Know when attackers exploit, misuse, or steal enterprise identities and identity infrastructure. Reduce the risk of identity-based attacks with real-time identity threat detection and response (ITDR).
Get full visibility into misconfigurations, risky permissions, and exposed credentials
Detect and respond to attacks that abuse credentials and bypass MFA to move laterally
Remediate and investigate faster with SOC workflow and access policy integration
The Problem
Identity is the new attack surface
As zero trust adoption shrinks traditional attack surfaces around the world, attackers are looking beyond malware. They're using sophisticated techniques to steal credentials, bypass multifactor authentication, and escalate privileges.
Legacy threat detection and identity systems weren't built to handle identity-based threats, leaving you with critical blind spots around risky changes, compromised credentials, and malicious activity.
50%
75%
91%
Solution Overview
Unlock identity-first security
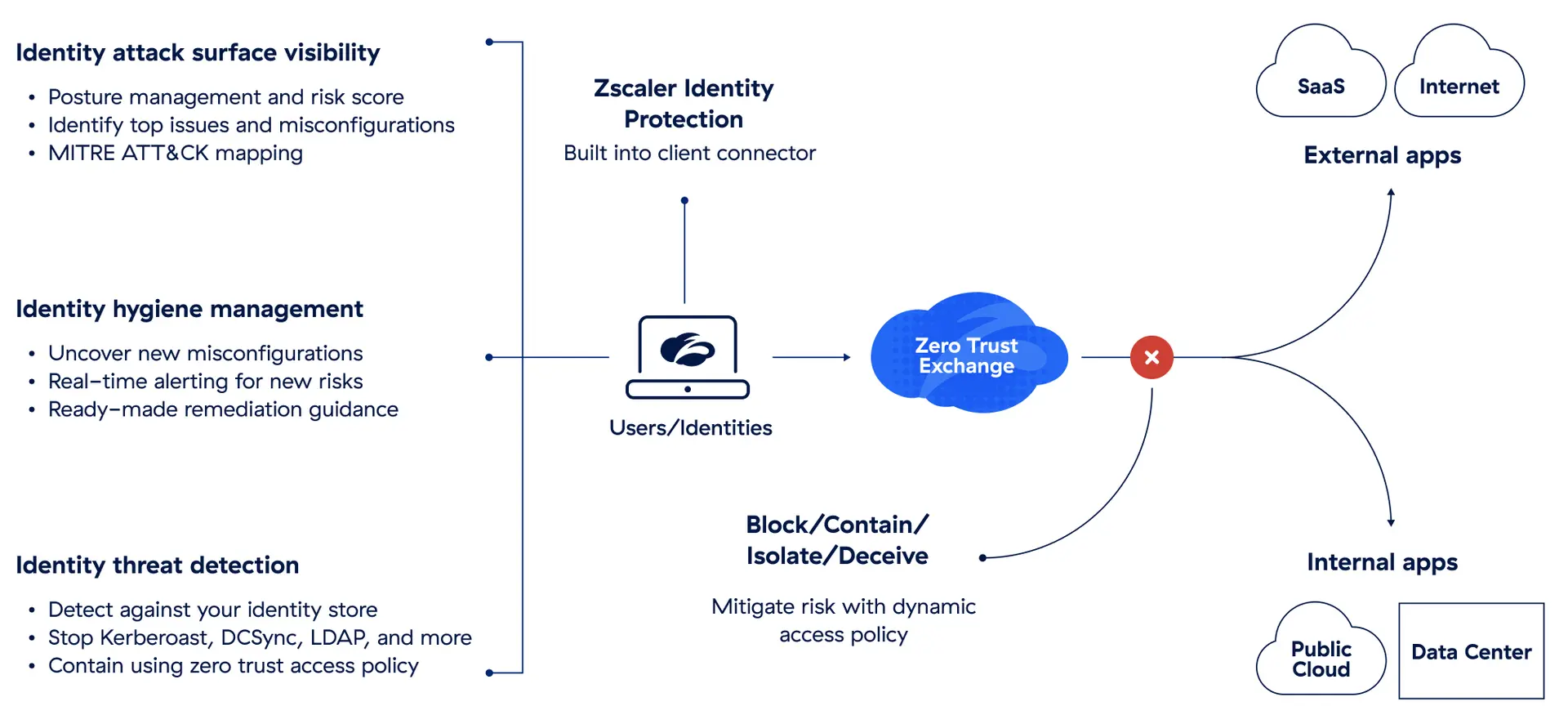
Zscaler Identity Protection protects users with continuous visibility into identity configurations and risky permissions. Built into Zscaler Client Connector, our lightweight endpoint agent, it's a simple, low-touch approach to stopping identity-based attacks.
Set up Identity Protection in just minutes, and start improving your security posture immediately. Rapid assessments and alerts give your security team valuable insights into identity-related vulnerabilities and changes that increase your risk of a data breach.
Benefits
Reduce the risk of user compromise and privilege exploitation
Quantify and track identity risk
Understand how, why, and where you’re vulnerable with identity security assessments, which include an intuitive risk score.
Find and fix risky configurations
Uncover issues that open new attack paths, such as shared password exposure, stale passwords, and unconstrained delegation.
Remediate with step-by-step guidance
Understand the issue, its impact, and affected users. Improve identity hygiene with remediation guidance in the form of video tutorials, scripts, and commands.
Monitor changes in real time
Get timely alerts when configuration and permissions changes in identity systems introduce new risks.
Detect identity attacks
Defend against vulnerabilities you can't remediate. Detect and stop attacks like DCSync, DCShadow, kerberoasting, and more when a compromise occurs.
Contain identity threats
Use native integrations with Zscaler Private Access™, SIEMs, and leading EDRs to contain identity attacks in real time or use alerts as part of your SOC workflow.
Use Cases
Comprehensive protection for an increasingly exploitable attack vector

Quantify and track identity posture with unified risk scoring. See top identity issues and the riskiest users/hosts in real time, with MITRE ATT&CK mapping for visibility into your security blind spots.

Identify new vulnerabilities and misconfigurations as they emerge. Get real-time alerts on new risks in your identity store, with ready-made guidance, commands, and scripts to help you remediate issues.

Detect attacks targeting your identity store. Prevent kerberoasting, DCSync, and LDAP enumeration attacks, with built-in containment based on zero trust access policy.

Get visibility into credentials stored insecurely across your endpoints, and clean them up to reduce your attack surface and prevent them from being exploited.

Identify endpoint credentials and AD domain passwords that have been compromised/leaked or are weak and could easily be cracked in the event of a compromise.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
FAQ
Cybercriminals exploit stolen credentials, phishing, social engineering, or weaknesses in authentication systems to access accounts and sensitive data. Once inside, attackers may impersonate legitimate users, escalate their access privileges, or move laterally across networks to steal data or deploy malware for use in further attacks.
Zero trust is a security model that assumes no user or device is inherently trustworthy, even when it is already on the network. It enforces strict identity verification, limits access to only required resources, and continuously monitors activity. This approach stops attackers from exploiting stolen credentials to move through systems undetected.
Identity threat detection and response (ITDR) focuses on identifying and stopping identity-targeted threats, such as credential theft, privilege abuse, or lateral movement. ITDR tools monitor identity systems for suspicious behavior, track anomalies over time, and respond quickly to prevent breaches or large-scale data theft.