/ What Is a Cloud Access Security Broker (CASB)?
What Is a Cloud Access Security Broker (CASB)?
A cloud access security broker (CASB) is an enforcement point that sits between cloud application users and cloud services to provide data protection and threat protection services. CASBs automatically prevent sensitive data leakage, stop malware and other threats, discover and control shadow IT, block risky sharing, enforce security policies such as authentication and alerting, and ensure compliance.

Overview
• CASB is a vital component of modern cloud security, offering visibility, control, and protection for cloud data and applications.
• CASB enables organizations to prevent data leakage, enforce compliance, mitigate threats, and discover shadow IT.
• Without CASB, enterprises face increased risks from cloud usage, misconfigurations, and malicious activity.
• The ideal CASB solution is multimode, combining inline and API-based enforcement for complete data and threat protection.
• Zscaler CASB integrates advanced security capabilities into a zero trust architecture for unified, scalable cloud protection.
Why Is a CASB Needed Today?
With increased cloud adoption, CASBs have become a key element of enterprise security for their various cybersecurity, access control, and data protection functions. They give you back control over corporate data, in motion or at rest, in cloud platforms and apps. CASBs are critical because:
- The growth of cloud platforms and apps (e.g., Microsoft 365, Salesforce) has made traditional network security tools, such as data center firewalls, far less effective.
- IT teams don’t have the control they once had. Almost anyone can pick up and use a new cloud app, and IT can’t manually manage granular user access controls at that scale.
- They can apply policy to provide shadow IT control, data loss prevention (DLP), data security posture management (DSPM), and advanced threat protection.
The Role of CASBs for Businesses
By offering visibility into activity, security policy enforcement, threat detection, and data protection, CASBs enable businesses to confidently embrace the cloud while maintaining control and ensuring regulatory compliance. Let’s take a closer look at some of the concrete benefits.
Benefits of CASB
An effective CASB solution offers key benefits as part of a holistic cloud security strategy:
Visibility into Shadow IT and Risk
Amid the rise of remote work and BYOD, organizations need clear visibility into the users, devices, and SaaS applications accessing their cloud environments. With it, the risk of unauthorized access skyrockets. A CASB discovers your organization’s cloud app usage, reports on cloud spend, and assesses risk to help you create and maintain appropriate access policies.
Cloud Usage Management
Use of the cloud can be subject to an array of compliance mandates, especially in highly regulated industries like financial services, healthcare, and the public sector. A CASB can identify the greatest risk factors in your industry and set stringent data protection policies to help you achieve and maintain compliance across your organization.
Data Security and DLP
The volume of the world’s data doubles in size every two years, and data risk grows in kind. Combining a CASB with cloud DLP lets you see both see and remediate potential risks. With visibility into sensitive content traveling to, from, or between cloud environments, you have the best chance to identify incidents, enforce policy, and keep data secure.
Threat Prevention
In today’s IT ecosystem, cloud resources are usually the most vulnerable. With behavior analytics and threat intelligence, you can quickly identify and remediate suspicious activity, keep cloud applications and data secure, and bolster your organization’s overall cloud security posture.
How to Implement a CASB
At the highest level, implementing a CASB is a matter of assessing your needs, matching them to the right product, setting it up in the way that best suits your systems, and performing ongoing monitoring and audits. You could look at it in five steps:
- Assess your environment and make a plan. Understand the cloud services and apps in use, attendant risks, and your security policy and compliance needs.
- Select the right CASB solution for your needs. Just as important as finding the right product, find the right vendor—choose a partner you know you can trust.
- Integrate the CASB with your cloud services and user directories. Use SSO to enable secure user access and seamless authentication.
- Configure access, data sharing, DLP, and security policies. Depending on your industry, you may need to take special care with your policies around encryption.
- Enable real-time monitoring and threat detection. You’ll also need to regularly review and update your policies as your organization’s needs evolve.
How Do CASBs Work?
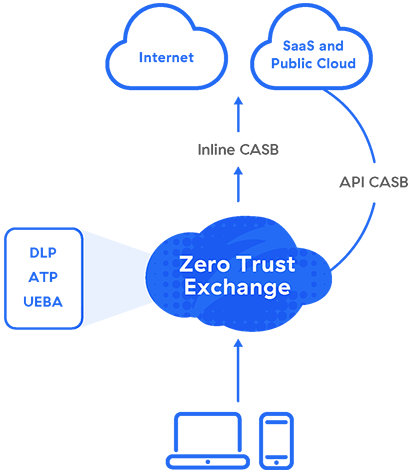
CASB solutions can take the form of on-premises hardware or software, but they’re best delivered as a cloud service for greater scalability, lower costs, and easier management. Whatever the deployment model, CASBs can be set up to use proxying (forward proxy or reverse proxy), APIs, or both—a multimode CASB.
