On 12 May 2017, a massive ransomware attack was unleashed and it disrupted business operations for public and private organizations on multiple continents. The ransomware is highly virulent and once a user is infected, it spreads rapidly across a corporate network.
The Zscaler team has been actively monitoring the attacks over the past 72 hours and while the initial delivery vector in this case is not over HTTP/HTTPS, we have added multiple protections to block the payloads as well as post-infection activity for this Ransomware strain as it morphs.
How WannaCry Works
The malware exploits a Microsoft Windows vulnerability in the Microsoft Server Message Block (SMB) v1.0 protocol. Once a user is infected, this strain of ransomware spreads laterally on the network by exploiting SMB file sharing protocol on TCP ports 139 and 445. The payload also has the capability to scan external IP ranges and further spread the infection.
Microsoft’s Response
Microsoft released a critical security patch, MS17-010, for this vulnerability in its March Security Bulletin and has been actively communicating customer guidance in blogs. Given the severity and virulent nature of this attack, Microsoft also released emergency patches for older, unsupported operating systems like Windows XP over the weekend.
Take Protective Action
- Apply Microsoft Windows security update MS17-010
- Block connection to ports 139 and 445 on your firewall
- Block legacy protocols like SMBv1 on local network
How Zscaler Can Help with Preventative Measures
