Zuverlässiger Schutz für kritische Endgerätedaten
Um die Sicherheit der User zu gewährleisten und ein hohes Niveau bei der Data Protection und Datensicherheit aufrechtzuerhalten, benötigen Sie eine so robuste wie einfache Lösung zur Verhinderung von Datenverlusten (DLP) an Endgeräten. Sie profitieren von einem ressourcenschonenden, einheitlichen und browserunabhängigen Endgeräteschutz.
- Bereitstellung einer leistungsstarken zentralisierten DLP-Richtlinie
- Schnellere und effizientere Reaktion auf Sicherheitsvorfälle
- Konformität mit allen einschlägigen Vorschriften

Das Problem
Herkömmliche DLP-Verfahren für Endgeräte sind nicht mehr zeitgemäß
Legacy-Endpoint-DLP erhöht die IT-Komplexität erheblich, beeinträchtigt die User Experience und führt zu Lücken in den Richtlinien. In der heutigen cloudbasierten Welt gewährleistet dieser Ansatz keinen ausreichenden Schutz für vertrauliche Informationen.
Komplexe Richtlinien
Die Bereitstellung und Verwaltung ergänzender DLP-Richtlinien verursacht zusätzliche Betriebskosten.
Fragmentierte Warnungen
Herkömmliche DLP-Engines für Endgeräte sortieren Daten in verschiedene Schubladen ein, verursachen dabei aber oft Konflikte mit anderen Warnmeldungen innerhalb der Organisation
Komplexität durch Agents
Zusätzliche Agents auf Endgeräten beeinträchtigen die Anwendererfahrung.
Discover the difference: Zscaler DLP vs. Legacy DLP
Unlock your true potential by leaving traditional DLP solutions behind. See how Zscaler redefines data protection for the modern era.
Lösungsüberblick
Leistungsstarker Schutz mit einfacher Bereitstellung
Zscaler Endpoint DLP bietet einen ganzheitlichen, jederzeit verfügbaren Schutz sowie zahlreiche weitere Funktionen, die Sicherheitsbeauftragten im Kampf gegen Bedrohungen einen Vorteil verschaffen.
Schnelle Bereitstellung
Verwenden Sie Ihre vorhandenen DLP-Richtlinien, um Endgeräte schnell zu schützen und den Zugriff durch unbefugte User zu verhindern.
Wichtige Kanäle schützen
DLP-Richtlinien für wichtige Exfiltrationskanäle wie Wechselspeichermedien, freigegebene Netzwerke und Drucker
Synchronisierung von Cloudspeichern überwachen
Verhindern Sie den Datenabfluss in Cloudspeicher wie Dropbox, Box und OneDrive.
Leistungsstarke Dashboards und Workflows
Beschleunigen Sie die Reaktion auf Vorfälle mit detaillierten Dashboards, Forensik und integrierter Workflow-Automatisierung.
Vorteile
Für einheitlichen, durchgängigen Datenschutz auf den Endgeräten
Als Modul der umfassenden Datensicherheitslösung von Zscaler bietet Zscaler Endpoint DLP Ihnen die erforderliche Transparenz und Kontrolle über Gerätedaten und reduziert gleichzeitig die Kosten und Komplexität der Datensicherheit.
Unkomplizierte, leistungsstarke Richtlinien
Stellen Sie überall eine konsistente DLP-Richtlinie bereit – an Endpunkten, inline und in der Cloud – mit der Leistung unserer branchenführenden Cloud-nativen Plattform.
Alles mit einem einzelnen, ressourcenschonenden Agent
So sorgen Sie für lückenlosen Schutz inner- und außerhalb des Netzwerks, ungeachtet des Verbindungsstatus.
Absolute Transparenz
Profitieren Sie von einer zentralen Datenquelle und konsistenten Warnmeldungen für alle Endgeräte- und Cloud-Daten, die auf einer zentralen Klassifizierungs-Engine basieren.
Funktionen
Schützen Sie kritische Daten mit Defense-in-Depth
Vertrauliche Daten klassifizieren
Verstehen Sie, welche Art von Daten gespeichert werden, in welcher Region sie sich befinden, wer darauf Zugriff hat und welches Risiko damit verbunden ist.