Proxy
Because they need to operate in the data path, the ideal CASB is founded on a cloud proxy architecture. Forward proxies are more often used with CASB, ensuring users’ privacy and security from the client side.
A forward proxy intercepts requests for cloud services en route to their destination. Then, based on your policy, the CASB enforces credential mapping and single sign-on (SSO), device posture profiling, logging, alerting, malware detection, encryption, and tokenization.
API
While an inline proxy intercepts data in motion, you need out-of-band security for data at rest in the cloud, which CASB vendors provide through integrations with cloud service providers’ APIs.
What’s a Multimode CASB?
In proxy mode, CASBs provide inline policy enforcement that stops leakage and malware in real time. They can also integrate with APIs to scan SaaS apps’ contents, enabling them to find and respond to sensitive data patterns as well as threats such as ransomware. More recently, API integrations have been used for DSPM, by which CASBs remediate misconfigurations in applications.
CASBs that offer both proxy and API-based modes are called multimode CASBs. Beyond securing SaaS, they can protect IaaS such as Microsoft Azure and AWS S3. And rather than deploying a CASB as another point product, you can deploy it as part of an SSE platform to ensure consistent security, enhanced performance, and consolidated administration.
What Does Gartner Say About CASB?
Gartner first defined “CASB” in 2012, when organizations primarily used the technology to control shadow IT.
As its capabilities began to overlap more with secure web gateways (SWG), in 2019, Gartner defined the secure access service edge (SASE), a framework of cloud-delivered services that provide “comprehensive WAN capabilities with comprehensive network security functions (such as SWG, CASB, FWaaS, and ZTNA) to support the dynamic secure access needs of digital enterprises.”
In 2021, Gartner identified the security-centric slice of SASE as the security service edge (SSE), reflecting growing efforts worldwide to streamline complex, disjointed security stacks.
CASB and SASE
CASB and SASE complement one another, with CASB securing cloud interactions and data flows while SASE more broadly integrates cloud security, networking, and access control. SASE includes CASB by definition, enabling organizations to enforce policies and secure data as part of their network architecture.
Zscaler is a Leader in the Gartner Magic Quadrant for Security Service Edge (SSE).
Top Use Cases for CASB
1. Discover and Control Shadow IT
When your users store and share corporate files and data in unsanctioned cloud apps, your data security suffers. To counteract this, you need to understand and secure cloud usage in your organization.
Zscaler CASB automatically discovers shadow IT, revealing the risky apps visited by users. Automated, easily configurable policies then enforce various actions (e.g., allow or block, prevent upload, restrict usage) on individual apps and app categories.
2. Secure Non-Corporate SaaS Tenants
Users may use both sanctioned and unsanctioned instances of apps like Google Drive. Responding by either allowing or blocking the app entirely can encourage inappropriate sharing or hamper productivity, respectively.
Zscaler CASB can distinguish between sanctioned SaaS tenants and unsanctioned instances, applying appropriate policy enforcement to each. Preconfigured SaaS tenancy controls deliver automated, real-time remediation.
3. Control Risky File Sharing
Cloud apps enable unprecedented sharing and collaboration. As a result, your security teams need to know who’s sharing what in sanctioned apps, lest you risk letting dangerous parties get hold of your data.
Collaboration management is a key capability of any effective CASB. Zscaler CASB quickly and repeatedly crawls files in your SaaS tenants to identify sensitive data, check the users with whom files are shared, and automatically respond to risky shares as needed.
4. Remediate SaaS Misconfigurations
When deploying and managing a cloud application, precise configuration is key to ensure the app functions properly and securely. Misconfigurations harm your security hygiene and can easily expose sensitive data.
Zscaler DSPM integrates with your SaaS tenants via API to scan for misconfigurations that could jeopardize regulatory compliance.
5. Prevent Data Leakage
In addition to cloud resource misconfigurations that could enable data breaches and leaks, you need to identify and control sensitive data patterns in the cloud. A vast amount of such data is regulated under frameworks like HIPAA, PCI DSS, GDPR, and many others.
Zscaler's cloud native security platform provides unified data protection with cloud DLP and CASB capabilities. It ensures cloud apps are properly configured to stop data loss and noncompliance, backed up with advanced data classification techniques to identify and secure sensitive data wherever it goes.
