/ What Is Least-Privileged Access?
What Is Least-Privileged Access?
Why Is Least-Privileged Access Important?
As higher volumes of data move to and through public and multicloud environments, and cyberattacks such as ransomware become more frequent and sophisticated, organizations are searching for ways to protect their growing attack surfaces and reduce security risk. This is where least-privileged access—also called the principle of least privilege (POLP) or the principle of minimal privilege—comes into play as one of the foundational elements of a zero trust approach.
Least-privileged access comprises three areas of consideration: user identity authentication, device security posture, and user-to-app segmentation. We’ll cover these in more detail shortly.
Least-Privileged Access and Zero Trust
Before we move on, let’s look at how these two terms relate to one another. “Least-privileged access” can sound a lot like “zero trust,” and indeed, they’re closely related but still crucially different concepts.
You can think of least-privileged access like a key card you give to each of your employees that’s uniquely coded to their job function. This lets you tailor access controls so most users can access common areas like Microsoft 365, but only some have privileged credentials to more sensitive material, such as financial information, HR data, and so on, reducing the risk of excessive permissions leading to data breaches.
Zero trust security takes this a step further, not granting trust simply because an employee has a unique key card. Before granting access, a zero trust policy establishes a user’s identity and full context for the connection request, such as the user’s device, their location, the application in question, and its content. This way—to extend the metaphor—another user can’t simply pick up a key card, take on its access rights, and start getting into places they don’t belong.
How Modern Least-Privileged Access Works
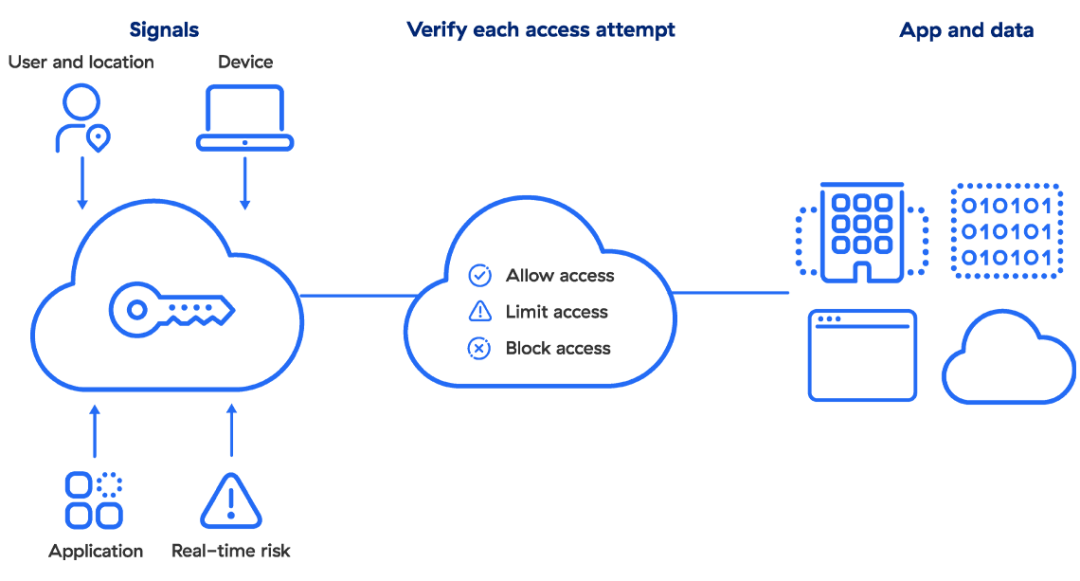
Today, least-privileged access and zero trust are essentially inseparable, with a modern approach incorporating user identity authentication, device security posture, and user-to-app segmentation in its controls. Let’s examine these three core elements.
User Identity Authentication
This is how you determine whether your users are who they claim to be. Identity and access management (IAM) providers and services (e.g., Okta, Azure Active Directory, Ping Identity) create, maintain, and manage identity information while offering various provisioning and authentication services.
Device Security Posture
A well-intentioned user with elevated privileges can still fall victim to malware. Paired with continuous assessment of endpoint security posture (provided by the likes of CrowdStrike, VMware Carbon Black, SentinelOne, etc.), modern least privilege policies can modify even a privileged user’s permissions based on their current device health.
User-to-App Segmentation
The traditional way to limit network exposure and lateral movement is network segmentation, using firewalls inside the enterprise network to restrict segments to privileged accounts. Although it’s key to limit internal lateral movement, this approach is complicated and doesn’t provide the granular control modern organizations need.
User-to-app segmentation is made possible with a zero trust network access (ZTNA) service, which enables granular segmentation through IT-managed business policies, not a stack of firewalls. ZTNA connects verified users directly to the applications they’re authorized to use without ever connecting them to your network, making lateral movement impossible. This access policy is extended to both remote and on-premises users, regardless of their location, with identical security controls.