Variants of WannaCry are already spreading, and delivery vectors are likely to change. The initial variants were configured with a killswitch domain (If the connection to this domain is successful then the malware will terminate.) We are already seeing newer payloads without any killswitch domain.
Zscaler added multiple signatures and indicators for blocking the original payloads as well as post-infection activity shortly after the attack to help any organizations affected by this campaign in their remediation efforts.
Advanced Threat Signatures:
Win32_Ransom_WannaCrypt0r
Win32_Ransomware_WannaCry
Win32.Ransom.WannaCry
In-line AV signatures:
W32/Trojan.XLPA-1871
W32/Trojan.VYDA-0103
W32/Ransom.ZTSA-8671
W32/Trojan.UXKN-7334
W32/Trojan.FSSE-8992
W32/Trojan.AHAZ-1193
W32/Trojan.TSYV-5087
W32/Trojan.FXSJ-2552
W32/Trojan.AHAZ-1193
Cloud Sandbox provides the best line of defense in a proactive manner against these evolving ransomware strains. Zscaler Cloud Sandbox successfully detected the payloads from this ransomware strain. Here is a sample Cloud Sandbox report from one such detonation:
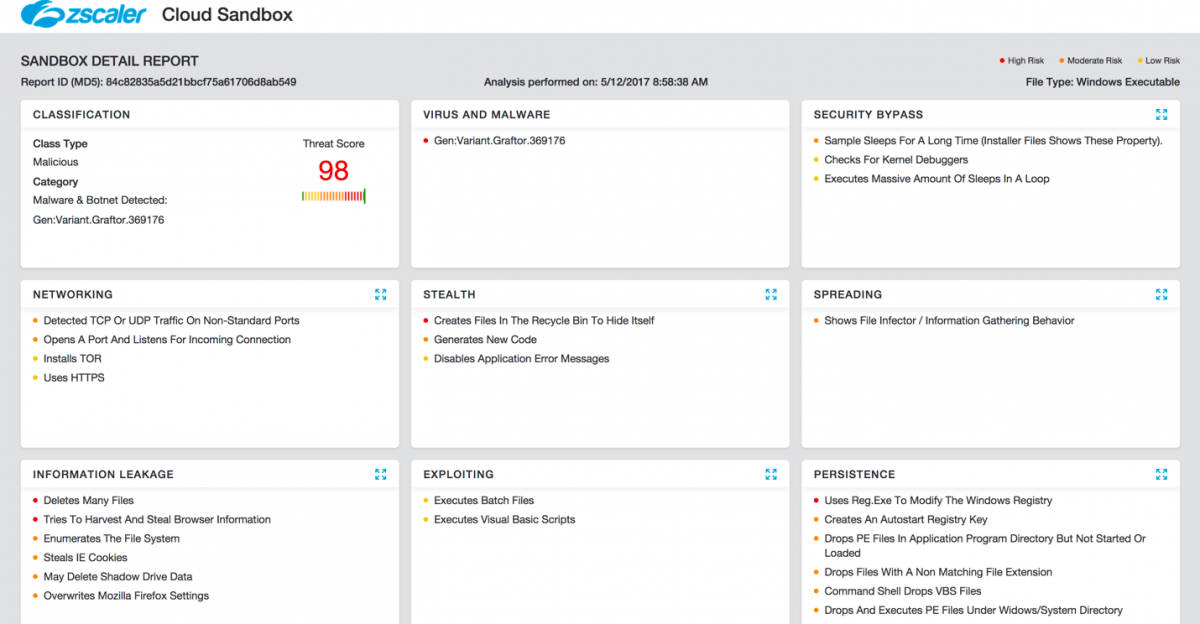
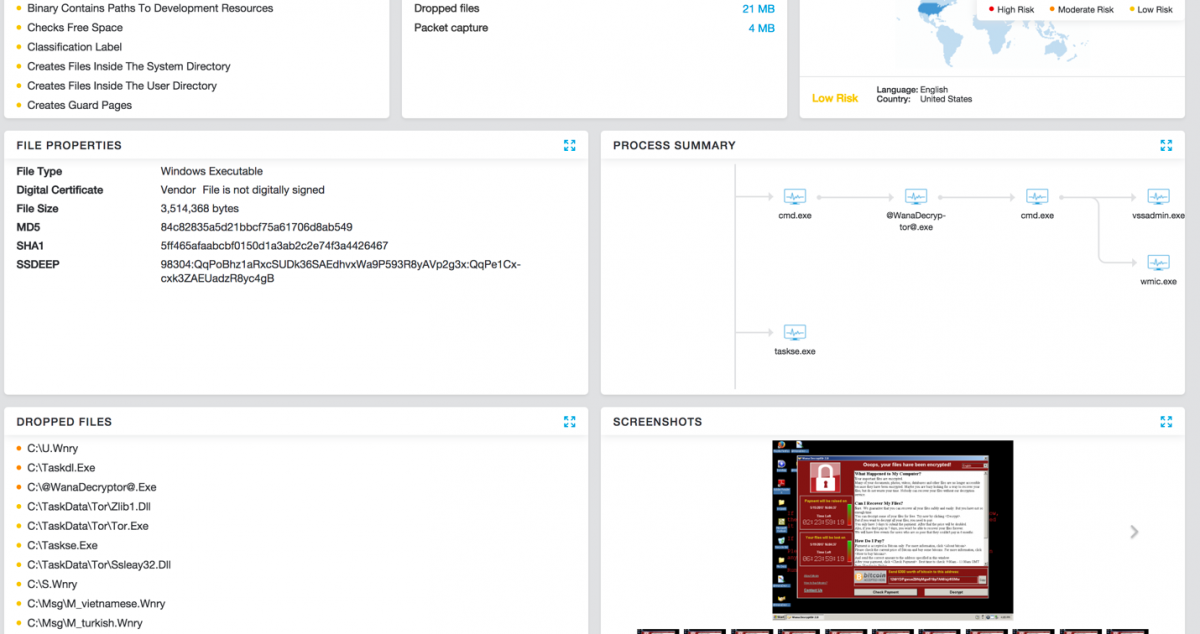
SSL inspection. Over 60% of Internet traffic is over SSL and most advanced threats hide in SSL. Zscaler Cloud Security Platform provides native SSL inspection.
Cloud Firewall. Enforcing policies to block outbound SMB traffic on ports 139 and 445 can be done in a single console and applied immediately across all locations with Zscaler’s Cloud Firewall.
Reference
https://www.us-cert.gov/ncas/alerts/TA17-132A
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
https://www.zscaler.com/blogs/research/wannacry-20-ransomware-attacks-continue





