In Part I of this series, I analyzed the files used in coordination with news.php to create the malicious spam "Hot Video" pages. In this second post, I'll analyze the rest of the files found on the site:
- .cch/ - folder contains thousands of spam pages
- page.php - displays the "Hot Video" page
- .sys.php - execute any PHP code and upload files
- g------.php (censored) and a few similar pages - execute any command and upload files
page.php and .cch/
page.php is nearly identical to the script news.php described previously: it displays the fake AV pages using the news.dot template. It uses sites.txt and key.txt to get the list of other spam pages, etc. The script is also obfuscated using FOPO.
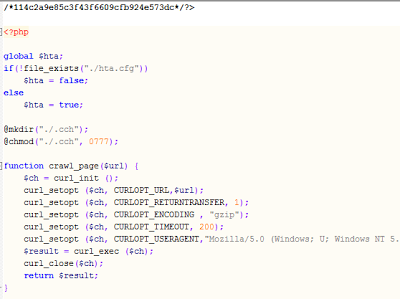 |
| Part of the de-ofuscated PHP code |
The only difference with news.php is that the spam content is stored in .cch/ instead of .news/.
The other 2 PHP scripts are not related to the "Hot Video" spam pages, but they are very dangerous for any website affected by this attack as they open it up to further compromise as discussed below.
.sys.php
This PHP script is not encrypted. It is very short, but very dangerous. It executes any PHP code entered in a POST request, and can upload any file, including .php files that can be executed on the site later.
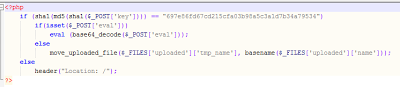 |
| Full source code |
Looking at the source code is not enough to be able to use it. Indeed, the script runs only if the correct parameter key=value is sent. The code starts with:
So you need to find the right value whose SHA1 of MD5 of SHA1 (!) is equal to "697e86fd67cd215cfa03b98a5c3a1d7b34a79534", otherwise the script does not do anything.
g------.php (censored)
I've found a few.php scripts with similar names, but always slightly different, on several hundred websites. Unfortunately for the webmasters, this means that a simple Google search can let anybody take full control of their website.
The script allows anybody to run any shell command on the site, run any PHP code, and to upload any file. It is not obfuscated, and unlike .sys.php, there is no trick to prevent people from using it. To protect the websites which have been hijacked, and now include these scripts, I won't go into further details regarding this file.
Conclusion
The scripts used to create the fake "Hot Video" pages are pretty simple. They work autonomously, so it is not possible to track the origin, or individual that may be behind the attack. Hundreds of websites have been compromised.
These hijacked sites are mostly online stores. They are dangerous not only for their users, whose information can be easily stolen, or could be presented with all kinds of malware, but for Internet users in general.
-- Julien





