We've seen an increase in hijacked websites in recent months, redirecting users to Fake AV pages, Blackhole exploit kits and other malware. While most websites hacked are personal sites, or University websites, some are more high profile.
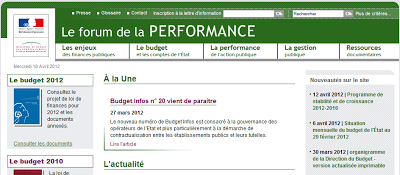 |
| http://www.performance-publique.budget.gouv.fr/ hijacked |
The website of the French Minister of Budget (www.performance-publique.budget.gouv.fr) is an example of a high profile site that was recently hijacked. Obfuscated JavaScript was added at the top of the page. It is very similar to what we have seen on other websites. The obfuscation contains some tricks to break JavaScript scanning tools, such as making reference to browser objects, exceptions, etc.
 |
| Malicious JavaScript inserted on the hijacked site |
The code creates an IFRAME to hxxp://nysbrtyjdjntytdrj7yn.rr.nu/?go=2. This address is not blocked by Google Safe Browsing at this time. I was not able to retrieve the content.
 |
| Deobfuscated JavaScript |
The domain rr.nu has been widely abused. It has been linked to the Mac Flashback Trojan, previous Fake AV campaigns, etc.
budget.gouv.fr is not the only governmental website that has been hijacked recently. In the last three months, we have seen many hijacked government sites including:
- Australia: library.cgg.wa.gov.au, ofv.sa.gov.au
- US: cityofhampton-ga.gov, sandy.utah.gov, governor.virginia.gov, letsread.cobbcountyga.gov, mississippi.gov, etc.
- Philippines: car.dost.gov.ph
- Colombia: acuavalle.gov.co, risaralda.gov.co
- Malaysia: ipharm.gov.my
Unfortunately, no website can be fully trusted anymore.




