In Part I and II, I analyzed files on a hijacked site that was part of the "Hot Video" campaign. While doing the analysis, I identified other hijacked domains and found additional scripts used to create the "Hot Video" pages. Some of them were much more elaborate.
page.php and page.dot
These pages present a slight variation of the "Hot Video" scripts seen in Part I and Part II. The template is loaded from page.dot instead of news.dot. Otherwise the script works the same way, however, the redirection to the malicious page is done by a different site, namely rapidejdr.fr. Interestingly, this website was already redirecting users to fake AV sites in July 2010. I did warn the owner of the site at the time, but apparently it fell on deaf ears.
trends.php
This script is very interesting. It does basically the same thing as news.php and page.php, displaying the "Hot Video" page and creating spam content, but in a different way. Checks for bots are also more thorough.
Here are the main differences:
is_search_bots()
The previous examples were only looking at the User-Agent header, to differentiate between users and bots. This version includes several other checks:
- Client IP address check - The script has a list of IP addresses/ranges which are considered to be bots. They are known Google IP addresses. A similar list can be seen at SEO-Wolf. It is interesting to see that, once again, attackers care primarily about Google, not Yahoo or Bing.
 |
| List of blocked IP addresses |
- Referer header check - If you do a search for "site:example.com", the request to the page is considered as being done by a bot
- User-Agent header check - Blackberry and Samsung browsers are flagged as bots
- Referer header must contain google or search.
- Referer header must contain q=.
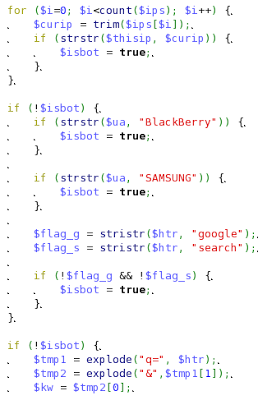 |
| Part of the is_search_bots() function |
sendPage($keyword)
The scripts display slightly different pages for bots and users. They use two templates: trend.dot for users and default.dot for bots. The differences between the pages generated are designed to trick Google into thinking this is not a spam page. The page delivered to search engine bots has the following characteristics:
- No "Hot Video:" string in the title
- The Flash overlay on the page is not created, so there is no redirection to a fake AV site
Otherwise, the content of the 2 pages is the same as detailed in a previous post: spam content, links to other spam pages, and a picture of the fake Youtube player.
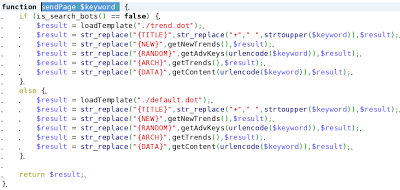 |
| The sendPage function |
getNewTrends()
This function did not exist in the previous scripts. The "Hot Video" pages include the 20 most popular searches from Google Hot Trends for the same day. This means new links to fake video pages are created automatically every day.
getTrends()
The spam page also contains links to older Google Hot Trends, taken randomly from the last 25 days:
getAdvKeys($key)
Another list of spam keywords is generated using Google Suggest, the list of suggestions which Google shows you as you type your keywords in the search engine. This means the fake pages are created not only for the popular searches, but also for searches suggested by Google.
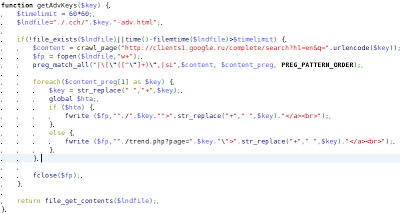 |
| Source of the function generating new keywords for spam |
Another difference with the previous script is that there is no hash done on the keywords to ensure that the request includes specific parameters.
Sitemap
As with the other "Hot Video" pages, there is a link to a sitemap page which lists other spam pages. But in this example, the sitemap is generated from the content on a different domain: byethost17.com. This page can create a list of spam pages for any domain and the base URL is sent as a URL parameter.
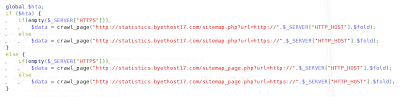 |
| sitemap.html is generated from a different domain |
Conclusion
This script looks like it was written by the same group as the other "Hot Video" scripts. However, it's functionalities are more like the other Blackhat spam SEO scripts I've seen, with extensive checks to separate users from bots, with different content displayed to each.
-- Julien





