For the past few months, the Zscaler ThreatLabZ research team has seen a number of AutoIt and .NET samples from different malware families using what is being called Frenchy shellcode. The name is so given because of the mutex name it creates: frenchy_shellcode_{version}. In this blog, we will provide a brief analysis of a .NET sample using the Frenchy shellcode and also provide an overview of various malware types that are using it.
As the execution of the malware begins, it extracts an embedded compressed resource with the name asmz://4da3bcc9092d2b15c67c8bb6a3248c6d/279552/z. When decompressed, this resource turns out to be a dynamic-link library (DLL) file, which is also .NET compiled with the MD5 2d80d567add3e9ebe93118c28fd96ad8.
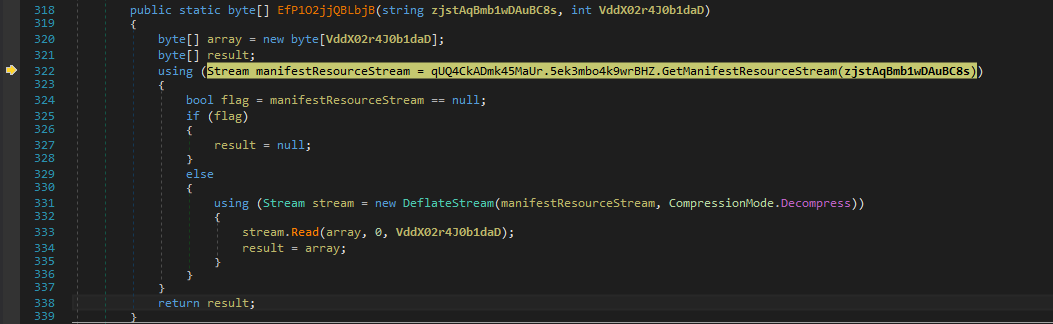
Figure 1: Decompression routine
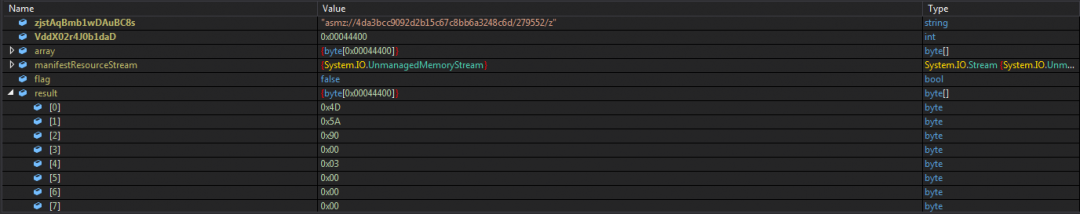
Figure 2: Compressed resource name stored in the variable
Control is transferred to this extracted DLL by invoking one of its routines named Average().
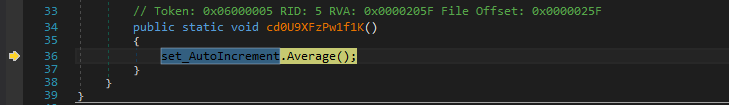
Figure 3: Average() function invoked in the extracted DLL
During execution, this DLL extracts the embedded AES-encrypted resource with the name 501Yek31KY. The AES key used for decryption is hardcoded with the value zlauDo4j2s76f3bAu7vJla9qxo4T9fDA. On decryption, the file turns out to be another .NET compiled executable with the MD5 9f93df82804d1467ba0096f91ecf091b.
- When execution begins, the executable performs two checks for virtual environment detection and terminates itself if either of the two is successful:
1. If SbieDll.dll is present
2. If the caption of the main window of any of the running process is empty
- For persistence, it creates a copy of itself in the %APPDATA%/Tasks/ folder with the name ThumbnailExtractionHost.exe, a VBS file with the name vTzzHA5v.vbs in the same folder to invoke ThumbnailExtractionHost.exe and a URL file in the startup directory with the name 89f429NZ.url to invoke vTzzHA5v.vbs.
