Overview
Secure web and non-web traffic for all users, apps, and locations
To protect users, apps, and data everywhere, you need security that can adapt to the dynamic needs and unique risks of distributed environments. Modernize your security with a zero trust cloud firewall that enables you to:
Stop threats and inspect 100% of traffic
even encrypted traffic
Centralize policy management
for all users and traffic
Seamlessly connect to SaaS apps
like Microsoft 365 and Zoom
Cut costs and complexity
without compromising performance
The Problem
Traditional firewalls weren't built to secure modern traffic
70%
95%
85.9%
Traditional firewalls can’t deliver zero trust
Traditional network-based firewalls use an IP-centric, zone-based architecture that increases the attack surface and lets threats move laterally. They can’t adapt to enforce dynamic policies based on user context, risk, and device posture. Next-generation firewalls (NGFWs), on-premises or in the cloud, struggle to inspect 100% of traffic without slowing performance, forcing network admins to choose between performance and security.
In short, traditional and next-generation firewalls can't provide zero trust to protect work-from-anywhere users, cloud apps, and locations.
Solution Overview
Move beyond legacy architecture with a zero trust firewall
Built on a cloud native platform, a zero trust firewall protects web and non-web traffic for all users, apps, locations, and clouds.
Unlimited scale and cloud native TLS/SSL decryption capabilities ensure 100% inspection of all traffic, with zero performance degradation. Protect users, devices, and apps anywhere from cyberthreats, protect data, and ensure regulatory compliance.
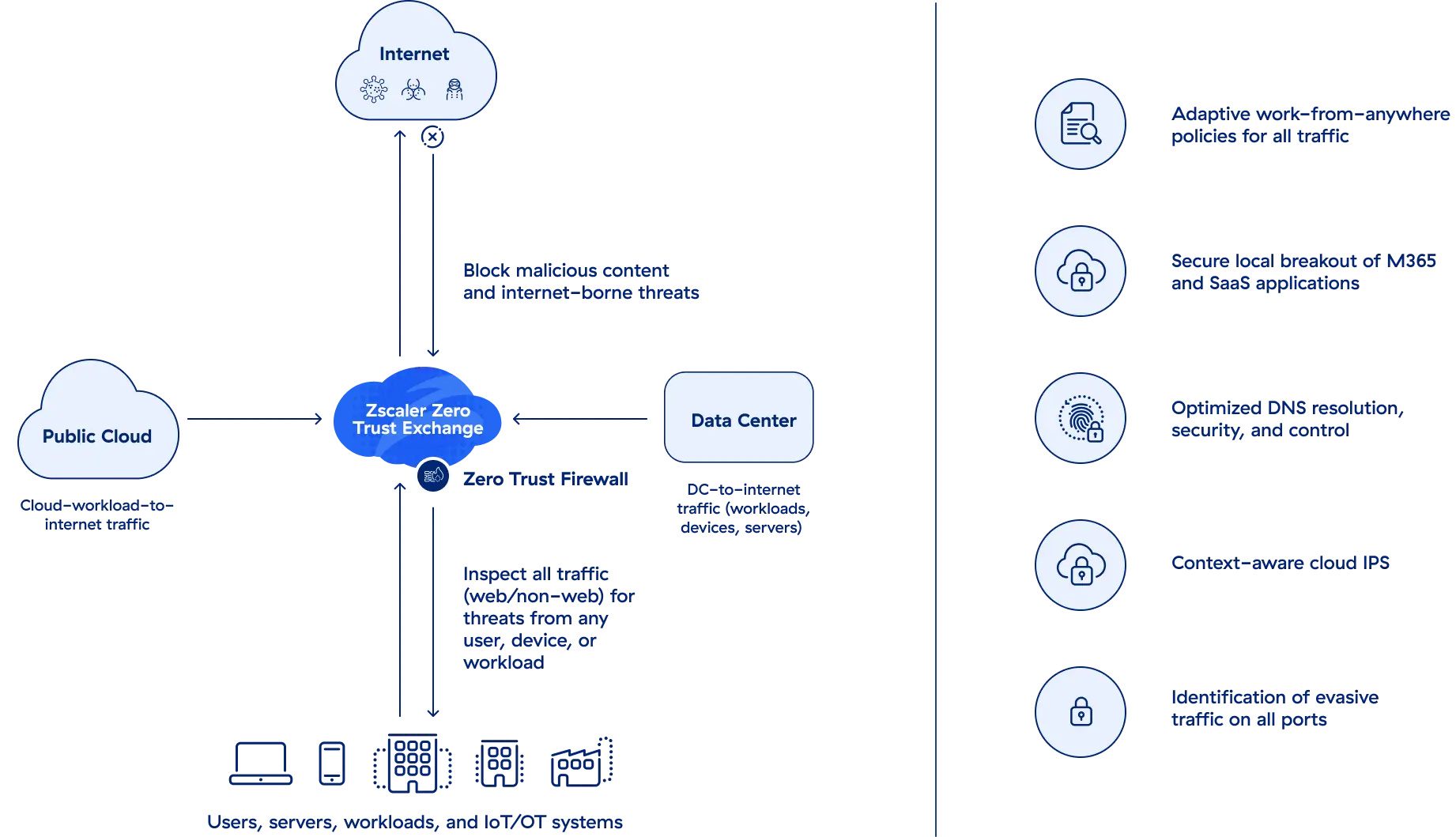
Benefits
Get infinite scale and unbeatable performance in a cloud-based firewall
Stay safe from threats
Uncover stealthy attacks with complete and unlimited inspection of traffic—including TLS/SSL—and proactively block malicious domains for all users while detecting and preventing DNS tunneling.
Centralize policy management for all users, locations, and clouds
Universally configure, manage, and enforce user- and app-aware threat protection and risk-based policies from a single console.
Securely connect to your favorite SaaS applications
Provide users with cloud-delivered, bandwidth-prioritized local internet breakouts to Microsoft 365, Zoom, and other business applications.
Dramatically reduce cost and complexity
Replace costly and inefficient security appliances with a cloud native zero trust platform that elastically scales to handle high volumes of long-lived connections without compromising performance.
Solution Details
What sets Zscaler Zero Trust Firewall apart?
Traffic inspection
Terminate malicious connections and prevent threats with unlimited inline traffic inspection and native TLS/SSL decryption.
Bandwidth control
Prioritize business-critical apps, provide a better user experience, reduce costs, and simplify IT with cloud-delivered bandwidth control.
Secure work-from-anywhere users
Leverage unparalleled user- and app-aware threat protection with dynamic, follow-me policies on and off the corporate network.
Wildcard domains
Create flexible access policy to cloud services and PaaS/IaaS with centralized policy management.
Advanced attack detection
Quickly identify and intercept evasive and encrypted cyberthreats hiding in traffic on nonstandard ports.
Secure internet breakouts
Improve user experiences with scalable, fast, secure direct-to-internet connections for all hybrid and branch traffic.
Always-on cloud IPS and custom signatures
Enrich SecOps workflows with adaptive behavioral IPS signatures, including custom signatures, that work in real time and are easily shared.
DNS performance and security
Sustain superior performance and keep your users and endpoints safe from malicious sites with localized resolutions and DNS tunneling.
Use cases
A complete platform to serve your whole organization