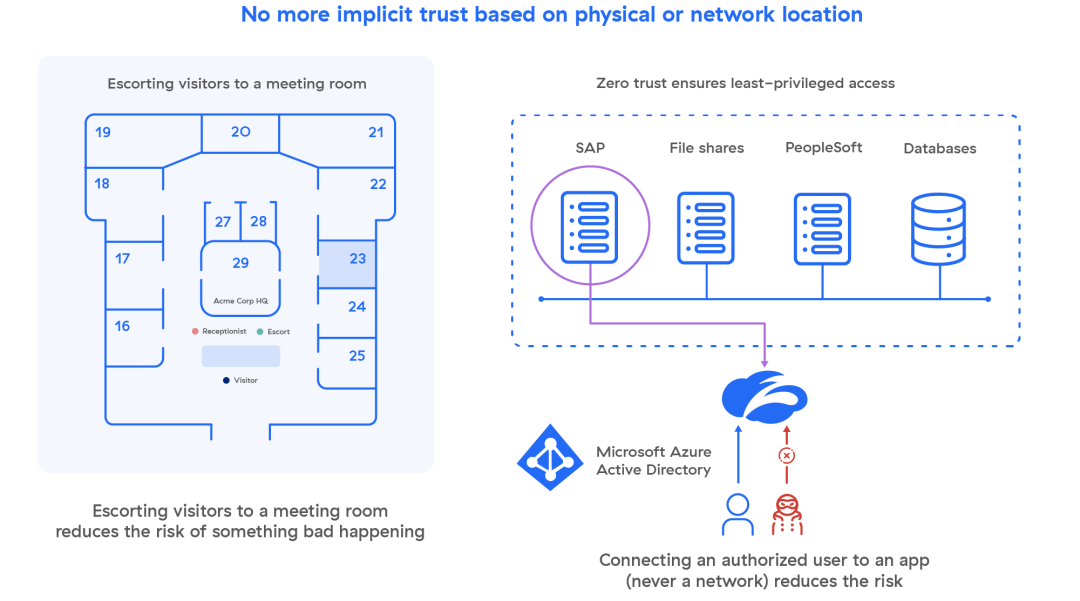
Least-Privileged Access Benefits
The convergence of the three core elements with an effective ZTNA service forms the basis of a strong, resilient security posture for your organization, where:
- User accounts are always authenticated before access is granted
- Devices are monitored and user access levels adapt based on security posture
- App segmentation minimizes lateral movement, eliminating the need for complex firewall tuning
A Word on Administrative Privilege
Of course, your administrator accounts require some further consideration. Superusers carry an immense burden of trust, and by nature, they can’t work with limited access. The traditional solution here is privileged access management (PAM), which manages your entitlements, accounts, and operating systems at the data center level. However, the shift to the cloud is making PAM less effective, necessitating a different means of distributing administrative access.
Today, the rise of DevOps means your cloud may see thousands of permission changes in a day. Cloud infrastructure entitlement management (CIEM) is succeeding here where PAM has begun to fail, as effective CIEM can manage and inventory cloud entitlements, perform privilege audits, detect and remediate privilege creep, confer admin rights to services, and carry out various other functions at a scale and level of complexity PAM can’t reach.
CIEM is an important consideration for today’s cloud environments as you’re planning or refining your least-privileged access approach.
How to Implement Least-Privileged Access In Your Organization
Achieving modern least-privileged access with zero trust is easier than it sounds, with just three basic steps:
- Adopt an identity provider (IdP) service. With the popularity of single sign-on services today, many organizations already leverage an IdP.
- Layer on a device posture service. Combining device health monitoring with flexible device policy lowers the risk compromised endpoints pose to your critical systems and data.
- Enable a ZTNA service. This allows you to eliminate both lateral access and internal firewalls with one technology. Some ZTNA services can be fully deployed in just a few hours.
How Zscaler Helps with Least-Privileged Access
Traditional firewalls, VPNs, and private apps all create a massive attack surface. Hackers and other bad actors can see and exploit vulnerabilities, externally exposed resources, and outdated network security solutions like VPNs put users on the network, giving attackers easy access to sensitive data. Plus, they can't scale or deliver a fast, seamless user experience—they require backhauling, introduce added costs and complexity, and are too slow to serve today's distributed workforce.
As the world’s most deployed ZTNA platform, Zscaler Private Access™ applies the principles of least privilege to give users secure, direct connectivity to private apps while eliminating unauthorized access and lateral movement. It can be deployed in hours to replace legacy VPNs and remote access tools with a cloud native, holistic zero trust platform. Zscaler Private Access is ZTNA, evolved.
Zscaler Private Access delivers fast, secure, and reliable private app access for all users from any device or location.
Suggested Resources
Frequently Asked Questions
As the name suggests, role-based access control ties access privileges to the function or functions that an employee serves within an organization. For example, developers may have certain permissions within a content management system that administrators would not need access to.
This falls into least-privileged access in that the administrators are receiving as few permissions to an application as possible, where their counterparts may need slightly more to perform a more granular task.
A superuser, also known as a root, is an account that’s been given extended permissions or access rights in order to perform a wider breadth of tasks. This account is trusted to a person within an organization who can perform a litany of tasks not designated to regular users. As such, superusers are not bound by the principle of least privilege.
Also known as access creep, it refers to the slow accumulation of unnecessary permissions, access rights, and outright privileges by individual users. This can happen when, for example, an employee is tasked to work on a short-term project wherein they need an additional permission to an application.
If this happens often to many employees, privileges can become overextended over time, and it can pose a risk to organizations if too many permissions become extended to too many users. It’s the gradual pace at which these permissions become extended that gives this phenomenon its ‘creep’ moniker.