- Finally, the Frenchy shellcode and the main malware binary are extracted. This executable contains two resources encrypted with Advanced Encryption Standard (AES). One resource with the name 9BMPzLT7ztLkxO7r contains the Frenchy shellcode and another with the name HC8354RuK8FCQSpg contains the main malware binary.
Figure 4: AES encrypted resource – malware payload
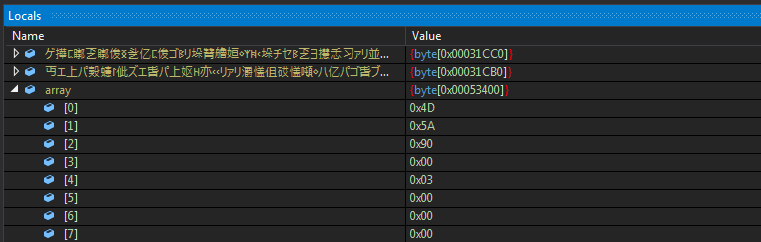
Figure 5: Extracted main malware payload [MD5: ac8ef8b4aeede1adab7366ca7e5a75be (AgentTesla)]
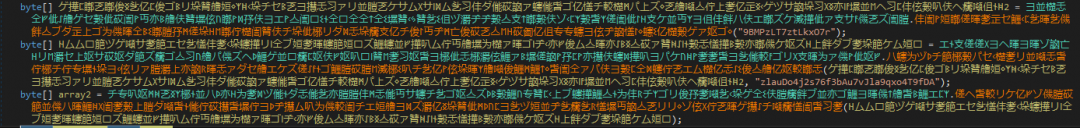
Figure 6: AES encrypted resource – Frenchy shellcode
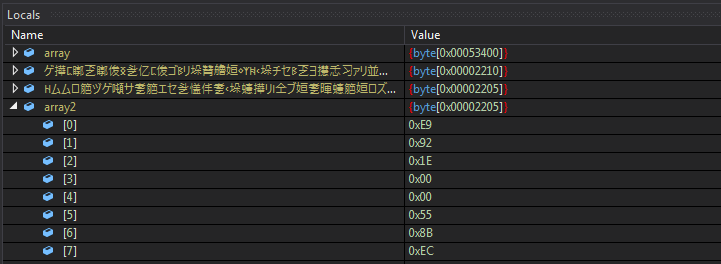
Figure 7: Extracted Frenchy shellcode [MD5: abdb5f121849f3f3718768d37abe0173]
Memory is allocated for the shellcode and main payload. Control is transferred to the Frenchy shellcode by creating a delegate using its memory location pointer along with two arguments:
- Currently executing binary full path
- Pointer to memory location of main payload
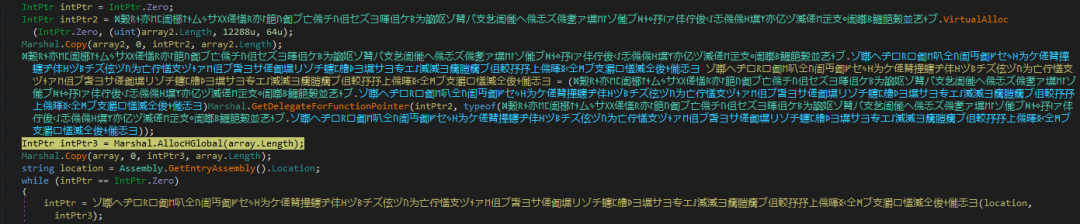
Figure 8: Control transferred to Frenchy shellcode memory location
Frenchy Shellcode Analysis
The main functionality of the shellcode is to perform hollow process injection, which injects malicious code in system memory. Execution of the shellcode starts with a relative jump instruction with the two arguments passed to the shellcode available on the stack.
Following the jump instruction, all the strings that will be used by the shellcode are generated on the stack. The interesting thing that this shellcode does is map all the required DLL again in the memory and make further calls via these newly loaded DLLs. This function helps bypass API monitoring that is done by some sandboxes in the user space. Four DLLs, namely advapi32.dll, ntdll.dll, user32.dll, and kerne32.dll, are mapped using the ZwOpenSection and ZwMapViewOfSection APIs. The DLL name used for ZwOpenSection is in the following format: \\KnownDlls32\\{dll_name}.dll.
