Gehen Sie aktiv gegen komplexe Angriffe in Ihrem Netzwerk vor
Angreifer, die unentdeckt Zugriff auf Ihre Umgebung erhalten, bilden sich ein, sie hätten bereits gewonnen. Setzen Sie Deception-Technologie für eine proaktive Abwehr ein, die raffinierte Bedrohungsakteure durch realistische Täuschungsmanöver anlockt und entlarvt.
Schutz vor lateraler Ausbreitung
indem Angreifer mit überzeugenden Honeypots abgeschreckt werden
Abwehr von GenAI-Angriffen
auf Ihre Infrastruktur und Ihre Lerndatensätze
Kompromittierte User erkennen
und den Missbrauch gestohlener Zugangsdaten
Das Problem
Angreifer kompromittieren Zero-Trust-Umgebungen über User und Apps
90%ige
80 %
91 %
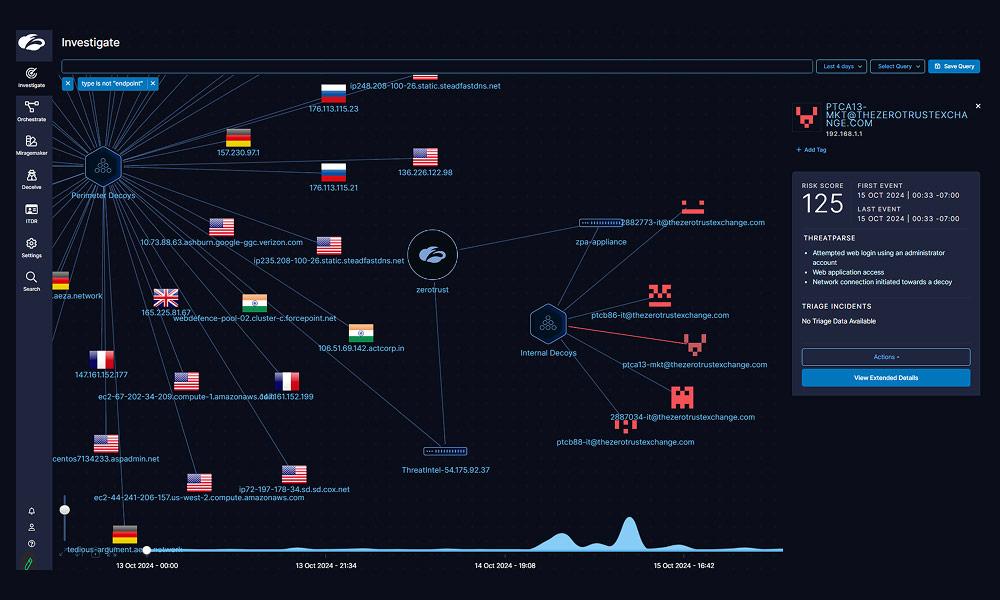
Produktübersicht
Erkennen Sie komplexe Bedrohungen, die herkömmliche Abwehrmaßnahmen umgehen
Zscaler Deception setzt in Ihrer Umgebung realistische Decoy-Assets ein, um aktive Angreifer anzulocken, zu erkennen und abzufangen. Wenn ein kompromittierter User mit einem Decoy interagiert, erhält Ihr Team sofort eine Warnmeldung – die Angreifer merken erst, dass sie ertappt wurden, wenn es zu spät ist.
Als Modul der Cloud-nativen Zscaler Zero Trust Exchange™ kann Deception hochpräzise Bedrohungserkennung schnell und nahtlos in der gesamten Unternehmensumgebung implementieren.
Reduzieren Sie Ihre Angriffsfläche
Lenken Sie böswillige Akteure von kritischen Zielen wie Endgeräten, Identitätssystemen, Netzwerken, Anwendungen und der Cloud ab.
Erkennen Sie wichtige Bedrohungen schneller
Erkennen Sie kompromittierte User, laterale Bewegungen und Ransomware mit hochzuverlässigen IOCs und geringer Fehlalarmquote.
Bedrohungseindämmung in Echtzeit
Mit Zero-Trust-Zugriffsrichtlinien können Sie den Zugriff auf vertrauliche SaaS-Services und interne Anwendungen dynamisch einschränken oder blockieren.
Vorteile
Gehen Sie die gezielte Bedrohungserkennung mit einem neuen Ansatz an
User und Anwendungen mit Decoys schützen
Erkennen Sie Bedrohungen und Angreiferaktivitäten mit Ködern auf Endgeräten sowie Decoys von Anwendungen, Servern, Usern und anderen Ressourcen.
Beschleunigen Sie die Reaktion auf Vorfälle und reduzieren Sie die Alarmmüdigkeit
Benachrichtigen Sie Ihr Sicherheitsteam schnell über bestätigte Bedrohungen und Sicherheitsverletzungen, ohne Fehlalarme oder zusätzlichen Betriebsaufwand.
Locken Sie Angreifer in die Falle
Ersetzen Sie Ihre Angriffsfläche durch überzeugende Scheinziele, denen Angreifer nicht widerstehen können, und fangen Sie sie in dem Moment, in dem sie den Köder schlucken.
Produktdetails
Eine umfassende Cyber-Deception-Plattform
Kernfunktionen
Mithilfe von Decoys von Chatbots, LLM-APIs und Agents sowie adaptiven Decoys können Angreifer erkannt werden, die die GenAI-Infrastruktur in Ihrer Umgebung ins Visier nehmen.
Nutzen Sie im Internet exponierte Decoys, um Bedrohungen bereits im Vorfeld eines Einbruchs zu erkennen, die speziell auf Ihr Unternehmen abzielen.
Legen Sie ein Minenfeld an, um Ihre Endgeräte mit Decoys von Dateien, Anmeldeinformationen, Prozessen und mehr zu schützen.
Erkennen Sie laterale Bewegungen in Ihren Cloud-Umgebungen mit Decoys von Web- und Dateiservern, Datenbanken und mehr.
Gewinnen Sie Erkenntnisse aus kontextreichen Protokollen und erhalten Sie mit zwei Klicks automatisierte Forensik- und Ursachenanalysen.
Setzen Sie Decoy-Serversysteme ein, auf denen Dienste wie SSH-Server, Datenbanken, Dateifreigaben und mehr gehostet werden.
Erkennen Sie Enumerationsaktivitäten und böswillige Zugriffe mit gefälschten Usern im Active Directory.
Erhalten Sie tiefere Einblicke in Angriffe in realistischen, hochgradig interaktiven Decoy-Betriebssystemumgebungen.
Anwendungsfälle
Machen Sie Ihr Netzwerk zu einer feindlichen Umgebung für Angreifer

