/ What Is Cloud Security?
What Is Cloud Security?

Why Is Cloud Security Important?
As workforces, data, and cloud applications have become more distributed, legacy networking models—built around local workers and resources—have made them slower and less secure. To make up for losses in security, productivity, and user satisfaction, organizations need to reconsider how they are protecting their environments.
Today, in a complex economy driven by innovation—and shadowed by the growing business of cybercrime—organizations need the flexibility and scalability of cloud services, which can only be effectively secured by cloud security solutions that rise to meet the unique needs of the cloud.
How Does Cloud Security Work?
A cloud environment is only as secure as its weakest point, so effective cloud security means multiple technologies working together to protect data and applications from all angles. This often includes firewalls, identity and access management (IAM), segmentation, and encryption.
Rather than protecting a perimeter, cloud security protects resources and data individually. This means implementing more granular security measures, such as cloud security posture management (CSPM), data protection, data security, disaster recovery, and compliance tools.
Cloud environments, especially hybrid clouds that combine public clouds with private data centers, can have many internal and external vulnerabilities. That’s why it’s critical to leverage access controls, multifactor authentication, data protection, encryption, configuration management, and more to keep them accessible and secure.
98.6% of organizations have misconfigurations in their cloud environments that cause critical risks to data and infrastructure.
What Is Cloud Computing?
Cloud computing—the cloud—now dominates worldwide as a means of accessing resources over the internet. It allows organizations to entrust some of their data, apps, and infrastructure to third-party cloud providers that may store, manage, or secure those resources.
Cloud Service Types
SaaS offerings, storage, and various platform and infrastructure services are available from public cloud service providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud.
There are four subtypes of cloud infrastructure deployment:
- Private cloud: Dedicated infrastructure used by one organization and owned by a third party or the organization itself, which is responsible for its security management. Common users include governments, financial firms, and others with especially sensitive data to secure.
- Public cloud: Infrastructure owned by a third party and shared among multiple organizations, which also share security responsibilities with the provider per a shared responsibility model. Public cloud services such as Google Workspace and Microsoft 365 are widely used globally.
- Hybrid cloud: A combination of private and public deployment where an organization uses each for its strengths, such as scalability (public cloud) or stricter controls (private cloud). Common users include DevOps teams or others in need of flexible, configurable systems.
- Multicloud: Shared infrastructure, generally used by organizations that need access to the same applications and/or have the same segmentation and privacy requirements (e.g., PCI DSS). Enterprises worldwide use multicloud environments to access various vendors’ services.
As well as four main cloud service models:
- Software as a service (SaaS): Complete software solutions delivered from the cloud, which can be free or paid (e.g., Google Docs)
- Platform as a service (PaaS): Cloud-delivered tools developers can use to build, test, and deploy applications in a scalable environment
- Infrastructure as a service (IaaS): Virtualized infrastructure, managed by a third party, onto which an organization can install software
- Functions as a service (FaaS): Similar to PaaS, but suited to individual functions of apps, which can be spun up or down very quickly
Cloud Security: The Shared Responsibility Model
A shared responsibility model is a cloud security and risk framework that delineates which cybersecurity processes and responsibilities lie with a cloud service provider (CSP) and which lie with the customer. With more IT architectures moving to the cloud, a shared responsibility model promotes tighter security and establishes accountability as it relates to the security of the cloud.
Learn more in our dedicated article: What Is a Shared Responsibility Model?
55.1% of organizations use more than one cloud provider, and 66.7% have public cloud storage buckets.
Pros and Cons of Cloud Security
When you move your resources off your network, perimeter-style defenses don’t work anymore, forcing you to re-evaluate how to most effectively support user productivity, identify security issues, mitigate vulnerabilities, block malware, and prevent data loss.
This is where cloud security comes in, bringing a whole slate of benefits, but not without some potential risks. Let’s look briefly at some of the most notable points.
Pros
- Scalability to meet security needs as an organization grows and evolves
- Increase visibility and security for cloud resources and unique endpoint devices
- Cost savings through reduced on-premises infrastructure and associated upkeep costs
- Centralized management to simplify monitoring, control, and enforcement of security policies
- Redundancy through multiple points of presence to support disaster recovery efforts
- Automatic updates to ensure rapid protection against the latest vulnerabilities
Cons
- Risk of misconfigurations that leave data vulnerable to unauthorized access and hackers
- Compliance concerns with regard to government or industry data handling regulations
- Latency and data privacy/sovereignty issues if the provider lacks global points of presence
At a glance, these cons might seem alarming—but with due diligence and the right partner, you can eliminate them.
Cloud Security vs. Traditional Network Security
Network security stacks were designed to protect enterprise networks, not the cloud. They can’t provide the comprehensive cybersecurity today’s SaaS apps, high-bandwidth services, and mobile users need. To do that without added costs or complexity, you need a multitenant security platform that scales elastically. You’ll never get that with a traditional network security architecture.
