One month after the WannaCry outbreak, we have seen another widespread ransomware outbreak, possibly involving the Petya ransomware family variant. The initial vector has been confirmed to be a compromised software update package from MeDoc. As we learn more, we will continue to update our blog.
- Businesses from several countries, including Ukraine, India, France, Russia, and Spain, have been impacted by this ransomware outbreak
- The malware family involved is purported to be a variant of the Petya ransomware family; however, from our analysis up to this point, we are seeing very little resemblance between this code and previous Petya variants
- This ransomware variant is highly virulent and, once it infects a user, it spreads rapidly across a corporate network via SMB
- There are reports of the payload using the EternalBlue (MS17-010) exploit when it is not able to spread through a network using the credentials of the logged-in user
- The ransomware payload encrypts the Master Boot Record (MBR) of an infected system, making it unusable
- The ransomware payload is also using the Windows Management Instrumentation Command-line (WMIC) interface for lateral movement over SMB. This explains why the attack has been successful more than a month after the WannaCry outbreak that leveraged the EternalBlue (MS17-010) exploit, which should have been patched on most systems by now
Protective Actions
- Apply Microsoft Windows security update MS17-010 and CVE-2017-0199
- Block legacy protocols like SMBv1 on your local network
- Disable WMIC on your local network
- Block connection to ports 135, 139, and 445 on your firewall
How Zscaler Can Help with Preventative Measures
Zscaler had generic signature coverage on one of the payloads involved and added multiple signatures and indicators for blocking other known payloads related to this attack.
Advanced Threat Signatures:
- Win32_ransomware_Petya_116628
