Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Microsoft, Midnight Blizzard, and the Scourge of Identity Attacks
Summary
On January 19, 2024, technology leader Microsoft disclosed that it had fallen victim to a Russian state-sponsored cyberattack that gave the threat actors access to senior management mailboxes and resulted in sensitive data leakage.
While we will break down the attack step-by-step and explain what organizations can do to defend against similar attacks below, here’s a TL;DR.
The threat actor
- Midnight Blizzard: State-sponsored Russian threat actor also known as Nobelium, CozyBear, and APT 29
- Notable Midnight Blizzard breaches: Hewlett Packard Enterprise (December 12, 2023) and SolarWinds (December 14, 2020)
The facts
- Attack target: Microsoft’s Entra ID environment
- Techniques used: Password spraying, exploiting identity and SaaS misconfigurations
- Impact: Compromised Entra ID environment, unauthorized access to email accounts of Microsoft’s senior leadership team, security team, legal, and more
What’s unique about the attack?
- Using stealthy identity tactics that bypasses existing defenses to compromise users
- Exploiting misconfigurations in SaaS applications to gain privileges
- Exploiting identity misconfigurations in Entra ID to escalate privileges
The attack sequence
- Found a legacy, non-production test tenant in Microsoft’s environment.
- Used password spraying via residential proxies to attack the test app tenant.
- Limited the number of attack attempts to stay under the threshold and evade blocking triggered by brute forcing heuristics.
- Guessed the right password and compromised the test tenant’s account.
- Generated a new secret key for the Test App that allowed the threat actor to control the app every where it was installed.
- Test App was also present in the corporate tenant. Threat actor used the app’s permissions to create an admin user in the corporate tenant.
- Used the new admin account to create malicious OAuth apps.
- Granted the malicious app the privilege to impersonate the users of the Exchange service.
- Used the malicious app to access Microsoft employee email accounts.
Microsoft’s official guidance
Defend against malicious OAuth applications
- Audit privileged identities and apps in your tenant
- Identify malicious OAuth apps
- Implement conditional access app control for unmanaged devices
Protect against password spray attacks
- Eliminate insecure passwords
- Detect, investigate, and remediate identity-based attacks
- Enforce multi factor authentication and password protections
- Investigate any possible password spray activity
Zscaler’s guidance
- Continuously assess SaaS applications for misconfigurations, excessive permissions, and malicious changes that open up attack paths.
- Continuously assess Active Directory and Entra ID (previously known as Azure AD) for misconfigurations, excessive permissions, and malicious changes that open up attack paths.
- Monitor users with risky permissions and misconfigurations for malicious activity like DCSync, DCShadow, kerberoasting, etc. that is typically associated with an identity attack.
- Implement containment and response rules to block app access, isolate the user, or quarantine the endpoint on an identity attack detection.
- Implement deception to detect password spraying, Entra ID exploitation, Active Directory exploitation, privilege escalation, and lateral movement for instances where stealthy attacks bypass existing detection and monitoring controls.
Deconstructing the attack
The threat actor Midnight Blizzard has had a long history of pulling off highly publicized breaches. It’s Microsoft this time around, but in the past, they’ve allegedly compromised Hewlett Packard Enterprise and SolarWinds. To people who analyze attacks for a living, the Microsoft breach should not come as a surprise.
Midnight Blizzard is among a growing list of nation-state and organized threat actors that rely on identity compromise and exploiting misconfigurations/permissions in SaaS applications and identity stores to execute breaches that conventional security thinking cannot defend against.
Other threat groups using these strategies and techniques include Evil Corp, Lapsus$, BlackMatter, and Vice Society.
In case of the Microsoft breach, the attackers demonstrated a profound understanding of OAuth mechanics and attack techniques to evade detection controls. They created malicious applications to navigate Microsoft's corporate environment. And by manipulating the OAuth permissions, they granted themselves full access to Office 365 Exchange mailboxes, enabling them to easily exfiltrate sensitive emails.
Security challenges
- Identity-centric tactics: Midnight Blizzard strategically targeted identities, exploiting the user's credentials as a gateway to sensitive data. Conventional detection controls like EDRs are not effective against such attacks.
- OAuth application abuse: The adversaries adeptly abused OAuth applications, a technique that complicates detection and enables prolonged persistence.
- Misconfiguration blind spots: Identifying misconfigurations within Active Directory/Entra ID and SaaS environments remains a complex task, often resulting in blind spots for defenders.
Step-by-step breakdown
Pre-breach
Before the attack commenced, an admin within Microsoft's test tenant had created an OAuth app. For the purpose of this blog post, let’s call this app ‘TestApp.’
For reasons unknown, this app was subsequently installed in Microsoft's corporate environment with elevated permissions, likely encompassing the scope Directory.ReadWrite.all, granting it the capability to create users and assign roles. Notably, this app appeared to be dormant and possibly forgotten.
ThreatLabz note: There is an unimaginable sprawl of applications, users, and associated misconfiguration and permissions that security teams often have no visibility into. More often than not, blind spots like these are what result in publicized breaches.
