Zscaler Blog
Get the latest Zscaler blog updates in your inbox
SubscribeBeans, Bullets and Bytes: Realizing the Promise of Zero Trust
There is an old adage that says, “amateurs talk strategy and professionals talk logistics”. The quote is attributed to Gen Omar Bradley who was known for his attention to detail in planning. Moving beans and bullets is a critical logistical activity in all terrestrial domains of warfare. However, for missions in the cyber domain, it is just as critical to move “bytes” in the form of mission critical information. Examples of mission critical information include real-time battlefield intelligence, weapon systems sensor data and blue-force tracking telemetry. Zero trust is more than just a cybersecurity architecture - it is fundamental to connecting fighters and decision makers, connecting sensors to shooters, as well as any other sensitive intelligence data that must be communicated. A true zero-trust architecture enables secure connectivity that is location independent, device independent, and network independent; thereby making joint and coalition forces more agile.
Carl von Clauswitz, the 17th century military strategist spoke on the importance of Lines of Communication (LOC) while observing Napoleon, and those observations are as relevant today in all warfighting domains as it was then. As Clausewitz wrote, the LOC was necessary to move critical supplies to the frontline, as well as provide an egress route for forces if they must move away from the frontline. Security of the LOC is paramount. Every military branch has incorporated LOCs into their own operational art for mission success. The Army establishes Ground LOCs, the Navy must secure Sea LOCs, and the Air Force identifies Air LOCs into and out of the area of operations (AOR). In the cyber domain, this concept is also relevant. Zero trust, as a cybersecurity paradigm, enables cyber operators to securely move critical information, in the form of bytes, to the frontline and everywhere it is needed for mission success.
The cyber domain is unique
Much has been written about the cyber domain vis-a-vie the other domains. In 2011, former Air Force Chief of Staff, General Larry Welch, made the point that every military domain must accomplish certain activities to be effective. Those activities are:
- Passive Defense
- Active Defense
- Exploitation (Operational Prep of the Domain)
- Attack
- Defining and Developing Needed Capabilities
However, in the cyber domain, there is one other activity that makes it unique to the other warfighting domains: constructing. In cyber we construct the operating environment. He also cautioned that there is a temptation to construct EVERYWHERE friendly forces will operate in. In other words, just because we can build networks to host national security information, we shouldn’t feel that we must own all the network infrastructure where the military will operate.
Effectively operating in the cyber domain is similar to operating in the sea domain, where it is not possible to control all bodies of water on the surface of the earth. Therefore, the Navy must secure only that portion of the sea where the service must operate, or the Sea Line of Communication (SLOC). Zero trust enables cyber operators to secure only the necessary portion of the cyber operating environment within the cyber domain. This secure portion of the cyber domain for military use becomes a Cyber Line of Communication (CLOC) where bytes can be effectively and securely communicated across the battlefield.
Cyber Lines of Communication
Establishing secure CLOCs to move information across the military operating environment is the operational imperative behind the DoD’s Zero Trust Reference Architecture (RA). The RA identifies 7 principles as guidance across the department as each military department implements zero trust. The first principle: Assume no implicit or explicit trusted zone in networks. As described above, relying on secure network technologies (Virtual Private Networks, Firewalls, Cross-Domain Solutions, etc.) will not protect the information resident on those networks. Each of the other principles build on the first and provide components that make use of the architecture to deploy a CLOC.
