The Zscaler Zero Trust Exchange is built on the world’s largest security cloud, which brokers over 190 billion daily transactions (that’s roughly 50x the number of daily Google searches), and extracts over 300 trillion signals each day. The ThreatLabz research team analyzes this massive data set to monitor threats, improve security controls, and to publish in-depth research on the evolving threat landscape.
Today, we released what may be our most-anticipated annual study, The State of Encrypted Attacks. In this report, ThreatLabz looks at the use of encrypted traffic (HTTPS, SSL, TLS) -- which is often considered to be safe and trusted -- to examine attacks and security risks.
The report found that more than 80% of attacks now use encrypted channels, up from 57% in last year’s study.
This should serve as a wake-up call: organizations must inspect their encrypted traffic just like any other traffic. This is problematic as it’s resource-intensive to decrypt, inspect, and re-encrypt traffic with legacy hardware-based security tools. This means shelling out more money for more devices, plus the added side-effect of slowing traffic to a crawl. But, by failing to do so, they’re giving malicious actors an easy entry into their environments.
Of course, there’s another option: using a cloud-native proxy architecture such as Zscaler allows for scalable inspection of all encrypted traffic without the performance degradation or added expense and complexity of legacy hardware.
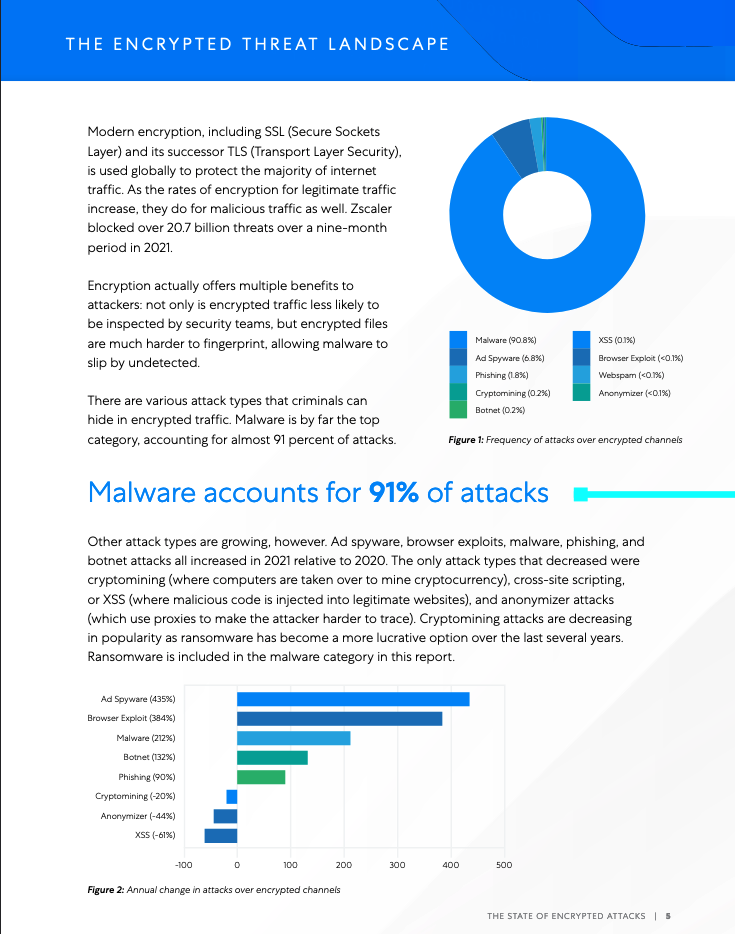
Key Findings
In January through September 2021, threats over encrypted channels rose 314% when compared to the same period the previous year, which itself was a 260% rise from 2019. Encryption is not a deterrent to attackers, and in fact offers them multiple advantages: encrypted traffic is less likely to be inspected by security teams, and without SSL inspection, malicious files are much harder to fingerprint, allowing malware to slip by undetected.
Some top trends:
- Tech is a huge target: Attacks on tech companies increased by 23 times(!) year-over-year; attacks on retail and wholesale companies increased by 841 percent.
- Critical services saw some relief: Healthcare was the biggest target in 2020, but threats have fallen off precipitously, along with attacks against government organizations. In the wake of big attacks, such as the one against Colonial Pipeline, there was increased attention from law enforcement, which made these industries less attractive as targets.
- The UK and U.S. are the top targets of encrypted attacks: India, Australia, and France round out the top five.
- Tactics are changing: Malware is up 212 percent and phishing is up 90 percent, whereas cryptojacking is down 20 percent. Attack trends are changing with ransomware gaining profitability and therefore popularity.
The State of Encrypted Attacks goes into great detail into all of these statistics and more -- including top attack types and threat families, most targeted applications, industry data, and in-depth case studies.
How to protect yourself
Zero trust strategies and architectures -- in which you trust nobody and inspect and authenticate everything -- are the most effective means of protecting your organization from encrypted attacks, as well as other advanced cyberthreats. Zscaler’s tenets of zero trust include:
- Preventing compromise by using cloud-native proxy architecture to inspect all traffic in-line and at scale, enforcing consistent security policies.
- Preventing lateral movement by connecting users directly to applications (rather than the network) to reduce the attack surface, and by containing threats by using deception & workload segmentation.
- Preventing data theft by inspecting all internet-bound traffic including encrypted channels to prevent data loss.
These tenets align directly to the attack chain, which typically involves three distinct stages. Attacks start with an initial compromise of an endpoint or asset exposed to the internet. Once inside, the attacker undergoes lateral propagation, performing reconnaissance and establishing a network foothold. Finally, attackers take action to achieve their objectives, which often involves data exfiltration. Therefore, your defenses should involve controls for each of those stages:
Security controls to prevent compromise:
- Audit your attack surface, stay up-to-date with security patching, and fix any misconfigurations that may exist.
- Move any internet-facing applications behind a cloud proxy that brokers the connection and eliminates vulnerable backdoors.
- Inspect all of your traffic!
Security controls to prevent lateral movement:
- Use microsegmentation to reduce access to data and applications, even for authenticated users. With Zscaler, the network is irrelevant to application access: you simply connect users directly to the application needed without risking any unnecessary exposure.
- Use dynamic defense strategies such as deception, which uses decoys to lure attackers and alert security teams of lateral movement or compromised users.
Security controls to prevent data theft:
- Disrupt command & control callback activity as well as data exfiltration attempts by inspecting all internet bound traffic with full SSL inspection to apply consistent security and data loss prevention policies.
Learn more -- download your copy of the report today!