Initial access
In late November 2023, Midnight Blizzard initiated reconnaissance on Microsoft's SaaS environment. Discovering the test tenant, the attacker targeted its admin account, which, being a test account, had a weak, guessable password and lacked multi-factor authentication (MFA). Employing a password spraying attack, the attacker systematically attempted common passwords to gain access, leveraging residential proxies to obfuscate their origin and minimize suspicion. Eventually, the attacker successfully compromised the admin account.
ThreatLabz note: Traditional threat detection and monitoring controls are ineffective against attacks that use valid credentials, MFA-prompt bombing, and other identity-centric techniques to compromise users.
Persistence
With control over the admin account, the attacker obtained the ability to generate a new secret key for TestApp, effectively commandeering it across all installations. This tactic mirrors techniques observed in the SolarWinds attack of 2020.
ThreatLabz note: In the absence of continuous monitoring and high-confidence alerting for malicious changes being made to permissions in SaaS applications, attacks like these easily cross the initial access phase of the kill chain.
Privilege escalation
Given TestApp's permissions within Microsoft's corporate tenant, the attacker created a new user, likely an administrator, to further their access. Subsequently, the attacker deployed additional malicious OAuth apps within the tenant to evade detection and ensure persistence, leveraging TestApp to grant elevated roles, such as Exchange role EWS.full_access_as_app, facilitating mailbox access and bypassing MFA protection.
ThreatLabz note: Configuration and permission based blindspots extend to identities themselves. As such, it is imperative that organizations have the ability to continuously assess their Active Directory/Entra ID for misconfigurations, excessively permissive policies, and other permissions that give attackers the ability to escalate privileges from a compromised identity. They should also continuously monitor for malicious changes in the identity store that might potentially be creating additional attack surfaces.
Lateral movement
Though specifics regarding the number and origin of installed apps remain unclear, the attacker's utilization of TestApp to confer privileges is evident. This culminated in unauthorized access to mailboxes belonging to Microsoft's senior leadership, security personnel, legal team, and other stakeholders.
How zero trust can help
A zero trust architecture provides a fundamentally secure approach that is better at protecting against stealthy attacks that are used by nation-state threat actors and organized adversaries.
Zero trust fundamentally eliminates weaknesses in your environment that are core properties of hub and spoke network models.
Below is a 10,000 foot reference architecture for zero trust that explains how and why it better protects against Midnight Blizzard-style attacks.
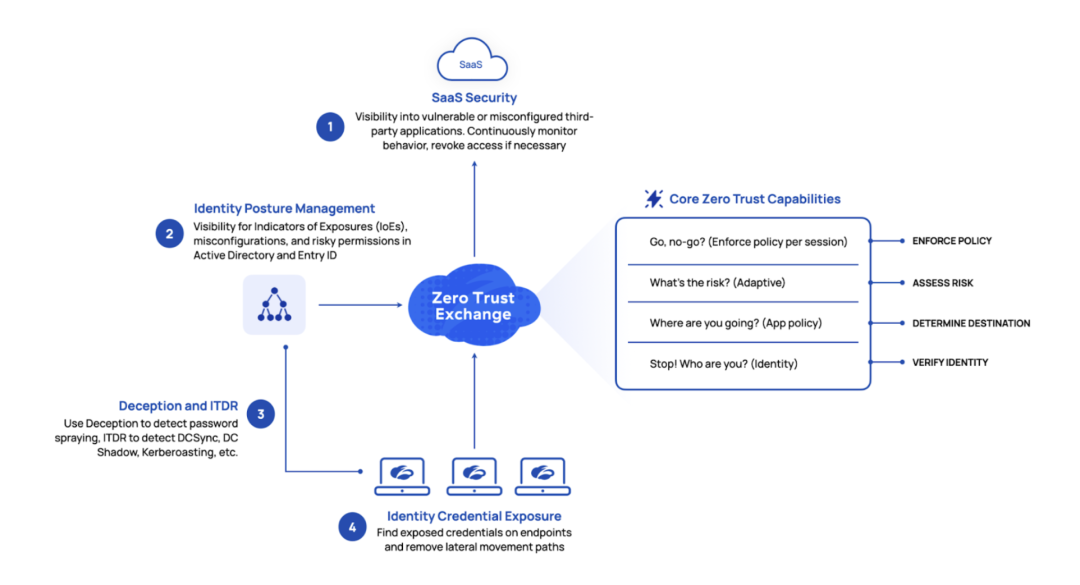
Core zero trust capabilities
This is the heart of a zero trust architecture consisting of Internet Access and Private Access. The Zero Trust Exchange acts as a switchboard brokering all connections between users and applications. This architecture makes your applications invisible to the Internet, thereby eliminating the external attack surface, replaces high-risk VPNs, and uses segmentation to reduce lateral threat movement and internal blast radius. To broker the connection, the Zero Trust Exchange verifies the identity, determines the destination, assesses risk, and enforces policy.