Bring security as close to the user as possible, delivering user- and app-aware threat protection and risk-based policies with the cloud effect for consistent, identical protection from anywhere and on any device.

Apply adaptive, risk-based policies from a centralized console that can terminate malicious connections.

Protect cloud infrastructure and resources, detect anomalies, and dynamically assess risk computation for user, device, and location.

Drive better user experience and cloud app performance while implementing DNS security and control policies. Achieve faster resolution by pairing geographically local apps.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications

Securing cloud transformation with zero trust
“The visibility and control offered by Zscaler allows us to make smart policy decisions that improve our users’ experiences while allowing us to ensure we are appropriately managing our risk environment.”
—Ken Athanasiou, CIO, AutoNation
FAQ
FAQs
Zero trust is a security strategy in which entities are granted access based on context and security posture—not assumed trust. A well-tuned zero trust architecture leads to simpler network infrastructure, a better user experience, and stronger cyberthreat defense. Learn more.
NGFWs provide inline application control, IPS, threat prevention, advanced anti-malware, and more. They also enforce stricter access controls on network traffic than traditional firewalls. However, they weren’t designed to support cloud apps and infrastructure. Learn more.
NGFWs go beyond traditional firewalls, adding inline application control, intrusion prevention system (IPS), threat prevention, and advanced malware protection, and more. However, they weren’t designed to support cloud apps and infrastructure. Learn more.
SSE is a convergence of network security services delivered from a purpose-built cloud platform. SSE core services include secure web gateway (SWG), zero trust network access (ZTNA), cloud access security broker (CASB), and firewall as a service (FWaaS). Learn more.