- CVE_2017_0199
Inline AV Signatures:
- W32/Petya.VUNZ-1981
- W32/Ransom.Petya.J!Eldorado
Zscaler Cloud Sandbox provides the best line of proactive defense against these evolving ransomware strains. A Cloud Sandbox report for a sample payload run is shown below:
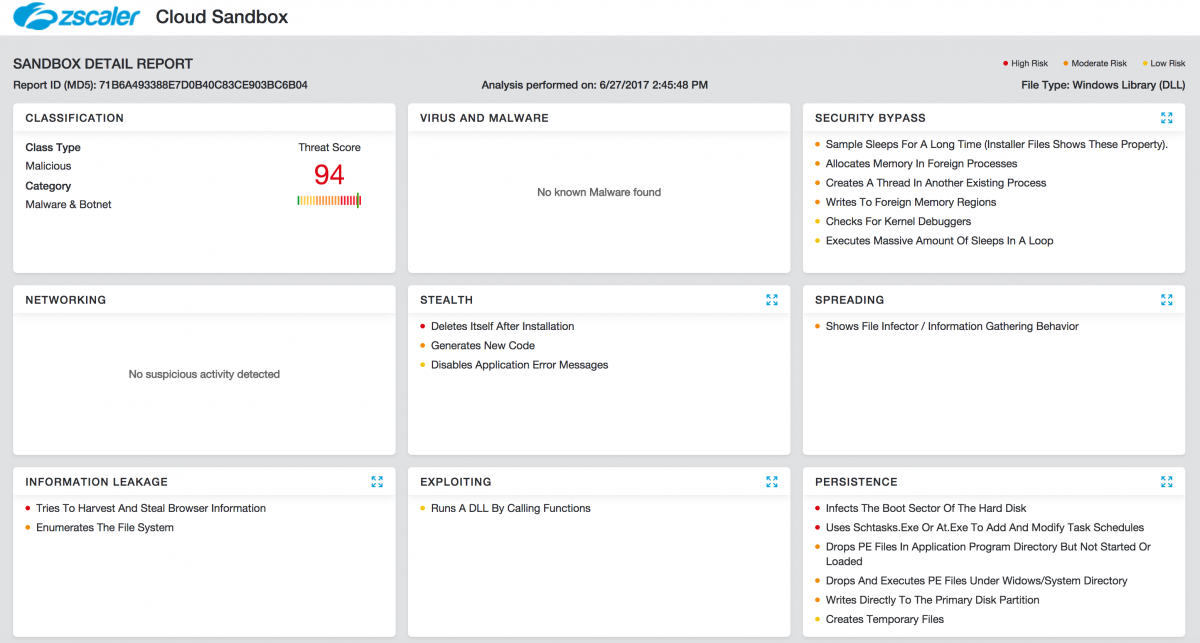
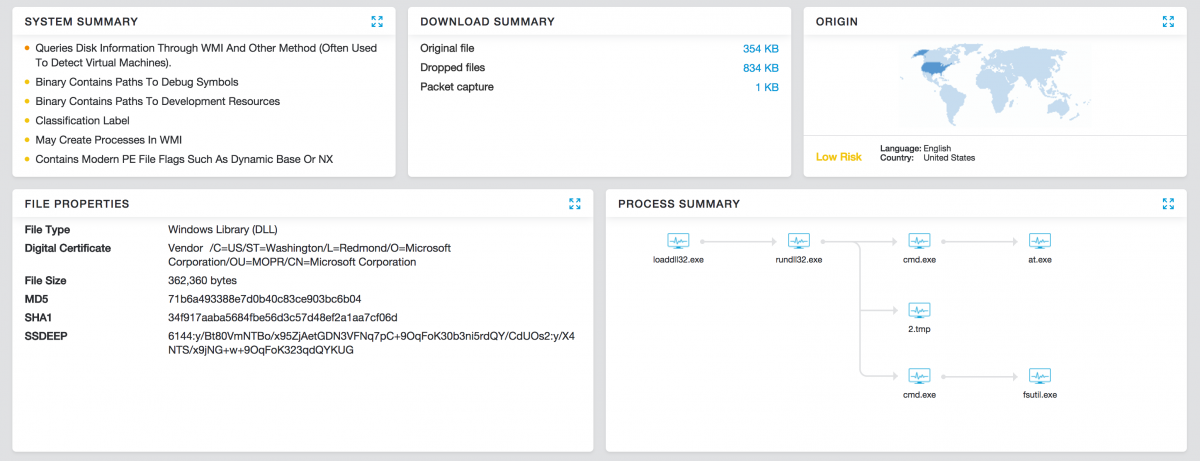
Figure 1: Zscaler Cloud Sandbox report of Petya ransomware
Initial Delivery Vector
The initial infection vector was via a compromised custom software update package delivered over HTTP from MeDoc. The ransomware has a worm component that uses the Windows Management Instrumentation Command-line (WMIC) interface and the MS17-010 (EternalBlue and EternalRomance) exploits to propagate laterally over SMB.
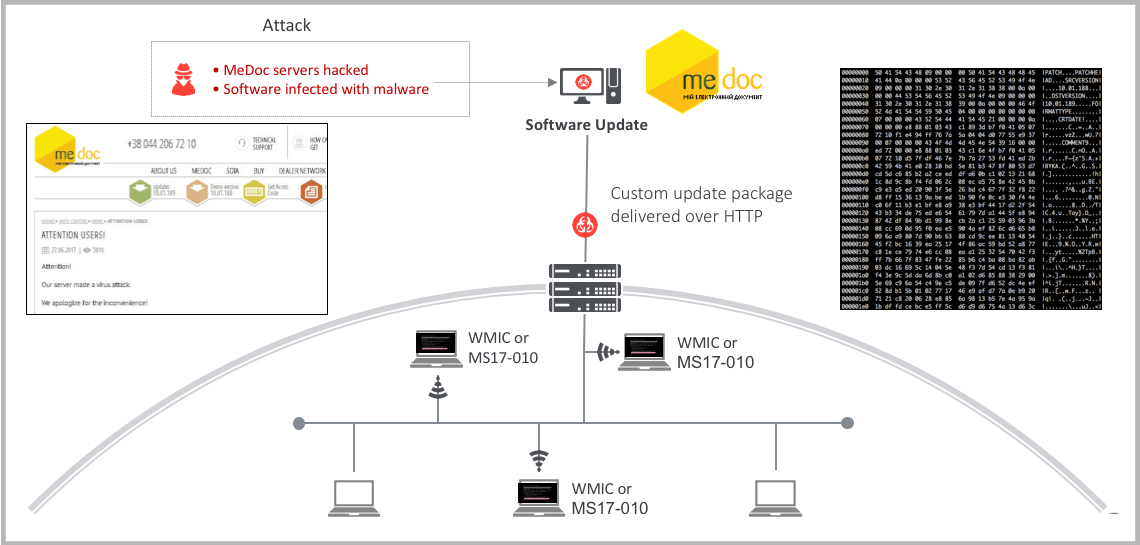
Figure 2: Initial infection and propagation
Technical Analysis of the Payload
We analyzed two unique payloads from this attack, both of which were Windows Dynamic-Link Library (DLL) files. These DLLs have an export function without a name; it is invoked using the ordinal value “#1” as shown below:
\rundll32.exe "%s",#1
It is also important to note that these files were recently compiled as shown in the screenshot below:
Figure 3: Recently compiled DLL payload
Once executed, the ransomware payload will perform the following activity on the victim's machine:
- There is a check in the ransomware routine to look for an infection marker, which, if found, will terminate the execution. This essentially serves as a killswitch for the ransomware payload, preventing further propagation within the network:
Infection Marker or Killswitch file => C:\Windows\MalwareDLLFileName where MalwareDLLFileName is the name of main DLL
-
The malware looks for files with following extension on the user machine and encrypts them:
.3ds.7z.accdb.ai.asp.aspx.avhd.back.bak.c.cfg.conf.cpp.cs.ctl.dbf.disk.djvu.doc.docx.dwg.eml.fdb.gz.h.hdd.kdbx.mail.mdb.msg.nrg.ora
