Protect your organization from the new generation of threats
To secure your organization from constantly evolving and advancing cyberattacks, you need a platform that delivers comprehensive zero trust cyberthreat protection at the speed and scale of the cloud.
Stop threats before they become attacks
Eliminate point products and complexity
Prevent lateral threat movement
See and prioritize your biggest risks
The problem
VPN- and firewall-centric approaches can no longer protect against cyberattacks
86%
56%
400%
A cyberattack is like a bank robbery
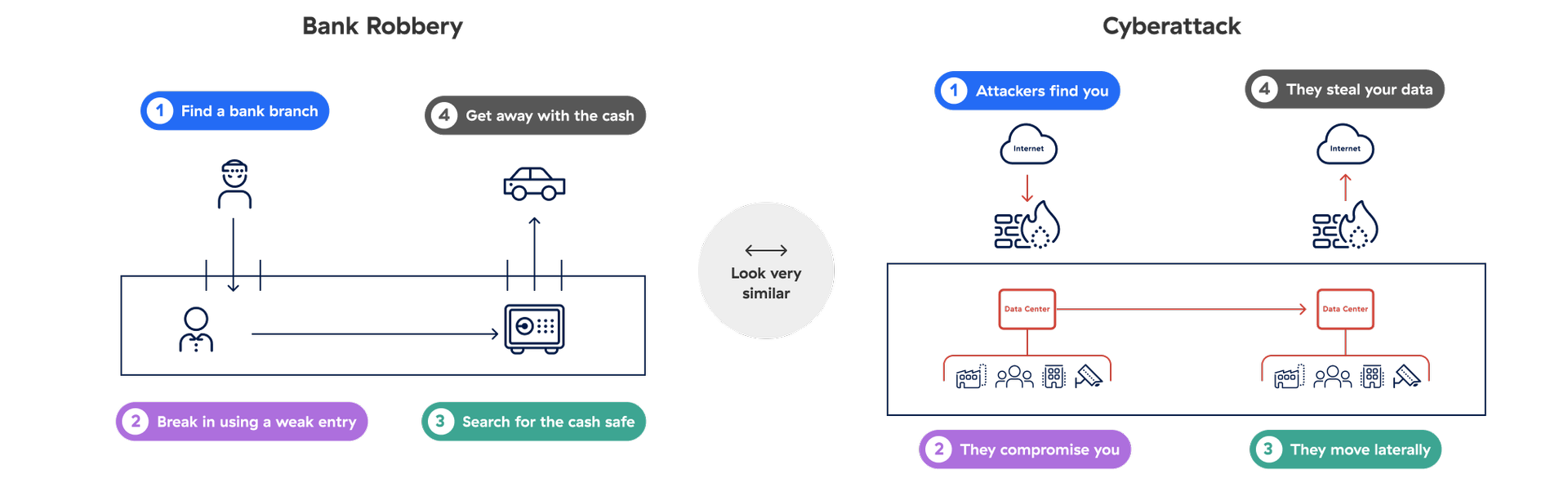
Attackers find you
Discoverable IPs are vulnerable—even firewalls and VPNs, which are meant to protect you in the first place.
They compromise you
Attackers exploit vulnerabilities to establish a beachhead in your network.
They move laterally
Once a machine is infected, the entire network is compromised.
They steal your data
Sensitive data across applications, servers, and entire networks is lost.