Erhalten Sie Frühwarnsignale von Perimeter-Ködern, wenn Bedrohungsakteure wie Ransomware-Betreiber oder APT-Gruppen Aufklärungsarbeiten zur Vorbereitung von Angriffen durchführen.

Setzen Sie Decoy-Passwörter, -Cookies, -Sitzungen, -Lesezeichen und -Apps ein, um kompromittierte User zu erkennen, wenn ein Angreifer mit der Deception-Umgebung interagiert.

Verwenden Sie Decoys von Anwendungen und Köder auf Endgeräten, um Angreifer abzulenken und abzufangen, die versuchen, sich seitlich in Ihrer Umgebung zu bewegen.

Umgeben Sie Ihre wertvollen Assets mit Decoys, die selbst die raffiniertesten Gegner erkennen und sofort blockieren.

Erkennen Sie Ransomware in jeder Phase des Angriffslebenszyklus mit Decoys im Netzwerk, auf Endgeräten, in Cloud- und Active-Directory-Umgebungen.

Profitieren Sie von nahtloser Integration mit der Zscaler-Plattform und Sicherheitstools von Drittanbietern wie SIEM und SOAR, um aktive Angreifer mit automatisierter, schneller Reaktion auszuschalten.

Decoy-Webanwendungen, die anfälligen Testbed-Anwendungen und Services für den Remotezugriff wie VPNs ähneln, fangen Angreifer ab, die sich mit gestohlenen Zugangsdaten anmelden.