The encrypted files will have same extension as before.
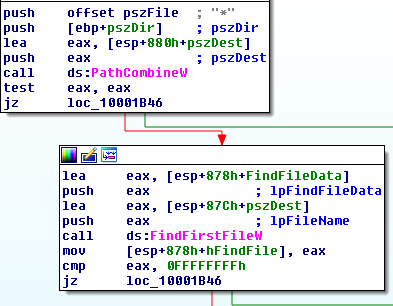
Figure 4: Enumerating files for encryption
- If the user is logged in with administrator privileges, the malware payload will also encrypt the Master Boot Record (MBR) and essentially make the system unusable upon system reboot
-
The malware then creates a scheduled task to reboot the infected system as seen below:
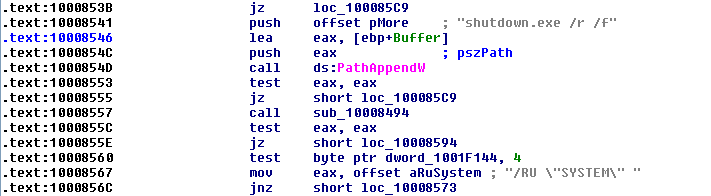
Figure 5: Scheduled task to reboot the system in one hour
- Once the system reboots, the infamous ransom note appears, demanding $300 in Bitcoins
Figure 6: Ransom note
-
The delay in rebooting the compromised system and showing the ransom note is probably done to provide a complete hour for the spreading module to propagate laterally in the network without any indication to the end user
-
We are still analyzing the propagation module but as previously reported, there is a new propagation vector involving WMIC which is possibly the reason this attack has been successful
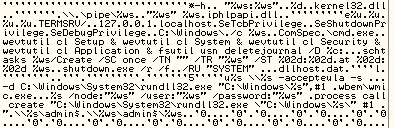
Figure 7: Leveraging WMIC for lateral movement
-
We did not observe any network C&C activity associated with these samples
Conclusion
WannaCry started a new era of ransomware variants weaponized with a mechanism for lateral movement. Petya authors went one step further by adding the WMI interface vector and we expect to see more variants in the coming months. This attack shows the importance of a multilayered security approach, and it highlights the gap that exists in applying security patches and securing internal systems (via network segmentation).
Zscaler ThreatLabZ is actively monitoring this threat and will continue to ensure coverage for Zscaler customers.
Indicators of Compromise
DLLs
- E285B6CE047015943E685E6638BD837E
- 71B6A493388E7D0B40C83CE903BC6B04
Research by ThreatLabZ team







