Everywhere security for your anywhere data
Cloud, AI, and mobility demand a dynamic, modern approach to data security. Move beyond complex DLP solutions and point products to a unified platform that provides everything you need for airtight protection, all in one place.
Full visibility of data, everywhere
Proactive mitigation of open risks
Real-time, inline DLP across all channels
The Problem
Dynamic data flows and rising demands on productivity have led to a patchwork of security measures. However, traditional data security wasn’t designed for AI, multicloud environments, and distributed data, leaving organizations with:
- Disjointed approaches to classification and DLP
- Complex administration and maintenance
- Brittle architectures that impact IT agility
- Costly hardware refreshes and operations
Solution Overview
The most complete platform for data security
Zscaler Data Security unifies groundbreaking classification and proactive data security posture management (DSPM) with the world's most trusted inline DLP proxy.
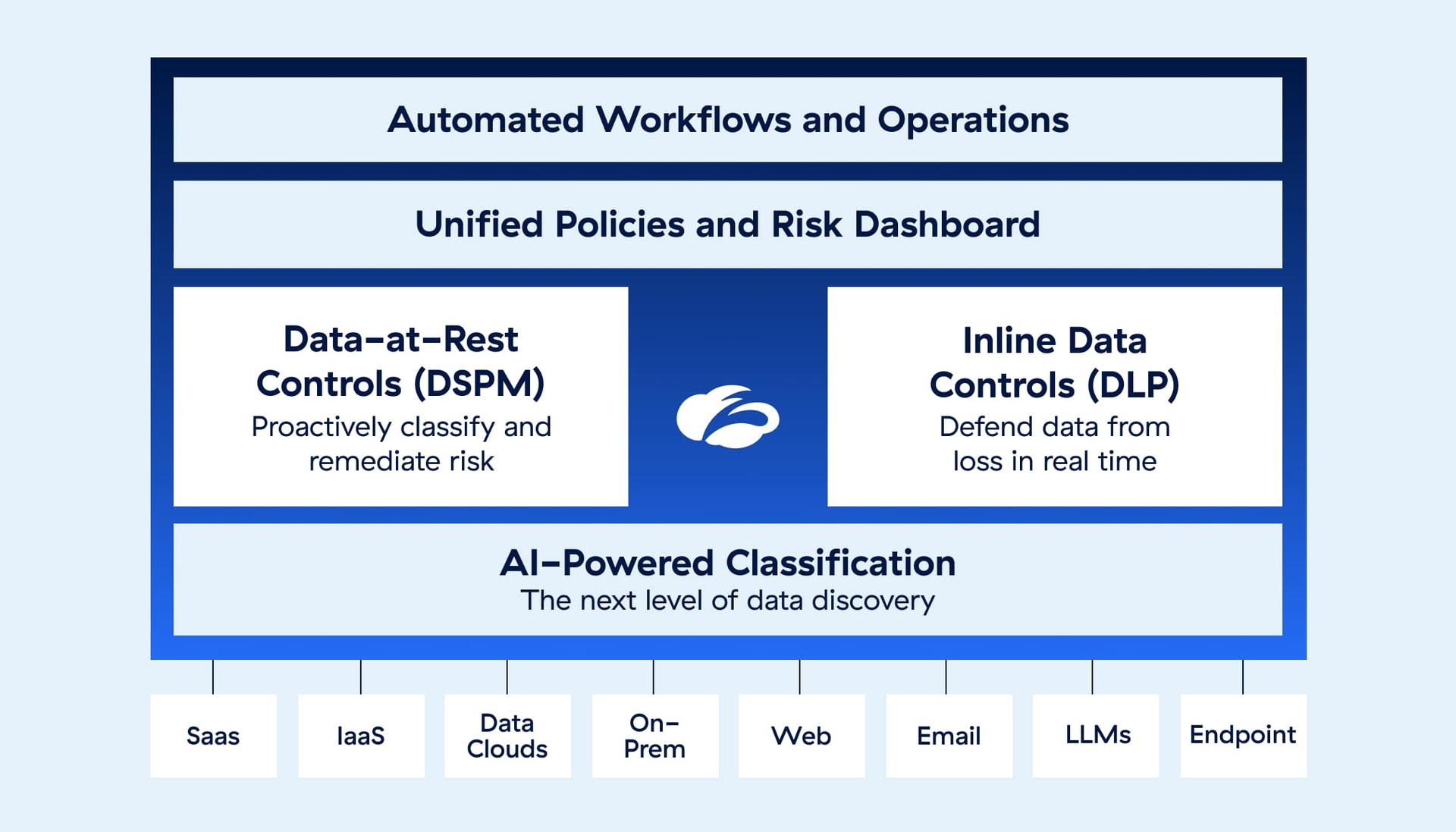
Benefits
One platform with all-in-one innovation