The best way to secure apps, workloads, cloud data, and users—no matter where they are—is to move security and access controls to the cloud.
Benefits of Cloud Security
A comprehensive cloud security platform provides:
- Built-in security services and cloud access controls that give you visibility into all traffic traversing your distributed cloud and on-premises infrastructure
- Insight into every request—by user, location, server, and endpoint device around the world—in seconds through one interface
- API integrations with SD-WAN, cloud access security broker (CASB), IAM, and endpoint protection services to further strengthen your security posture
Common Cloud Security Challenges
Although it can greatly ease security management and increase visibility, cloud security comes with its share of challenges, underscoring how important it is to find the right partner.
1. Identity and Access Control
Cloud providers continue to add more services, and the average number of distinct entitlements for these services now exceeds 5,000. This volume of entitlements can be challenging to manage using traditional identity and access management (IAM) approaches.
2. Logging, Monitoring, and Incident Response
Comprehensive and accurate logs are a cornerstone of effective incident response. Many organizations’ existing solutions are ill-equipped for the volume of data cloud computing tends to produce, and are unable to reliably collect complete logs.
3. Storage and Encryption
Queueing and notification services often hold sensitive information before it’s processed and proper security measures are applied. The sensitivity of this is frequently overlooked—many services lack server-side encryption.
4. Cloud Ransomware
Cloud environments are still vulnerable to cyberattacks. Attackers most commonly infiltrate environments by taking advantage of misconfigurations or poor security practices, such as over-permissioned access, insufficient policy controls, or weak passwords.
5. Supply Chain Attacks in the Cloud
Sharing data and access with third parties, such as suppliers and contractors, opens cloud environments to greater risk of supply chain attacks, making the monitoring and management of third-party access a key priority for security teams.
68% of organizations have external users (from outside the organization, via role delegation or guest users) with admin permissions to the cloud environment.
Why the Cloud Offers Better Protection Than Appliances
Protecting users with consistent and enforceable policies requires more than URL or web filtering. That’s why thousands of organizations have already moved their IT security from appliances to secure cloud services. Let’s glance at some of the key differences.
Enterprise-Wide Protection
Appliance-based security requires security stacks at all egress points or backhauling traffic over costly MPLS links from branch offices and remote sites. Mobile users go unprotected.
Cloud-based security extends users the same protection whether they’re in the HQ, branch offices, on the road, or at home.
Integrated Security
With appliance-based security, appliances from different vendors often work in isolation, with no simple way to aggregate their data to understand security issues.
With cloud-based security, integrated security controls and cloud services correlate information to give you a complete picture of your entire network.
User Experience
With appliance-based security, every appliance between your users and the internet causes latency. If users have to VPN into the data center, their experience is even worse.
Cloud-based security with Zscaler provides fast local breakouts, and our Single-Scan Multi-Action technology enables our security services to scan simultaneously for faster performance.
IT Complexity
With appliance-based security, maintaining appliances from multiple vendors is expensive and difficult, requiring continuous patching and upgrades.
Cloud-based security consolidates point products into an integrated platform; there's no hardware or software to buy or manage.
Intelligence
With appliance-based security, point products generally apply a single technique to identify threats and pass the data on to the next appliance, applying patches when available.
Cloud-based security from Zscaler integrates intelligence from countless sources, so when a threat is detected anywhere in the cloud, protection is deployed everywhere.
Value
Appliance-based security is expensive to purchase, and as threats increase, you're forced to buy more appliances as well as replace old ones.
Zscaler cloud-based security moves security from capex to opex for about the price of a cup of coffee per user per month.
4 Pillars of Cloud Security
Cloud security aims to protect more than just the perimeter, bringing security all the way down to the data. Some of the most common measures include:
- Identity and access management (IAM) to help provision access to resources in cloud environments. IAM also helps you prevent unauthorized access to data, apps, and infrastructure shared across clouds.
- Data loss prevention (DLP) to monitor and inspect data to prevent exfiltration. DLP is an essential element of cloud computing security that a traditional security model can’t carry out effectively.
- Data encryption to encode data so that attackers can’t interpret it without decrypting it. Encryption also helps establish trust and preserve anonymity, and is required by various privacy regulations worldwide.
- Security information and event management (SIEM) to analyze security logs in real time, giving your security team increased visibility over your cloud ecosystem.
These are core security technologies, but with today’s savvy threat actors and growing compliance requirements, cloud security has had to evolve to keep up.
How Is Cloud Security Evolving?
The global technology landscape is evolving, and so is cloud security. More recently, two of the most important concepts are security service edge (SSE) and zero trust.
SSE solves fundamental challenges related to remote work, the cloud, secure edge computing, and digital transformation, providing secure access to the internet, SaaS and cloud apps, and your organization’s private apps.