Richtlinien überwachen und durchsetzen
Behalten Sie sämtliche Endgeräte-Aktivitäten über eine einzige Konsole im Auge und wenden Sie eine einheitliche Richtlinie an, um Daten bei der Übertragung und im Ruhezustand zu überwachen und zu schützen.
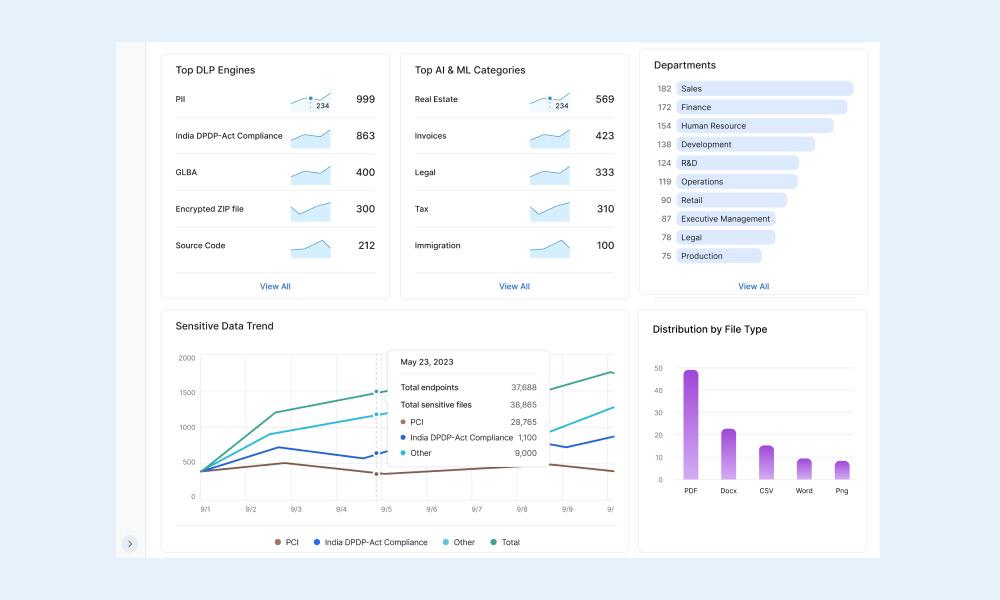
Automatische Fehlerbehebung
Entlasten Sie Ihr Sicherheitspersonal durch KI-gestützte Automatisierung zum Erkennen und Verhindern von Bedrohungen, Richtlinienverstößen und Datenverlusten.

Want to see Zscaler Data Security in Action?
Explore our interactive demo hub to see the powerful ways Zscaler can find and secure all types of data risks
Anwendungsfälle
Optimieren und stärken Sie die Datensicherheit auf Endgeräten

Get rid of complicated point products and deliver data security from one unified strategy.

Track and consistently protect your most sensitive data in real time, no matter where or how it is accessed.

Secure the employee attrition process by stopping exfiltration of sensitive data to personal and removable storage.

Ensure regulatory compliance is maintained for required data and file types across your entire organization.

unsere Plattform
Zscaler Zero Trust Exchange
Sichere User-, Workload- und Gerätekommunikation zwischen und
innerhalb von Zweigstellen, Cloud-Umgebungen und Rechenzentrum.
Zero Trust Everywhere
Zuverlässiger Schutz vor Cyberangriffen
- Externe Angriffsfläche minimieren
- Schutz vor Kompromittierung
- Schutz vor lateralen Bewegungen
Schutz für Daten
- Datensicherheitsstatus ermitteln, klassifizieren und bewerten
- Datenverluste kanalübergreifend verhindern
Sichere KI-Nutzung
- Sicherheit bei der Nutzung öffentlicher KI-Tools
- Sicherheit bei der Nutzung privater KI-Anwendungen und -Modelle
- Sichere Agent-Kommunikationen
Betriebsabläufe automatisieren
- Sicherheitsabläufe beschleunigen
- Hervorragende digitale User Experience
FAQ
Endpoint-DLP-Lösungen überwachen und schützen kontinuierlich vertrauliche Daten auf Endgeräten (z. B. Laptops, Desktops, IoT, Mobilgeräte), um unbefugte Freigaben oder Exfiltrationen zu verhindern. Durch die Ausweitung der herkömmlichen DLP Funktionen auf einzelne Geräte können Unternehmen vertrauliche Dateien effektiver schützen. Endpoint DLP kann auch riskante Useraktivitäten wie das Übertragen, Hochladen oder Drucken vertraulicher Daten erkennen und blockieren.
Ja, heutige Endpoint-DLP-Lösungen verwenden Datenklassifizierungstechniken zum Erkennen vertraulicher Informationen wie Kreditkartennummern, personenbezogene Daten oder geistiges Eigentum. Zu den erweiterten Funktionen gehören Exact Data Match (EDM) und trainierbare Klassifikatoren zur Erkennung spezifischer Datentypen und Muster, die für das jeweilige Unternehmen relevant sind.
Um zu bewerten, ob Ihre Endpoint-DLP-Lösung alle verbundenen Geräte schützt, können Sie durch eine zentrale Überwachung überprüfen, ob alle Endgeräte, einschließlich Laptops, Desktops, Mobilgeräte und IoT-Assets erfasst werden. Überprüfen Sie die nahtlose Integration mit Netzwerk-Systemen und testen Sie die Erkennungsfunktionen für vertrauliche Dateien und riskantes Userverhalten. Führen Sie regelmäßige Compliance-Audits durch und pflegen Sie aktuelle Endgerät-Inventare, um lückenlosen Schutz zu gewährleisten.