Solution Overview
Holistic, future-ready threat defense
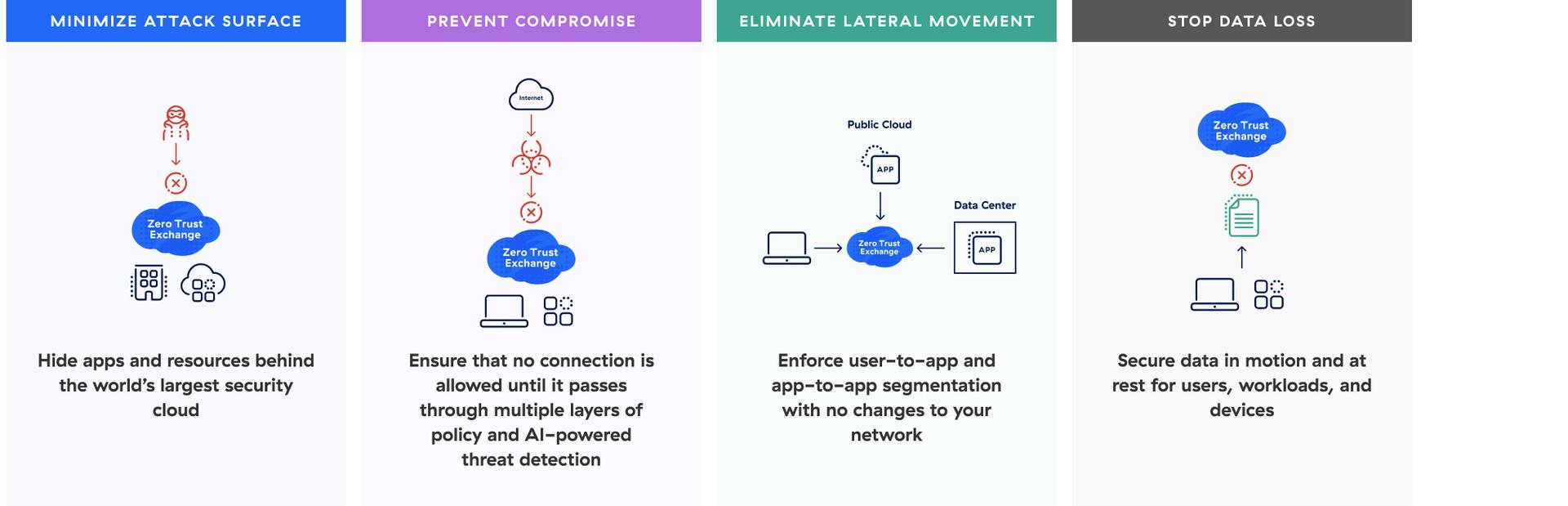
The cloud native Zscaler Zero Trust Exchange™ platform combats every step in the attack chain. This holistic approach maps to the MITRE ATT&CK framework to minimize attack surface, prevent compromise, eliminate lateral movement, and stop data loss.
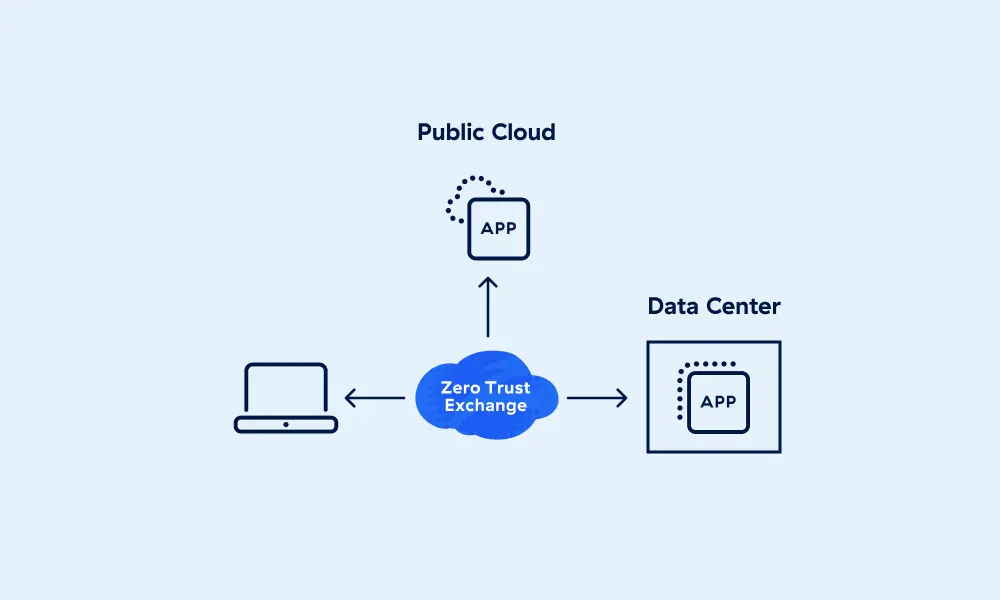
Built on the principle of least privilege, our proxy architecture enables full TLS/SSL inspection at scale, with connections brokered between users and applications based on identity, context, and business policies.