With a unified cloud platform and single agent, easily scale high-performance DLP everywhere: web, GenAI, endpoints, email, SaaS, and IaaS. Enjoy unlimited TLS/SSL inspection while minimizing endpoint agents—no complex administration, patching, or hardware required.

See AI usage and prompts, block risky access, and enforce prompt DLP or isolation to prevent data loss. Even manage Microsoft Copilot oversharing with bulk updating of OneDrive permissions and label updates.

Use innovative LLM Classification to read content in real time and understand sensitivity—without keyword requirements—for smarter, faster protection. Paired with EDM, IDM, OCR, and Regex, you’re ready to outsmart data risks.

Discover where your data lives and the risks hiding in plain sight. Leverage a powerful approach to classification and risk mitigation that closes misconfigurations and integrates thoughtfully into a larger platform.

Take a hands-off approach to operations with Workflow Automation. Get full visibility of DLP incidents while creating automated workflows for user justification requests, training, or escalations.
Curious to See Zscaler in Action?
Try our Interactive Demo Center to see how easy it is to protect data everywhere with Zscaler’s unified interface.
Key Platform Offerings
Discover the Zscaler Data Security approach
Modernize your data security
Consolidate point products into one platform that cuts costs and complexity.

Key factors
Deliver high-performance DLP inspection across web and email data.
Secure custom data, documents, and screenshots with advanced classification techniques.
Streamline operations with automated incident management and user coaching.
Enable safe use of GenAI
Ensure your data remains safe while supporting productive GenAI workflows.

Key factors
See shadow AI and prompts while protecting sensitive data with inline controls, DLP, and browser isolation.
Control risky oversharing to Copilot with advanced control over OneDrive permissions and labels.
Enhance your data security posture
Mitigate risks by mapping data and closing misconfigurations.

Key factors
Govern and secure public clouds and sensitive data with integrated DSPM.
Govern and secure sharing, posture, integrations, and misconfigurations.














































































our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
FAQ
Data security posture management (DSPM) finds, classifies, and protects sensitive data across on-premises and cloud environments. It uses continuous monitoring and automation to spot gaps, rank risk, and fix issues like misconfigurations or excessive permissions. It also validates controls with access mapping, risk correlation, and audit evidence to streamline compliance and remediation.
Data loss prevention (DLP) is vital to secure access service edge (SASE) because it makes SASE data-aware. It discovers, classifies, and controls sensitive data across web, SaaS, cloud, and endpoints, even in encrypted traffic. With one set of policies, DLP helps stop exfiltration, risky sharing, and BYOD leaks while supporting compliance.
Unified DLP strengthens compliance by making one set of data controls work everywhere—web, SaaS, cloud, and endpoints. It continuously discovers and classifies sensitive data, its location, and who can access it, and enforces policies to block risky sharing and shadow IT leaks. By mapping to the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), PCI DSS, and more, it can detect risks and support rapid remediation. Centralized visibility and audit-ready reports cut blind spots and speed audits across multi-cloud deployments.