Zur Erkennung von Prompt Injection, Data Poisoning und anderen Angriffen mit hohem Schadenspotenzial, die auf Ihre GenAI-Infrastruktur und Lerndatensätze abzielen.

unsere Plattform
Zscaler Zero Trust Exchange
Sichere User-, Workload- und Gerätekommunikation zwischen und
innerhalb von Zweigstellen, Cloud-Umgebungen und Rechenzentrum.
Zero Trust Everywhere
Zuverlässiger Schutz vor Cyberangriffen
- Externe Angriffsfläche minimieren
- Schutz vor Kompromittierung
- Schutz vor lateralen Bewegungen
Schutz für Daten
- Datensicherheitsstatus ermitteln, klassifizieren und bewerten
- Datenverluste kanalübergreifend verhindern
Sichere KI-Nutzung
- Sicherheit bei der Nutzung öffentlicher KI-Tools
- Sicherheit bei der Nutzung privater KI-Anwendungen und -Modelle
- Sichere Agent-Kommunikationen
Betriebsabläufe automatisieren
- Sicherheitsabläufe beschleunigen
- Hervorragende digitale User Experience
FAQ
FAQ
Die Deception-Technologie von Zscaler geht über herkömmliche Honeypots hinaus, indem Decoys direkt in Endgeräte, Netzwerke, Active Directory, Cloud-Workloads, IoT/OT-Geräte usw. in User-Umgebungen eingebettet werden, sodass sie nicht von legitimen Assets zu unterscheiden sind. Statt statischer Honeypots setzt Zscaler Decoys und Breadcrumbs ein, damit Angreifer dazu verleitet werden, sich unwissentlich zu erkennen zu geben. Diese proaktive, verteilte Strategie zur Bedrohungserkennung in Echtzeit lässt sich nahtlos in die Zscaler Zero Trust Exchange integrieren.
Zscaler Deception ist nahtlos in die Zscaler Zero Trust Exchange integriert, um ressourcenschonende Decoy-Assets dynamisch über unternehmenseigene Endgeräte, Netzwerke, Active Directory, Cloud-Workloads und IoT/OT-Geräte zu verteilen. Die Decoys sind authentischen Assets zum Verwechseln ähnlich, sodass schädliche Aktivitäten praktisch sofort erkannt werden. Dieser eingebettete Ansatz ermöglicht eine proaktive Bedrohungserkennung und sorgt gleichzeitig für eine kontinuierliche Validierung für Zero Trust. Zscaler Deception ist außerdem in den Zscaler Client Connector und in Zscaler Private Access integriert, um laterale Bewegungen von Endgeräten zu Anwendungen zu erkennen.
Zscaler Deception ist darauf ausgelegt, ein breites Spektrum an Bedrohungen aufzudecken, darunter Advanced Persistent Threats (APTs), Pre-Breach-Angriffe, Identitätskompromittierung, Rechteausweitung, laterale Bewegungen, Insider-Bedrohungen und Ransomware. Indem Angreifer mit Decoys und Ködern angelockt werden, lassen sich verdächtige Verhaltensweisen bereits im Frühstadium erkennen. Dies gewährleistet einen proaktiven Schutz vor Sicherheitsverstößen und verkürzt die Verweildauer erheblich.
Ja, Zscaler Deception unterstützt Cloud-, On-Premise- und Hybridumgebungen vollständig. Das ressourcenschonende Design gewährleistet unabhängig von der Infrastruktur eine nahtlose Bereitstellung auf Endgeräten, Workloads und IoT-Geräten. Als Cloud-Lösung lässt es sich perfekt in zukunftsfähige verteilte Umgebungen integrieren und ermöglicht eine umfassende und skalierbare Bedrohungserkennung.
Ja, Zscaler Deception kann Angriffe wie Prompt Injection, Data Poisoning, Jailbreaking, Adversarial Suffixes, Trainingsdatenextraktion usw. erkennen. Zscaler Deception unterstützt die Erstellung von Decoy-LLM-Chatbots und -APIs zum Erkennen dieser Angriffe.








