Background
A joint cybersecurity advisory was released by the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) related to an increased cybercrime threat to U.S. hospitals and healthcare providers from ransomware, notably Ryuk and Conti
What is the issue?
CISA, FBI, and HHS have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers from ransomware like Ryuk and Conti. These ransomwares have been deployed by malware belonging to Trickbot and BazarLoader/BazarBackdoor families. Cybercriminals disseminate TrickBot and BazarLoader via phishing campaigns that contain either links to malicious websites that host the malware or attachments with the malware. Loaders start the infection chain by distributing the payload; they deploy and execute the backdoor from the C2 server and install it on the victim’s machine. TrickBot or BazarLoader infection can lead to deployment of ransomware, such as Ryuk and Conti.
What systems are impacted?
All machines running Windows operating system.
What can you do to protect yourself?
We recommend making periodic backups of all the important data and keeping those backups isolated off the network. It is equally important to have updated security software and the latest software patches applied to the endpoints. Remote Desktop service access should always be restricted, or it should be turned off if not used. As always, avoid opening suspicious emails containing attachments or links that come from any unknown sources. Disable macros in Office programs. Do not enable them unless it is essential to do so. Enable multi-factor authentication (MFA) across both business and personal email accounts to thwart most credential harvesting attacks.
Zscaler coverage
- Advanced Threat Protection
Win32.Downloader.BazarLoader
Win64.Downloader.BazarLoader
Win32.Backdoor.Bazar
Win64.Backdoor.Bazar
Win32.Backdoor.Anchorbot
Win32.Banker.TrickBot
Win64.Banker.TrickBot
Win64.Ransom.Ryuk
Win32.Ransom.Ryuk
Win32.Ransom.Conti
- Malware Protection
W64/Ransom.Ryuk.A.gen!Eldorado
W32/Trojan.BVXG-5604
W32/Trojan.XFWW-7740
W64/Agent.BYF.gen!Eldorado
W32/Trojan.MLJJ-9184
W32/Trojan.DYOA-8084
W64/Trojan.QDKO-4869
- Advanced Cloud Sandbox
Win32.Ransom.Ryuk
Win32.Ransom.Conti
Win32.Banker.Trickbot
Details related to these threat signatures can be found in the Zscaler Threat Library.
Zscaler had also published detailed analysis blogs for Ryuk, Trickbot and Bazarloader.
Our Cloud Sandbox Report for Ryuk ransomware executable can be seen in Figure 1.
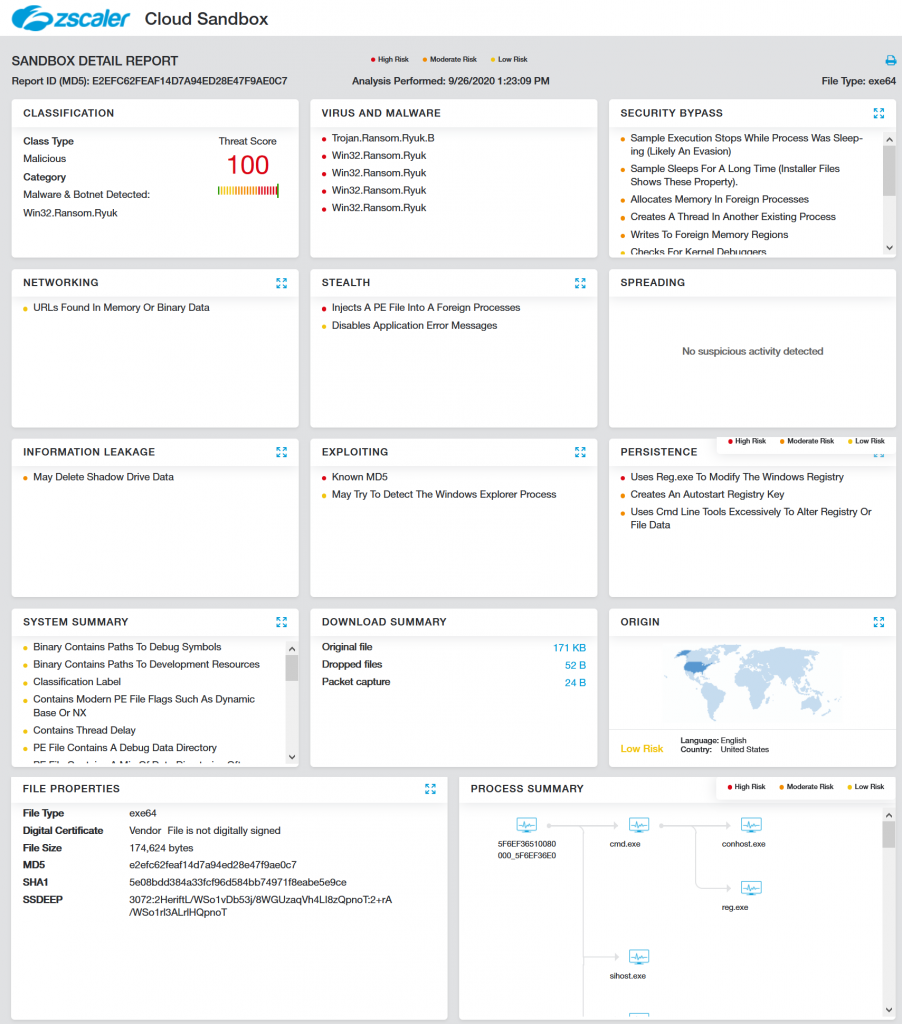
Fig 1: Cloud Sandbox Report for Ryuk Ransomware
Our Cloud Sandbox Report for the Conti ransomware executable can be seen in Figure 2.