Benefits
What sets Zscaler Cyberthreat Protection apart?
Secure all four stages of a cyberattack
Minimize the attack surface, prevent compromise, eliminate lateral movement, and stop data loss.
Protect users from cyberthreats inline
Block threats before they enter your systems with AI-powered threat protection.
Reduce complexity with a cloud-based architecture
Retire legacy hardware and point products, simplifying management and saving costs.
Understand the biggest risks to your organization
Gain actionable risk insights and guided workflows for remediation.
Solution Details
Minimize the attack surface
Threat actors can’t attack what they can’t see. By hiding your apps, locations, and devices from the internet, Zscaler prevents threat actors from reaching and breaching these assets.

Key offerings
Get a holistic view of what’s exposed to the internet, vulnerabilities, and TLS/SSL weaknesses.
Prevent unauthorized access to critical systems (SSH/RDP/VNC).
Keep users, branches, and factories hidden behind the Zero Trust Exchange.
Prevent compromise
Snuff out phishing attacks, malware downloads, and more with full inline TLS inspection at scale and AI-powered threat prevention informed by more than 400 billion daily enterprise transactions.

Key offerings
Transform risky web content into a safe, dynamic stream of pixels.
Leverage content scanning, correlation, and risk scoring.
Eliminate lateral movement
Zero trust segmentation requires no network segmentation—your network is simply transport. Minimize the blast radius, defend against insider threats, and reduce operational overhead.
Key offerings
Leverage OWASP Top 10, CVE, and custom protections for application traffic.
Stop data loss
Discover shadow IT and risky apps with automatic classification of sensitive data. Secure user, workload, and IoT/OT traffic for data at rest and data in motion with inline email, endpoint DLP, and TLS inspection at scale.

Key offerings
Close dangerous misconfigurations in SaaS platforms like Microsoft 365 and Google Workspace.
Secure public cloud data with in-depth data discovery and posture management.
Take a self-guided tour
Stop advanced cyberattacks like ransomware, supply chain attacks, phishing, & more with proprietary advanced threat protection.
Featured Alliances




our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
FAQ
FAQs
Cyberthreat protection is a category of security solutions designed to help security professionals defend systems and networks against malware and other targeted cyberattacks. Such attacks attempt to infiltrate systems or networks to disrupt services or steal data, often to turn a profit for the attackers. Read the article
Zero trust is a security strategy that asserts that no entity—user, app, service, or device—should be trusted by default. Following the principle of least-privileged access, before any connection is allowed, trust is established based on the entity’s context and security posture, and then continually reassessed for every new connection, even if the entity was authenticated before. Read the article
Ransomware attacks are a type of malware attack in which threat actors may encrypt files, exfiltrate (steal) data and threaten to publish it, or both, to coerce the victim into making a ransom payment, usually in cryptocurrency. Attackers generally promise to provide decryption keys and/or delete stolen data once paid. Ransomware has become a highly popular means of extortion by cybercriminals as remote and hybrid work models have exposed endpoints to new vulnerabilities. Read the article
Threat intelligence is the collection, analysis, and dissemination of information about suspected, emerging, and active cyberthreats, including vulnerabilities, threat actors’ tactics, techniques, and procedures (TTPs), and indicators of compromise (IOCs). Security teams use it to identify and mitigate risk, reinforce security controls, and inform proactive incident response. Read the article