Once the kernel32.dll is loaded, Frenchy shellcode extracts the address of LoadLibrary and GetProcAddress to load further required DLLs and extract necessary API addresses.
Now, when this initialization phase is complete, the shellcode’s main functionality begins. First, it creates the mutex with the name frenchy _shellcode_{version} where {version} is 002 in this case.
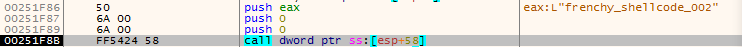
Figure 9: Frenchy shellcode version 002
Frenchy shellcode creates a process of currently executing binary in suspended mode.
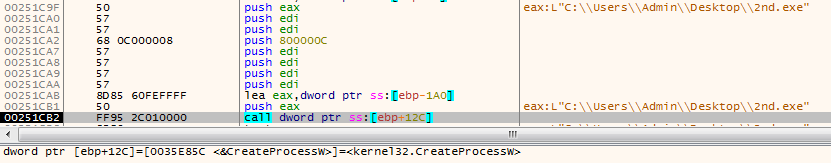
Figure 10: Creating new process in suspended mode
It creates a new section to be shared with the newly created process.
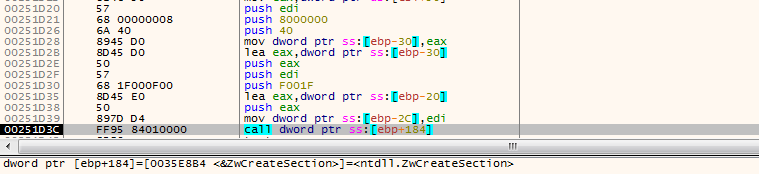
Figure 11: Shared section
Finally, the shellcode maps the view of this section into a newly created process, copies the main malware payload to this mapped view, modifies and sets the context of the newly created process, and starts the process main thread by calling NtResumeThread.
Malware variants using the Frenchy shellcode:
Win32.Backdoor.404Keylogger 6a8a308fd9d93877405edddaca2dc0b1
Win32.Backdoor.AgentTesla ff87170119ffe5da1a9933eac4813e89
Win32.Backdoor.AysncRAT 4e0620db87741809db739b36d493efd3
Win32.Backdoor.DarkComet aca05d97aa34360a18ce7e4a331195b8
Win32.Backdoor.HawkEye c1da6168e4ce782169295858057d6a82
Win32.Backdoor.Keybase db5fe533c78602a3d4e5a2a307782855
Win32.Backdoor.LimeRat 7f3b73f4680cd45b2f06cd991c26b60a
Win32.Backdoor.Nanocore d18509eb899f634f579e154b226c1f72
Win32.Backdoor.NetWiredRC 2d1ed53e7af0864f0916a4ce4f5e40b7
Win32.Backdoor.NjRat a7b38bf292212efd6c0bf11060483b19
Win32.Backdoor.NjRatLime 88c674e2dcd55b5e8672c1a063d06fd4
Win32.Backdoor.PhoenixKeylogger 382609b2a5c90f287b466f55911238d2
Win32.Backdoor.PredatorLogger 16cbd896990793871fd3fd7bcd23cf1a
Win32.Backdoor.QuasarRAT db07aca234c3f12a141760cfc6a46e0e
Win32.Backdoor.RemcosRAT 4ef1c56657d74aa09d77573273f99750
Win32.PWS.AZORult 6e33a3075b667eab19647f1d149a510f
Win32.PWS.FormBook 6e685961cc335b33d05e6415700fcf96
Win32.Ransom.Adame 20716b0abbf051ec151fecc0cc957145
Win32.Ransom.Phobos 0e1b676f95c0e51163178ffdd99817c8
Win32.Trojan.APT33 9aa2f7959f31196f6c5aa37ae3c5a2ae
Conclusion
Zscaler ThreatLabZ is actively tracking this mode of delivery and malware families involved to ensure coverage for Zscaler customers.