6. Prevent Successful Attacks
Once an infected file gets past your organization’s security into one of your sanctioned cloud apps, it can quickly spread to connected apps and other users’ devices. That’s why you need a way to defend against threats in real time both at upload and at rest.
Zscaler CASB thwarts malware’s advances with advanced threat protection capabilities, including:
- Real-time proxy to prevent malicious files from being uploaded to the cloud
- Out-of-band scanning to identify files at rest and remediate threats
- Cloud sandboxing to identify even zero-day malware
- Agentless cloud browser isolation to secure access from unmanaged endpoints
Zscaler CASB
Zscaler delivers multimode CASB as a service along with SWG, ZTNA, and more as part of our comprehensive Zscaler Zero Trust Exchange™ platform to help you eliminate point products, reduce IT complexity, and inspect traffic in a single pass. Your administrators simply configure one automated policy for consistent security across all cloud data channels.
Inline Security for Cloud Data in Motion
High-performance forward proxy and SSL inspection provide critical real-time protection:
- Shadow IT discovery and cloud app control identify and secure unsanctioned apps without requiring network device logs
- DLP measures prevent uploads of sensitive data to sanctioned and unsanctioned apps
- Advanced threat protection stops known and unknown malware in real time with machine learning-powered cloud sandboxing
- Browser isolation streams sessions as pixels for BYOD to prevent data leakage without a reverse proxy
Out-of-Band Security for Data at Rest
API-based scanning of SaaS apps, cloud platforms, and their contents automatically enhances your security:
- Predefined and customizable DLP dictionaries identify sensitive data in SaaS and public clouds
- Collaboration management functionality crawls apps for risky file shares and revokes them according to policy
- Cloud sandboxing scans data at rest to identify and respond to zero-day malware and ransomware
- DSPM auto-discovers and classifies risky data assets across SaaS, PaaS, public cloud, on-premises, and LLMs
Achieve stronger SaaS security with Zscaler CASB.
Suggested Resources
FAQ
CASB solutions are essential for organizations of all sizes that rely on the cloud to store sensitive data, collaborate via SaaS apps, or manage cloud resources. Industries like healthcare, finance, and the public sector benefit most from CASBs due to stringent data regulations, but they are also critical for businesses adopting remote work, BYOD policies, or facing threats from shadow IT adoption.
A cloud access security broker (CASB) is a security tool that enforces policies between users and cloud services. It helps organizations ensure cloud data protection, prevent data leakage, and mitigate security threats. CASBs offer pivotal capabilities like data loss prevention (DLP), shadow IT discovery, compliance enforcement, and seamless integration with SaaS and IaaS platforms.
To choose the right CASB, assess your organization’s cloud security needs, current risks, and compliance requirements. Look for features like multimode deployment (proxy and API integrations), real-time data monitoring, advanced DLP, threat prevention, and shadow IT control. Partner with a trusted vendor that offers scalability, ease of implementation, and integrations into broader security service edge (SSE) platforms.
While CASBs provide crucial cloud security functions, they are best used as part of a comprehensive security strategy. They work seamlessly alongside solutions like secure web gateways (SWG), zero-trust network access (ZTNA), and DSPM to enforce unified protection. Deploying CASB within wider frameworks such as SASE or SSE ensures broader cloud and network security coverage.
CASBs are invaluable for shadow IT visibility because they automatically discover unsanctioned applications that employees use without IT approval. By doing so, CASBs help organizations control risky file-sharing, enforce proper access policies, reduce security vulnerabilities, and mitigate overall cloud usage risks.
Multimode CASB solutions offer both inline protection (via proxying) and out-of-band scanning (using API integrations). This dual approach enables real-time policy enforcement to prevent data leakage and malware while providing visibility into data at rest to help detect misconfigurations and manage compliance. Multimode CASBs allow businesses to seamlessly secure both SaaS and public cloud environments.
CASBs enforce compliance by identifying sensitive data subject to GDPR or other regulatory frameworks, applying stringent policies to its storage, transmission, and usage. Advanced features like cloud DLP scan for regulated data patterns, prevent unauthorized access, and remediate risky file activity for adherence to compliance mandates.
CASBs amplify DLP by proactively scanning sensitive data moving within sanctioned and unsanctioned cloud applications. Real-time proxy capabilities enforce policies on data uploads, downloads, and sharing, while API integrations secure data stored at rest. Combined, these features prevent leakage and unauthorized access to sensitive data, bolstering cloud DLP effectiveness.