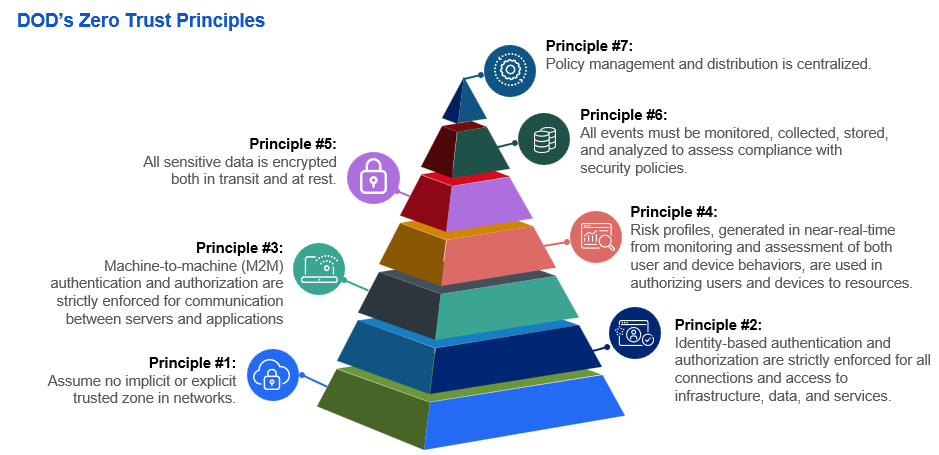
There are a couple of operational use cases that are top of mind in the department today where mission success requires leveraging CLOCs through zero trust. The first is Agile Combat Employment (ACE). The ACE vision requires a lean and light force that is capable of rapidly dispersing throughout an area of responsibility (AOR) with a minimal footprint. Cyber operators typically bring many pallets of information and computing technology (ICT) to establish a forward operating location. The ICT brought forward includes networking hardware, security tools to protect the network, and servers with mission critical apps. With zero trust establishing CLOCs to securely access cloud-based mission critical apps, the amount of equipment necessary is dramatically reduced and thus becomes a force multiplier to achieve the ACE vision.
So how does zero trust make it possible to reduce the deployable footprint? A cloud-based security solution, that operates in-line between the user and the application, dramatically shrinks the requirement to leverage hardware security appliances that attempt to secure the network (violating principle #1 in the RA) and protect users. Creating a CLOC through zero trust is essentially creating an HOV lane that rapidly moves critical information, securely, from users to applications, or sensors to shooters, or geospatial data to common operational pictures. To accomplish this, each connection is established after authorizing the identity of the user (RA Principle #2), a risk assessment is determined (RA Principle #4), the communication is encrypted (RA Principle #5), and the connection is monitored for nefarious activity or changes in access policy (RA Principle #6). Zscaler delivers a zero trust CLOC that meets the DoD’s principles and can be implemented in the cloud, or in an on-premises variation for early stages of building out a Forward Operation Location (FOL).
The second use case is the challenge of operating in a coalition environment. Since Zscaler is creating a bespoke connection that is segmenting the user directly to the application, there is no need to build separate networks to host coalition data and information. Instead, a coalition application is all that is necessary to enable secure coalition data exchanges. As RA Principle #2 advises, there must be an identity which is managed to authorize access to data and information. With a coalition identity and zero trust access through a CLOC, coalition partners can be rapidly on-boarded and granted access. Often in just minutes!
Zscaler has partnered with Service Now to build a notional Mission Partner Environment (MPE) identity repository of coalition partners. MPEs allow the military and its trusted partners to communicate, collaborate and to share sensitive, classified information securely and in real-time. Once an individual partner is identified as participating in the coalition operation, a Service Now workflow creates and provisions an identity in Microsoft Active Directory, that can be exported to any SAML 2.0 Identify Provider (IdP). Once the identity is established, all the Zscaler security functionality can be made available to establish the bespoke CLOC between the coalition partner and the mission partner application. This same workflow can be used for joint access, so this solution enables rapid access to Coalition and Joint All-Domain Command and Control data and information.
While zero trust is often viewed as something new, it has a long history in industry and the private sector. More importantly, from the early days of network-centric warfare over 20 years ago, the DoD has been tackling the challenge of getting the right information to the right place at the right time. Viewing this challenge as a logistics activity through the establishment of Cyber Lines of Communication, in a domain that cannot be completely owned and controlled through military operations, helps establish the correct pathways to enable mission success.
Was this post useful?

Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




