 |
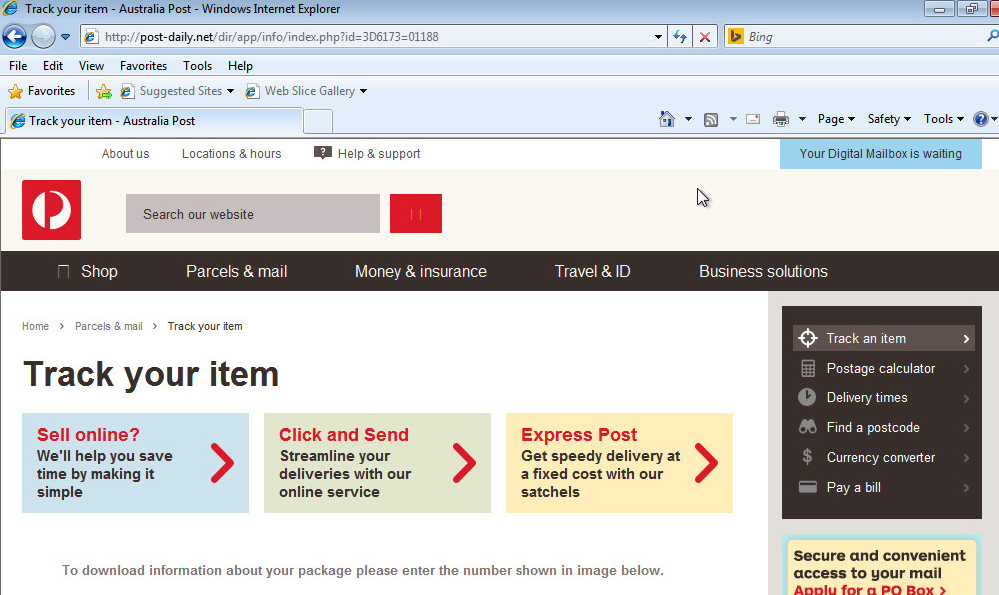
| This link is seen from a phishing e-mail. |
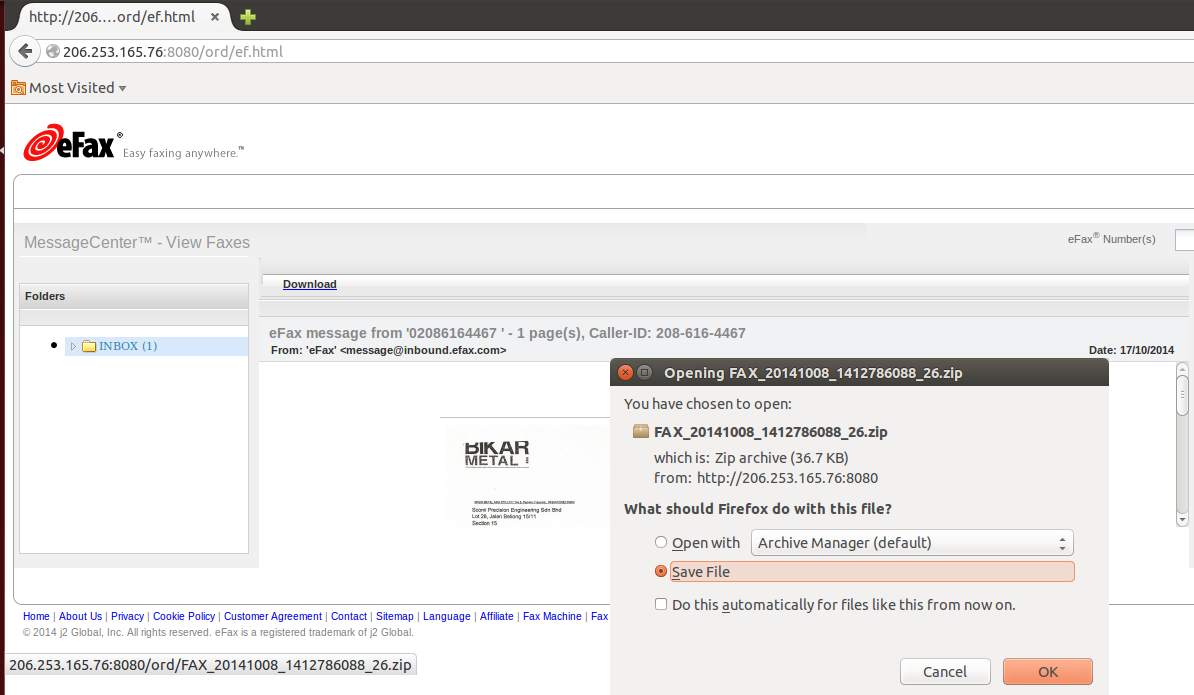
We recently encountered a ransomware campaign leveraging phishing e-mails purporting to be from the Australian Postal Services. The spam campaign themes used by the attackers involve tracking services or mobile invoices containing a link to the malicious content. Upon completion of a CAPTCHA, the user is provided a zip file which contains a malicious executable posing as a PDF document.