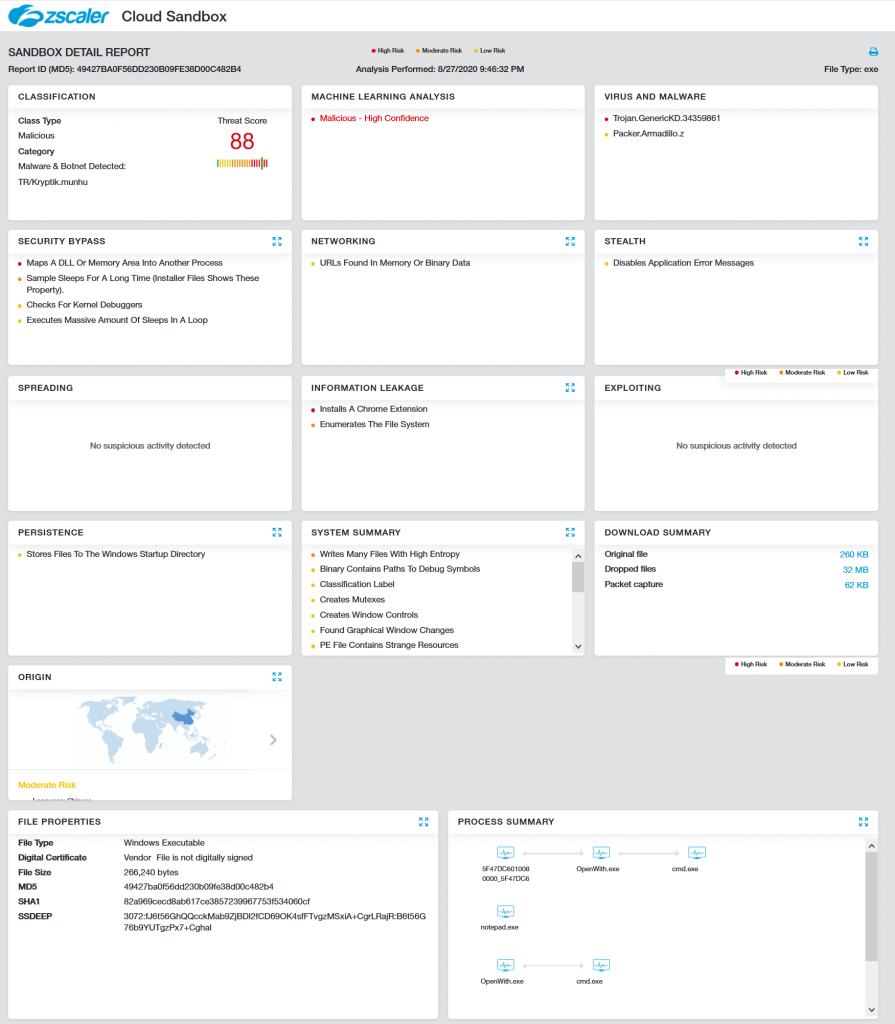
Fig 2: Cloud Sandbox Report for Conti Ransomware
The Zscaler Cloud Sandbox provides proactive coverage against advanced threats such as ransomware and banker trojans. The Zscaler ThreatLabZ team is also actively monitoring Trickbot, BazarLoader, Ryuk and Conti malware families and ensuring coverage for all the latest IOCs associated with these malware.
References
- https://us-cert.cisa.gov/ncas/current-activity/2020/10/29/microsoft-warns-continued-exploitation-cve-2020-1472
- https://www.zscaler.com/blogs/research/spear-phishing-campaign-delivers-buer-and-bazar-malware
- https://www.zscaler.com/blogs/research/trickbot-emerges-few-new-tricks
- https://www.zscaler.com/blogs/research/examining-ryuk-ransomware





