Cloud security is a complicated endeavor that requires different technologies to work together to attain the ultimate outcome: protecting today’s digital organizations. Platforms like Google Cloud can prove to be a valuable tool in achieving this outcome—that is if vendors use it as more than window dressing.
Not all clouds are the same
Zscaler has spent more than 10 years developing, scaling, and enhancing its purpose-built, multi-tenant security cloud. And the company has gone to significant lengths to explain why this type of cloud—a service-edge cloud—is a requirement for delivering high-performance, inline security from the cloud.
The popular Google Cloud Platform (GCP) is a different kind of cloud—a destination cloud. It is not designed and optimized for edge network traffic processing, but it can be very useful in security nevertheless. Zscaler has been leveraging GCP to enhance the Zscaler platform of cloud security services. Allow me to explain how.
I have led the machine learning and AI team at Zscaler since my company, TrustPath, was acquired by Zscaler, and we couldn’t do what we do today without GCP. We use many of its services—from basic computing, storage, database, and monitoring services all the way to location services and AI platform services. One of the platform’s differentiated services is Google Cloud BigQuery Service, which can process in seconds what it would have taken days to accomplish in the past. Another powerful service we use extensively is the Tensor Processing Unit (TPU) service, which is Google’s purpose-built hardware service optimized for machine learning and AI.
We’ve used GCP for a long time—again, not as a place to pass around customers’ network traffic, as some companies do, but to leverage its massive AI and big data power to deliver intelligence to our Zscaler cloud and our customers.
The total number of utilized computing cores in one of the Zscaler GCP clusters
Machine learning and the Google Cloud
Machine learning algorithms build a mathematical model based on “training” data. In one of our use cases, we collected millions upon millions of file samples on the GCP storage service as the training data. We then trained the machine learning models on the GCP computing service—we also leverage Google’s AI platform to speed up the model training time. We leveraged the trained model and moved it to the Zscaler cloud to make threat detection in real time. Most of our use cases are about detecting, predicting, and blocking unknown threats, which are threats without signatures yet from the security intelligence feeds.
Amit Sinha, Zscaler CTO and EVP, laid out three fundamental requirements for machine learning to work in the cybersecurity industry in a recent Forbes article. Within Zscaler, machine learning turned out to be incredibly effective precisely because of the way we leverage the Google Cloud, with the marriage of Zscaler’s deep security domain knowledge and the TrustPath team’s industry-leading machine learning expertise, along with the vast amount of data the Zscaler cloud processes every day.
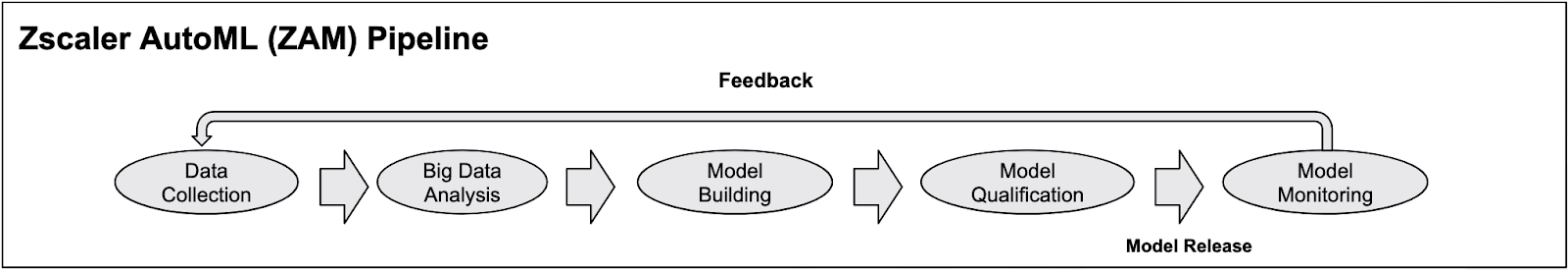
The Zscaler automated pipeline for data collection and model training
As a result of this marriage, the Zscaler cloud, enhanced by machine learning models trained on GCP, is able to detect anomalies and identify new malware as it surfaces, even if it has never been seen before. Furthermore, the machine learning modules that run in the Zscaler cloud security platform provide verdicts or classifications on unknown threats very quickly, often in milliseconds.
The real power of GCP for security
While Zscaler has been harnessing the power of the Google Cloud for years, some vendors have only recently begun using this powerful tool. Even if these companies are looking at the tools in GCP to improve their cloud security offerings, it takes quite a bit of time to leverage those tools to their greatest benefit.
However, as I touched on earlier, some networking security vendors use Google Cloud simply as a way to route their customers’ network traffic. Google Cloud gives them the appearance of having a large security cloud when, in reality, they are simply moving legacy products that are designed for physical environments into the cloud and calling it a cloud service.
The Zscaler cloud was built in the cloud...for the cloud. One hundred data centers spread across five continents give the Zscaler cloud the power to process 65 billion transactions per day as it provides inline security that’s always close to the user. And, using tools from the Google Cloud to enhance Zscaler technology, we are able to block thousands of threats every second to help keep our customers safe.
Don’t judge a book by its cover
Organizations have many things to consider when contemplating cloud security, and it's important to remember that not everything is as it appears. What looks like a true cloud offering on the surface may actually be nothing more than terrestrial-based devices being force-fit into the cloud—devices that can't operate inline efficiently, don’t take full advantage of GCP's real strength and intelligence, and won't scale elastically—from vendors that don't offer SLAs on performance.
In today’s digital society, and the vast and evolving threat landscape, it is critical to take a close look at vendors to determine which have invested in technology designed to protect your future and which are more invested in the status quo.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Howie Xu is the Zscaler VP of Machine Learning and AI





