud delivers advanced threat and data protection through cloud-scale TLS inspection. Firstly, its proxy-based architecture effectively reduces the attack surface by concealing all workloads from the internet. Secondly, it prevents lateral threat movement by enforcing least-privileged access to workloads, using user-defined tags for granular control. Thirdly, by consolidating security into a single, comprehensive platform, it eliminates the need for multiple firewalls, significantly reducing operational complexity and costs.
Zero Trust Cloud centralizes and standardizes workload security management across all clouds through a single, consistent framework. It provides real-time traffic inspection, simplifies policy enforcement, and eliminates complex firewall management. This reduces operational complexity and costs while enabling scalable, flexible, adaptable security. Zero Trust Cloud secures all traffic paths in a multi-cloud environment and microsegments workloads using one platform.











