OVERVIEW
Powering the next wave of digital transformation
Fifth Generation Wireless (5G) and edge computing are accelerating innovation across industries, ushering in a new meta in connectivity.
DETAILS
5G and edge workloads are attractive targets for cyberattacks
Once a threat actor gains access to the network, they can disrupt operations as well as steal and encrypt sensitive data.
Every internet-facing firewall, on-premises or in the cloud, can be discovered and attacked

Devices (UE) lack sufficient security and can easily be compromised, serving as beachheads for finding high-value targets

A single infected device on a routable network can infect everything on the network

Architectural diagram
Risk of compromise: An open system architecture that enables massive device connectivity
RISK: IoT/OT systems can be easily exploited, and firewalls are not designed to inspect TLS/SSL traffic at scale
A large, routable network: Connects branches, factories, data centers, and public clouds to enable communications
RISK: A single infected device can infect everything on the network
Castle-and-moat security: Establishes a security perimeter between the corporate network and internet
RISK: Every internet-facing firewall can be discovered and exploited

HOW IT WORKS
Zscaler zero trust architecture for private 5G
Secures and simplifies private 5G deployments for centralized 5G Core
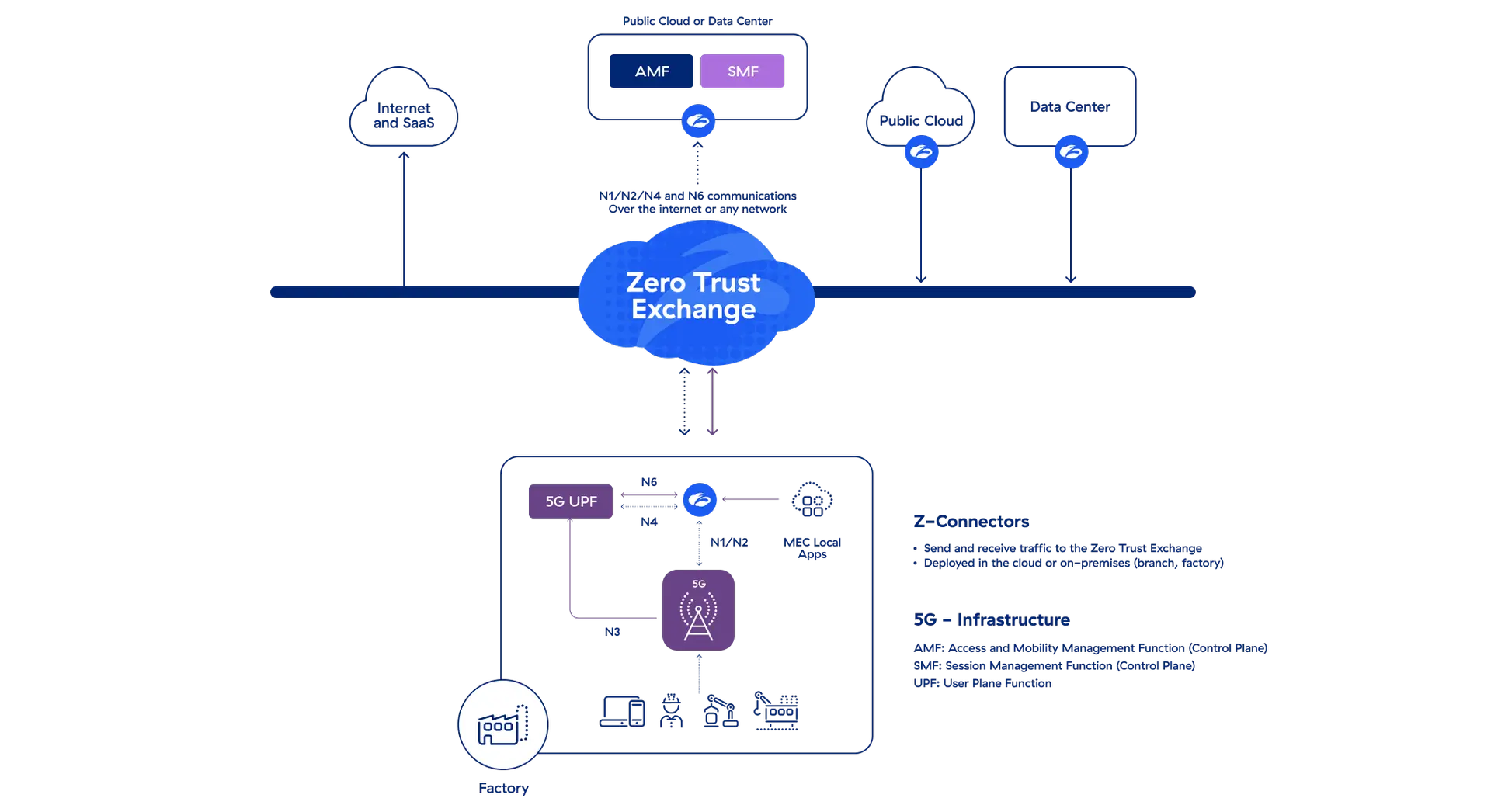
- Secure site-to-site connectivity over the internet without a routable network (5G UPF to Core)
- Ensure users and devices (UE) are not on the same routable network as apps in the MEC, DC, and cloud
- Minimize the egress and ingress attack surface
- Identify workload vulnerabilities, misconfigurations, and excessive permissions
- Prevent compromise and data loss with inline content inspection
- Quickly resolve performance issues with visibility into device, network, and app performance
Together, we're empowering customers to securely embrace private 5G





“With Zscaler zero trust, we can protect [mission-critical] workloads by securing all internet, device, and workload communications.”
—Sebastian Kemi, Chief Information Security Officer, Sandvik AB

“[With Klas and Zscaler], the warfighter now has unprecedented secure, granular access to warfighting applications at the tactical edge.”
—Carl Couch, Director of Engineering, Klas Government



![With Zscaler zero trust, we can protect [mission-critical] workloads by securing all internet, device, and workload communications. zscaler-customer-sandvik](/_next/image?url=https%3A%2F%2Fcms.zscaler.com%2Fsites%2Fdefault%2Ffiles%2Fimages%2Fcase-study-teaser%2Fzscaler-customer-sandvik.jpg&w=1920&q=75)

