In this blog, the Zscaler ThreatLabZ team provides details on the Maze ransomware.
Background
On April 18, 2020, Cognizant confirmed a security incident causing service disruptions for some of its clients due to a Maze ransomware attack. The Maze ransomware was first found in May 2019.
What is the issue?
The Maze ransomware, like normal ransomware, will encrypt files in an infected system and then demand a ransom to recover the files. Before encrypting the files, the Maze ransomware will also perform data exfiltration from the infected system. However, one of the important characteristics of the Maze ransomware group is that if the victims do not pay the ransom, they threaten to release the information (including confidential documents) stolen from the infected systems. The Maze ransomware uses different techniques to gain entry to a victim's machine, such as exploits kits, remote desktop connections with weak passwords, and via email attachments.
What systems are impacted?
Since the Maze ransomware binaries are .exe and .dll files, this can impact all machines running the Windows operating system.
What can you do to protect yourself?
We recommend making periodic backups of all important data and keeping those backups isolated off the network. It is equally important to have updated security software and the latest software patches applied to the endpoints. Remote Desktop service access should always be restricted or it should be turned off if not used. As always, avoid opening suspicious emails containing attachments or links that come from any unknown sources. And disable macros in Office programs. Do not enable them unless it is essential to do so.
Zscaler coverage
- Advanced Threat Protection Signatures
Win32.Ransom.Maze
VBA.Downloader.Maze
Win32.Ransom.Maze.LZ
- Malware Protection
W32/Ransom.NC.gen!Eldorado
Trojan.MAZE-4
W32/Application.MAZE-9275
W32/Trojan.MAZE-3041
- Advanced Cloud Sandbox
Win32.Ransom.Maze
Details related to these threat signatures can be found in the Zscaler Threat Library.
Our Cloud Sandbox Report for the Maze ransomware executable can be seen in Figure 1.
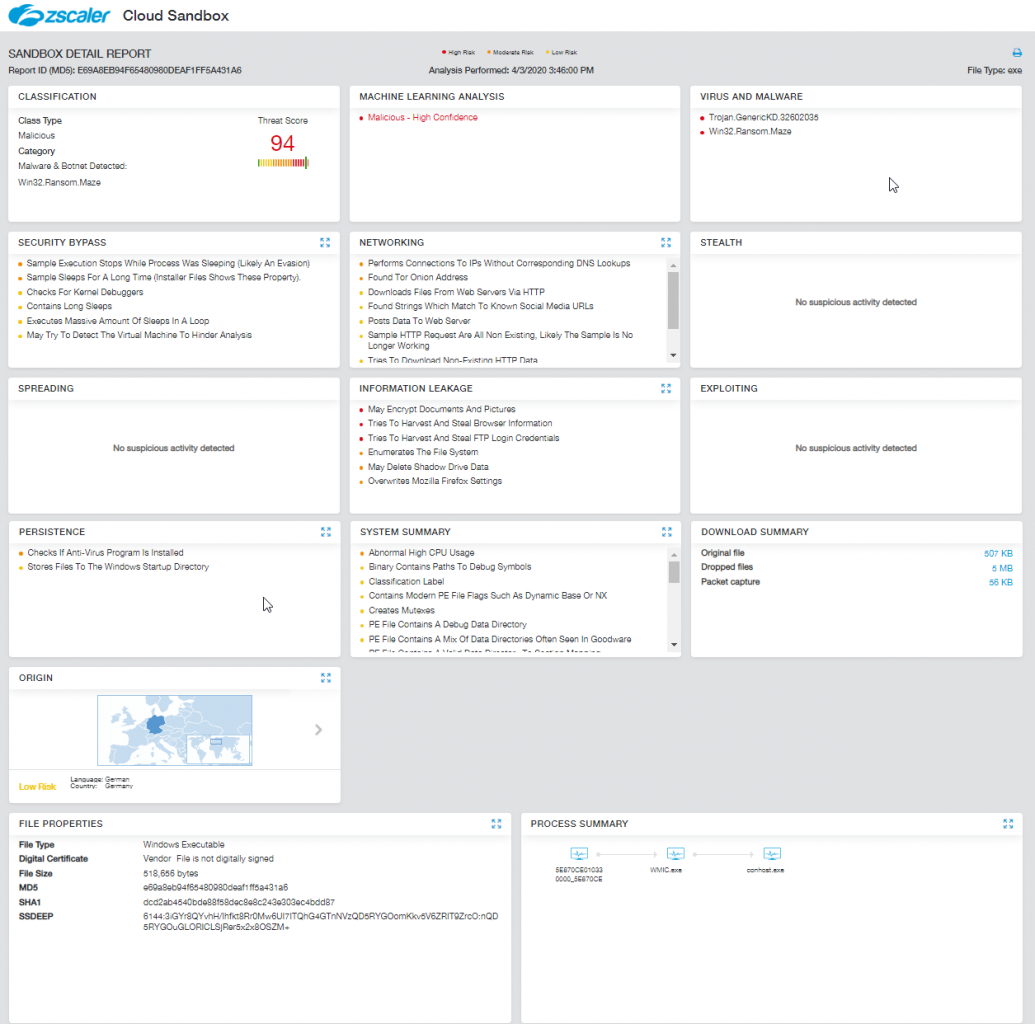
Figure 1: The Zscaler Cloud Sandbox report for the Maze ransomware
The Zscaler Cloud Sandbox provides proactive coverage against advanced threats, such as ransomware. The Zscaler ThreatLabZ team is also actively monitoring the Maze ransomware family and ensuring coverage for all the latest IOCs associated with the Maze ransomware.