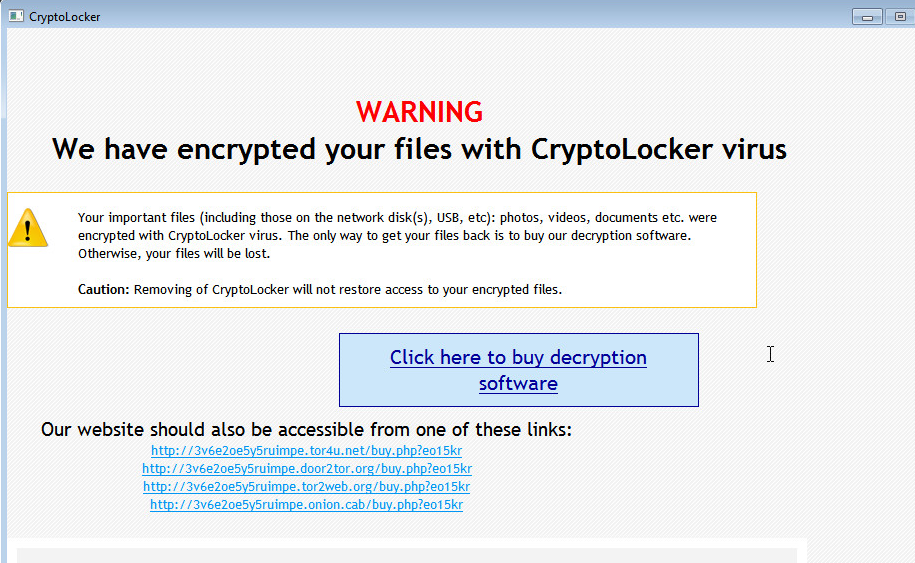
At the time of research, this particular file shows a a detection rate of 16/53 antivirus engines on Virustotal. Before the victim even has a chance to realize their mistake, they are greeted by a message informing them of just how impacted they are.
The goal of Cryptolocker or any other Crypto-Ransomware attack is to encrypt personal files and hold them hostage. The attacker encrypts the files using a specific key which is either obtained during the phone home request to a Command & Control (C2) server, or hard-coded within the malicious executable. In this case, the malicious executable itself is falsely presenting itself as a valid executable for AQQ IM.
 |
| AQQ is a popular IM application |
- C:\MSOCache\All Users\
- C:\Users\[Public/Username]\
 |
| The ".encrypted" files can only the key controlled by the attacker can release them. |
The threat will also drop a file in the Windows directory and an associated registry key to launch the file upon boot. This will ensure that the threat will remain persistent if the victim attempts to reboot their system.
 |
| The autostart value is randomly generated. |
Cryptolocker will phone home to a hard-coded malicious domain via SSL. The SSL certificate is signed using the printable string 'debian'. This transaction is the secure communication which will provide the specific key needed to encrypt the victim's files.
 |
| Viewing the C:\Windows\uhjrajyj.exe in this case will reveal the hardcoded domain used to phone home. |
 |
| The phone home address is hard-coded within the malicious payload. |
 |
| Decrypted call back attempt |
 |
| DGA activity |
These domains are largely returning 504 errors now as they have either not yet been registered or have already been shutdown. A few do were still live at the time of the research. Zscaler inspected the associated IP addresses and found them to be hosted in the Russian Federation. The two server IP addresses of note at the time of the blog are 46.161.30.20 and 46.161.30.19. Active ransomware URLs leading to these servers include:
- usygoseqowapadoh[.]com:443
- usygoseqowapadoh[.]com/topic.php
- octoberpics[.]ru:443
- octoberpics[.]ru/topic.php
Administrators should be on the lookout for the above connections as they likely indicate a compromised system. Given how prevalent this threat is, the U.S. Government recently released an associated alert on the US-CERT site.
Taking regular backups of your personal files remains a user's best chance at mitigating the threat if they have been hit by this attack. It is also important for system administrators to enforce strict file-type access control policies surrounding the download of archive and executable files from unknown sources.