ThreatLabz note: Zscaler extends core zero trust capabilities with SaaS supply chain security, Identity Posture Management, ITDR, Deception, and Identity Credential Exposure to eliminate application and identity misconfigurations, detect stealthy attacks, and provide visibility into exposed credentials on endpoints to remove lateral movement paths. Below, we breakdown what each of these capabilities can do.
SaaS Security
While the move to the cloud and SaaS applications has aided organizations to accelerate their digital transformation, it has also created a new set of security challenges. Among these, the lack of visibility into dangerous backdoor connections to SaaS applications is paramount as it creates supply chain risk — the kind that was exploited in the Microsoft breach.
SaaS Security strengthens your security posture by providing visibility into third-party application connections, over-privileged access, risky permissions, and continuous monitoring for changes that can be malicious in nature. It is a core step in securing your SaaS environment.
Identity Posture Management
Nine in ten organizations are exposed to Active Directory attacks and there has been a 583% increase in Kerberoasting and similar identity attack techniques in 2023 alone. These are not isolated phenomena. Misconfigurations and excessive permissions in Active Directory and other identity providers are what enable these types of attacks. For example, an unprivileged account without MFA having the ability to control an application with privileged roles should be flagged, but most security teams do not have appropriate visibility into these types of misconfigurations.
Identity Posture Management augments zero trust by providing security teams visibility into identity misconfigurations, policies, and permissions that open up potential attack paths. With periodic assessments, security teams can leverage remediation guidance to revoke permissions, limit policies, and remove misconfigurations. Identity Posture Management also alerts security teams to malicious changes in the Active Directory in real time.
Deception and ITDR (Identity Threat Detection and Response)
As evidenced in the Microsoft breach, attackers used password spraying from a residential proxy and limited the number of tries to evade detection. Traditional threat detection and monitoring approaches just do not work here. Deception, on the other hand, is a pragmatic approach that can detect these attacks with fairly high confidence. Decoy users created in Entra ID can detect such password spraying attacks without false positives or the need to write complex detection rules.
ITDR can detect identity-specific attacks like DCSync, DCShadow, and Kerberoasting that would otherwise require detection engineering and significant triage to spot.
Identity Credential Exposure
While TTPs (Techniques, Tactics, and Procedures) were not reported for credential exploitation, credentials and other sensitive material (like username, passwords, authentication tokens, connection strings, etc.) on the endpoint in files, registry, and other caches are something that threat actors like Volt Typhoon, Scattered Spider, BlackBasta, BlackCat, and LockBit are known to have exploited in publicly reported breaches.
Identity Credential Exposure provides security teams with visibility into credential exposure across their endpoint footprint, highlighting blind spots that open up lateral movement and data access paths from the endpoint.
Zero trust creates multiple opportunities to detect and stop Midnight Blizzard-style attacks
| Problem | Solution | How does it work? | MITRE ATT&CK Technique |
| Password spraying | Zscaler Deception | Decoy user accounts in Entra ID can detect any attempts to sign in using the credentials of the decoy users. Any failed/successful attempts will be logged to detect attacks like password spraying | |
| Existence of apps/SPNs with high privilege | Zscaler ITDR | ITDR can surface unprivileged accounts that have a path (e.g., owner rights) to apps with privileged roles | NA |
| Creation of apps/SPNs with high privilege | Zscaler SaaS Security | Monitoring for and alerting when a risky app is added, app is created by an unverified publisher, and when an app hasn’t been used in a while | There is no technique that maps to this but in terms of the nature of the technique, the ones listed below are a close approximation of how you think of the attack. |
| Creation/modification of users with high privileges | Zscaler ITDR | Monitoring of an alerting on unauthorized addition of privileged permissions to principals | |
| Secret addition to apps | Zscaler SaaS Security | Flags applications with multiple Application Secrets | T1098.001 - Account Manipulation: Additional Cloud Credentials |
| Disabled MFA | Zscaler ITDR | Find accounts where MFA is disabled and get alerts when MFA is disabled for any account | T1556.006 - Modify Authentication Process: Multi-Factor Authentication |
| Consent grants | Zscaler SaaS Security | Monitors inclusion of high risk scopes like EWS.full_access_as_app or EWS.AccessAsUser.All to alert on the app’s risk level | T1098.003 - Account Manipulation: Additional Cloud Roles T1098.002 - Account Manipulation: Additional Email Delegate Permissions |
What should I do next?
- Identity is the weakest link. Irrespective of whether you are running a zero trust architecture or not, start by getting visibility into identity misconfigurations and excessive permissions that can allow attackers to grant themselves privileges. We’re offering a complimentary Identity Posture Assessment with Zscaler ITDR.
- Gain visibility into your SaaS sprawl and find dangerous backdoor connections that can give attackers the ability to establish persistence. Request an assessment with Zscaler SaaS Security.
- Implement Deception irrespective of what other threat detection measures you have. It is one of the highest ROI threat detection controls that you can implement, augmenting controls like EDR. Zscaler Deception has a comprehensive set of decoys that can deceive and detect sophisticated attackers.
If you are a Zscaler customer, contact your account manager for support on these assessments and Deception rollout.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