Zero trust, a key component of SSE, is also also seeing rapid adoption. Based on the idea that no user or entity should be inherently trusted, a zero trust approach grants access to data and apps based on specific context—identity, content, location, device, and more—while delivering enhanced user experiences.
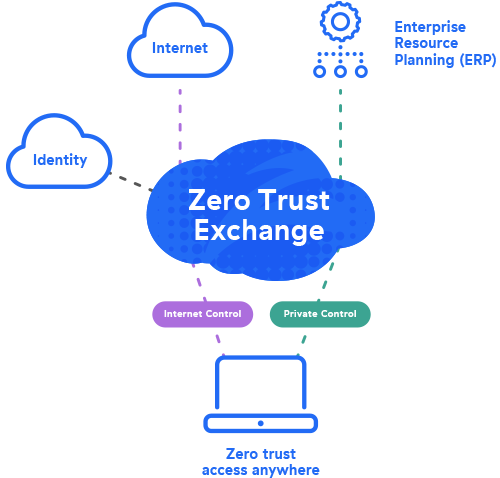
Why Should You Embrace Zero Trust?
The benefits of the cloud increasingly outstrip on-premises technology. Securing cloud environments means investing in technologies that will prevent data breaches while helping users stay satisfied and productive, and today, zero trust is the only security paradigm that can offer that.
According to Cybersecurity Insiders, 72% of organizations are prioritizing zero trust adoption. They understand that archaic, siloed security tools simply don’t have the capacity or scalability to protect all your cloud resources, wherever they’re being accessed from.
As you evaluate zero trust offerings, remember that any vendor can say they offer zero trust. Many vendors bolt a cloud platform onto a legacy network appliance and call it “cloud ready.” You need a partner with a zero trust solution that’s cloud native: built in the cloud, for the cloud.
How Zscaler Can Help
Zscaler secures your cloud environment with a cloud native zero trust architecture through Zscaler Private Access™ (ZPA™), part of the Zscaler Zero Trust Exchange™ platform. As the world’s most deployed ZTNA platform, ZPA applies the principle of least privilege to give users secure, direct connectivity to private apps while eliminating unauthorized access and lateral movement.
ZPA offers you:
- Peerless security, beyond legacy VPNs and firewalls: Users connect directly to apps—not the network—minimizing the attack surface and eliminating lateral movement.
- The end of private app compromise: App protection with inline prevention, deception, and threat isolation minimizes the risk of compromised users.
- Superior productivity for today's hybrid workforce: Lightning-fast access to private apps extends seamlessly across remote users, HQ, branches, and third parties.
- Unified ZTNA platform for users, workloads & OT/IoT: Securely connect to private apps, services, and OT/IoT devices.
Zscaler for Workloads provides comprehensive protection for workloads in multicloud environments, including on-premises data centers. Zscaler Posture Control secures your cloud native apps through build, deploy, and runtime with:
- Cloud security posture management (CSPM): Identify and remediate misconfigurations and vulnerabilities across all major public cloud providers.
- Cloud infrastructure entitlement management (CIEM): Manage cloud risk by identifying and minimizing excessive privileges in public cloud services.
- Cloud data loss prevention (DLP): Protect sensitive data and improve risk triage with greater understanding of impact for public cloud risks.
Additionally, Zscaler Workload Communications (ZWC) protects all your cloud workload traffic—north-south and east-west—to prevent the spread of malware across your cloud infrastructure. A unified solution that provides orchestration across all major cloud providers, it offers both consistent security and simpler operations.
Uncover critical risks across your entire public cloud environment with a free Cloud Security Risk Assessment.
Get a complete picture of your public cloud risks, compliance posture, and cloud asset inventory, with actionable remediation guidance.
Suggested Resources
Frequently Asked Questions
The top cloud security risks include data breaches and unauthorized access, misconfigurations that leave data exposed, inadequate IAM controls, compliance and regulatory challenges, and potential service outages or disruptions. Other risks include shared infrastructure vulnerabilities, insider threats, and dependencies on third-party cloud service providers for security measures.
Cloud security is a subcategory of cybersecurity that focuses specifically on protecting data and applications stored in remote servers, rather than an organization's private, on-site servers. It involves measures to secure virtual spaces, control access, and prevent breaches in cloud environments. General cybersecurity measures are built to protect any or all other digital workloads, in the cloud or not, against online threats such as viruses, hacking, and identity theft.
Cloud security involves protecting digital assets stored in the cloud. A company might use strict access controls (functionally similar to requiring ID cards) to ensure need-to-know access to sensitive information. The same company might also encrypt its data so that only those with the correct key can read it. Combined with other measures and regular security audits, an organization can create a secure, controlled environment for its cloud data.
While the process varies greatly from one organization to another, most begin securing cloud data by identifying and classifying their data to determine its needs. They should then implement strong access controls, authentication, and encryption to protect data in transit and at rest. Regular vulnerability audits and testing can pinpoint weak points, and comprehensive monitoring and logging solutions will help find and address anomalous behavior.